Doctor Web discovers Trojan targeting construction cranes
Real-time threat news | Hot news | All the news | Virus alerts
November 17, 2016
BackDoor.Crane.1, a Trojan for Windows, was used to attack Russia’s two largest manufacturers of portal cranes and lifting cranes, as well as auxiliary equipment. This is one of the few cases involving malware being used to engage in targeted attacks that Doctor Web’s specialists have registered in the recent past. The backdoor Trojan and the two other malware programs it has been downloading on infected machines have been stealing confidential information for some time. The cybercriminals involved were interested in obtaining financial documentation, agreements, and internal business correspondence. In addition, these Trojans periodically made screenshots and sent them to the command and control (C&C) server. We tend to think that those attacks were carried out by unscrupulous rivals.
Now we will briefly focus on some technical features of BackDoor.Crane.1.
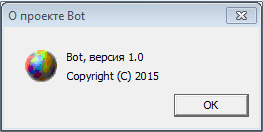
The Trojan’s resources contain the window “About the Bot project” which is not displayed while the backdoor is in operation—the virus makers probably forgot to remove it when they copied the code. The window has the string “Copyright © 2015”; however, the current version was compiled on April 21, 2016.
Once launched, the Trojan checks whether the configuration file is present; if not, it creates one. BackDoor.Crane.1 then loads its modules into the computer’s memory and starts periodically requesting instructions from the C&C server. It should be noted that, when interacting with the C&C server, the Trojan uses the string “RSDN HTTP” as a value for the parameter User-Agent. Therefore, Doctor Web’s specialists have concluded that the attackers copied some code fragments from a website for software developers—rsdn.org.
BackDoor.Crane.1 has several modules that can be installed on the command of cybercriminals. Each of them executes a specific function, for example:
- A received command can be executed using the command interpreter cmd;
- A file can be downloaded from a specified link and saved to a certain folder on a computer;
- A list of folder content can be generated and sent to the C&C server;
- A screenshot can be taken and sent to the C&C server;
- A file can be loaded to a specified server over the FTP protocol;
- A file can be loaded to a specified server over the HTTP protocol.
Doctor Web specialists have determined that some of BackDoor.Crane.1’s modules downloaded and installed two other Trojans written in the Python language. The Trojans were added to the Dr.Web virus databases under the names Python.BackDoor.Crane.1 and Python.BackDoor.Crane.2. Python.BackDoor.Crane.1 shares information with the C&C server over the HTTP protocol and can execute almost the same commands. However, some new instructions were added to the command list:
- Get a list of files and folders using the specified path;
- Delete particular files;
- Shut down certain processes;
- Copy the specified files;
- Send a list of running processes and information on the current operating system and disks of the infected computer the C&C server;
- Terminate itself.
The second Trojan—Python.BackDoor.Crane.2—is designed to execute the shell code, received from cybercriminals, on an infected computer.
The signatures for these Trojans are already in the Dr.Web databases and do not pose any threat to our users.