Doctor Web discovers Trojans in firmware of well-known Android mobile devices
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
December 12, 2016
One of these Trojans, dubbed Android.DownLoader.473.origin, was found in firmwares of a large number of popular Android devices operating on the MTK platform. At the time this news article went to posted, the Trojan was detected on the following 26 models of smartphones:
- MegaFon Login 4 LTE
- Irbis TZ85
- Irbis TX97
- Irbis TZ43
- Bravis NB85
- Bravis NB105
- SUPRA M72KG
- SUPRA M729G
- SUPRA V2N10
- Pixus Touch 7.85 3G
- Itell K3300
- General Satellite GS700
- Digma Plane 9.7 3G
- Nomi C07000
- Prestigio MultiPad Wize 3021 3G
- Prestigio MultiPad PMT5001 3G
- Optima 10.1 3G TT1040MG
- Marshal ME-711
- 7 MID
- Explay Imperium 8
- Perfeo 9032_3G
- Ritmix RMD-1121
- Oysters T72HM 3G
- Irbis tz70
- Irbis tz56
- Jeka JK103
However, the number of infected Android devices can be, in fact, even bigger.
Android.DownLoader.473.origin is a downloader Trojan which starts its activity every time a device is turned on. The malware program monitors the Wi-Fi module and then connects to the command and control (C&C) server in order to get the configuration file with instructions. The file contains information about the application the Trojan should download. After the program is downloaded, Android.DownLoader.473.origin covertly installs it.
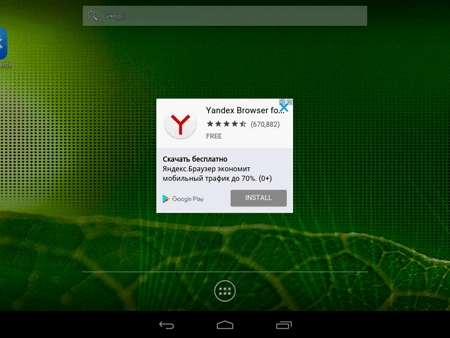
The Trojan can download not only benign applications but also malware and unwanted ones. For example, Android.DownLoader.473.origin actively distributes the advertising program H5GameCenter that is detected by Dr.Web as Adware.AdBox.1.origin. Once installed, it displays a small box image on top of running applications. The image cannot be removed from the screen. It is a shortcut clicking on which opens a catalog integrated into Adware.AdBox.1.origin. In addition, the Trojan shows advertisements.
On various forums, Android users note that even if they delete H5GameCenter, it is soon installed on the system once again. It happens because Android.DownLoader.473.origin again downloads and installs Adware.AdBox.1.origin if the program has been deleted.
Another Trojan found on the devices Lenovo A319 and Lenovo A6000 was named Android.Sprovider.7. The Trojan is incorporated into the application Rambla which provides access to the Android software catalog named the same.
The payload of Android.Sprovider.7 is located in a separate program module (which is detected as Android.Sprovider.12.origin). It is encrypted and stored in resources of the main malware program. When a user unlocks the home screen, the Trojan checks whether the module is still active. If not, Android.Sprovider.7 retrieves this component from its body and runs it. The module Android.Sprovider.12.origin can execute the following functions:
- Download an APK file and try to install it by obtaining the confirmation from a user.
- Run an installed application.
- Open the specified link in a browser.
- Make a phone call on a certain number by using a standard system application.
- Run a standard system phone application in which a specified number is already dialed.
- Show advertisement on top of all applications.
- Display advertisements in the status bar.
- Create a shortcut on the home screen.
- Update a main malicious module.
It is known that cybercriminals generate their income by increasing application download statistics and by distributing advertising software. Therefore, Android.DownLoader.473.origin and Android.Sprovider.7 were incorporated into Android firmware because dishonest outsourcers who took part in creation of Android system images decided to make money on users.
Doctor Web has already informed smartphone manufacturers about this incident. Users of the infected devices are recommended to contact technical support specialists to get the updated system software as soon as it is ready.
Dr.Web for Android detects Android.DownLoader.473.origin and Android.Sprovider.7 so that our users can check whether the firmware is infected.