Doctor Web examines multi-component Trojan for Linux
Real-time threat news | Hot news | All the news | Virus alerts
May 25, 2017
Doctor Web security researchers registered the first attacks of this Trojan from the Linux.LuaBot family in December 2016. All versions of this Trojan are written in the script language Lua. Since November 2016, the Trojan has been constantly evolving, and new versions of Linux.LuaBot appear on a regular basis. Linux.LuaBot is a set of 31 Lua scripts and two additional modules, each of which performs its own functions. The Trojan infects devices possessing the following architectures: Intel x86 (and Intel x86_64), MIPS, MIPSEL, Power PC, ARM, SPARC, SH4, and M68k—in other words, not only computers, but also a wide array of routers, set-top boxes, network storages, IP cameras and other “smart” devices. Note that Doctor Web’s specialists were unable to detect in-the-wild samples of the Trojan built for the SPARC architecture: the infecting Trojan can detect SPARC, but no real, existing modules have been found for it.
All the scripts included in Linux.LuaBot are interdependent. The Trojan generates a list of IP addresses to attack and then attempts to connect to remote devices via this list and sign in by brute-force login using a special vocabulary. The scripts used by the Trojan to hack network nodes know how to determine the architecture of an attacked device and, moreover, have a special mechanism for detecting “honeypots”—decoy servers used to deceive cybercriminals. Digital security researchers use “honeypots” to examine attack methods and cybercriminal techniques. In addition, the attacks are performed via the Telnet and SSH protocols—a separate Lua script is responsible for the operation of these protocols. If access to a device is obtained, the malicious script installs the corresponding Linux.LuaBot architecture on it. In the course of an attack via the Telnet protocol, the compromised device is loaded with a small module, which upon launch downloads the actual Trojan. When a device is attacked via the SSH protocol, the Trojan is loaded immediately.
One of the Linux.LuaBot modules is a fully functional web server that operates via the HTTP protocol. The server can save an application on the infected device and launch it, transmit a file from its directory upon request, and share information about the version of the Trojan. It is notable that the May version of Linux.LuaBot lost the function to transmit data about the devices it has infected.
Linux.LuaBot communicates with a command and control (C&C) server via the HTTP protocol, and all the information it transmits is encrypted. A P2P network based on the Bittorent DHT protocol, the same protocol used in ordinary torrent networks, is used to search for new configuration files and modules. Yet another script is responsible for this function. In addition, a digital signature is used to verify the authenticity of received and sent messages. If a P2P network is unavailable, a separate script uses other infected nodes to update Linux.LuaBot by downloading its files to compromised devices according to special request. This script was used only in early versions of the Trojan.
The danger of Linux.LuaBot for owners of Linux devices centers around the fact that this Trojan is in fact a backdoor; in other words it executes commands issued by cybercriminals. In addition, earlier versions of this malicious program launched a proxy server on the devices it compromised. Cybercriminals used this server to anonymize their online activities.
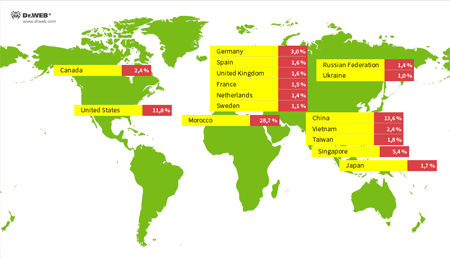
Doctor Web’s specialists have collected statistics on the unique IP addresses of devices infected with Linux.LuaBot. The image below provides information about the geographic distribution of these addresses.
Doctor Web security researchers are familiar with several modifications of Linux.LuaBot, which differ in terms of their set of functions and architectural features. Dr.Web Anti-virus detects all currently existing samples of Linux.LuaBot.