September 27, 2016
This malicious program (dubbed Linux.Mirai) first appeared in May 2016 and was added to the Doctor Web virus database under the name Linux.DDoS.87. This Trojan, designed to carry out DDoS attacks, can work with the SPARC, ARM, MIPS, SH-4, M68K architectures and Intel x86 computers.
Linux.DDoS.87 code had numerous flaws which were eliminated in later versions of the Trojan. It also shares a few features with the Linux.BackDoor.Fgt family, one of whose representatives we described in November 2014. Once launched on an infected computer, Linux.DDoS.87 searches the memory for the processes of other Trojans and terminates them. To avoid being terminated itself, the Trojan creates a file named .shinigami in its folder and periodically verifies its presence. Then Linux.DDoS.87 attempts to connect to its command and control server for further instructions. It sends the server the identifier that defines the infected computer’s architecture and the MAC address of the network card.
Linux.DDoS.87 can launch the following DDoS attacks when directed to do so by cybercriminals:
- UDP flood;
- UDP flood over GRE;
- DNS flood;
- TCP flood (several types);
- HTTP flood.
The maximum uptime of Linux.DDoS.87 on an infected computer is one week, after which the Trojan terminates its operation.
August 2016 began with the discovery of a new version of this dangerous Trojan. The new version, dubbed Linux.DDoS.89, shares many of its predecessor’s features, although there are some notable differences from Linux.DDoS.87. For example, the newer version has another procedure for launching the Trojan. The mechanism for protecting its own process from being unloaded has also changed: now the malicious program makes no attempt to verify whether a special file is present in a specific folder; instead it uses a process identifier (PID) for that. Linux.DDoS.89 no longer sends the MAC address of the network card to the command and control server. Moreover, HTTP flood attacks are no longer carried out. However, the format of the commands received from cybercriminals has not changed. Finally, Linux.DDoS.89 includes a new component—the telnet scanner that was used previously in all modifications of Linux.BackDoor.Fgt. This scanner is designed to search for vulnerable computers on the Internet and connect to them using the telnet protocol.
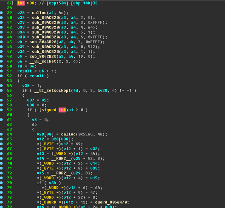
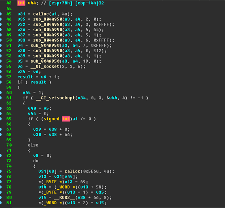
September began with the discovery of an updated version of the Trojan dubbed Linux.Mirai. Some samples of this malicious program now have a self-removal function. The Trojan has learned how to turn off the watchdog timer (which protects against system hangs and reboots), and once again it is carrying out HTTP flood attacks. Nonetheless, Linux.Mirai and its predecessors are very similar. The illustration below lets you compare Linux.DDoS.87 (left) and Linux.Mirai (right) code fragments.
Some researchers have reported that if Linux.Mirai finds a vulnerable telnet device, it executes a bash script embedded in it. Such behavior is typical of Linux.BackDoor.Fgt; however, our specialists have found no such script in the malicious programs they have examined. They would appreciate it if these colleagues would provide them with specific examples of Linux.Mirai in which virus writers have included this feature.
To learn more about this Trojan family, download a PDF file of a detailed technical review prepared by Doctor Web's specialists.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments