Doctor Web discovers Windows Trojan that installs fake Chrome browser
Real-time threat news | Hot news | All the news | Virus alerts
August 29, 2016
The Trojan is notable for its ability to bypass the Windows protection system—Accounts Control (UAC). Information about this technology was first posted in an Internet blog on August 15. Just three days later, the first sample of this Trojan, which was subsequently named Trojan.Mutabaha.1, appeared in Doctor Web’s laboratory. The technology involved relies on the use of a system registry branch to launch a malware program that has elevated privileges. The Trojan contains a characteristic line that includes the project’s name:
F:\project\C++Project\installer_chrome\out\Release\setup_online_without_uac.pdb
First, a dropper, which saves an installer to the disk and runs it, and a BAT file, which is responsible for the dropper’s removal, are simultaneously launched. Then the installer connects to the command and control server to receive a configuration file which specifies an address for downloading the browser.
The browser, named Outfire, is a special build of Google Chrome. During installation, it registers itself in the Windows system registry, launches several system services, and creates tasks in the Windows Task Manager in order to load and install its updates. In addition, Outfire modifies the installed Google Chrome browser by removing or creating new shortcuts and copying current Chrome user account information into the new browser. Finally, Trojan.Mutabaha.1 searches for other fake browsers in the system by generating its names with the help of value combinations taken from two glossaries. The total number of such variants is 56. If it finds any, the Trojan compares the name of the found browser with its own name (to make sure that the Trojan will not mistakenly delete itself) and then kills the processes of that browser, removes its records from the Task Manager, and modifies the Windows system registry.
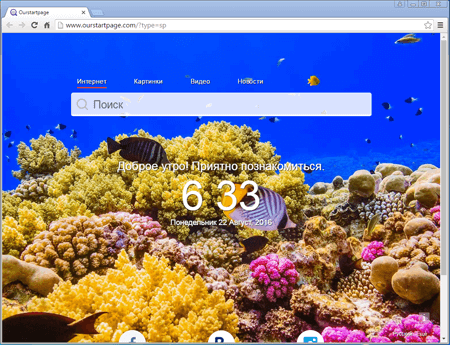
Once the installation is complete, the fake browser displays a home page which cannot be changed in the browser’s settings. In addition, it has a fixed extension designed to replace advertisements in browsed webpages and uses its own search engine, set by default—however, it can be changed in the application’s settings.
Dr.Web successfully detects and removes Trojan.Mutabaha.1, and, therefore, this malicious program poses no threat to our users.