Doctor Web discovers new Trojan targeting POS terminals
Real-time threat news | Hot news | All the news | Virus alerts
August 2, 2016
The Trojan, named Trojan.Kasidet.1, is a modified version of Trojan.MWZLesson. For more information about this threat, read this article published by Doctor Web in September 2015. Trojan.MWZLesson can also intercept GET and POST requests sent via Mozilla Firefox, Google Chrome, Internet Explorer, and Maxthon browsers.
Trojan.Kasidet.1 is distributed as a ZIP archive that contains a SCR file, which is a self-extracting SFX-RAR archive. This file then extracts and runs the main malicious payload.
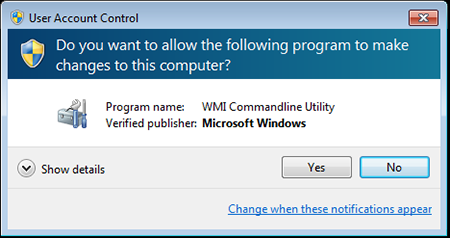
The Trojan first checks whether its copy and any virtual machines, emulators, and debuggers are present in the infected system. If Trojan.Kasidet.1 finds a program that can somehow hinder its operation, it terminates itself. If not, it gains administrator privileges and runs itself. Even though the User Accounts Control (UAC) system demonstrates a warning on the screen, the potential victim is thrown off guard because the running application (wmic.exe) appears to have been developed by Microsoft:
The wmic.exe utility then runs the executable file of Trojan.Kasidet.1. Like Trojan.MWZLesson, it scans the computer’s memory for bank card track data obtained with the help of the POS terminal and transmits it to the Trojan’s command and control (C&C) server. In addition, it steals passwords for Outlook, Foxmail, and Thunderbird email applications and can be incorporated into Mozilla Firefox, Google Chrome, Microsoft Internet Explorer, and Maxthon browsers for the purpose of intercepting GET and POST requests. This malware program can also download and run another application or a malicious library on the infected computer, find a particular file on a disk, or generate a list of running processes and transmit it to the C&C server.
However, unlike Trojan.MWZLesson, the C&C server addresses of Trojan.Kasidet.1 are placed in a decentralized domain zone—.bit (Namecoin). This is a system of alternative root DNS servers based on Bitcoin technology. Common browsers cannot access such network resources; however, Trojan.Kasidet.1 uses its own algorithm to get the IPs of its C&C servers. Although malware programs that use this Namecoin technology have been known since 2013, they are not frequently detected in the wild, unlike other Trojans.
Dr.Web Anti-virus successfully detects and removes this Trojan, and, therefore, this malicious program poses no threat to Dr.Web users.