June 23, 2016
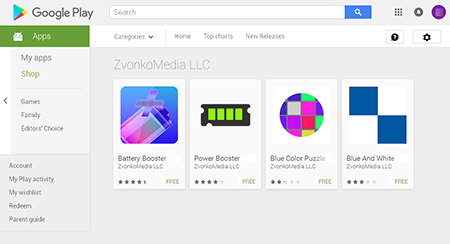
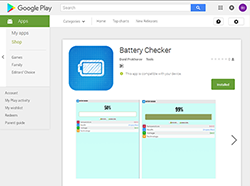
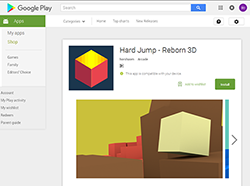
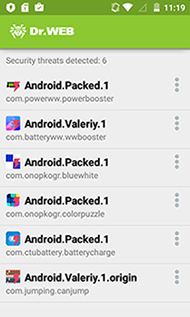
The Android.Valeriy.1.origin Trojan is implemented as a malicious plug-in incorporated into benign applications. It is distributed by ZvonkoMedia LLC, Danil Prokhorov, and horshaom in six different Android apps published on Google Play:
- Battery Booster;
- Power Booster;
- Blue Color Puzzle;
- Blue And White;
- Battery Checker;
- Hard Jump - Reborn 3D.
These programs, which are games and service tools, have been downloaded by more than 15,500 users. Besides, Doctor Web security researchers registered over 55,000 downloads of these applications after they gained access to the Trojan’s C&C server. Our specialists have already informed Google about this incident. So far, applications containing Android.Valeriy.1.origin were still available for downloading.
Once one of these applications is launched, Android.Valeriy.1.origin connects to the server and gets instructions containing a specially generated link. The Trojan follows this link that leads to some website that provides the Trojan with the endpoint URL, depending on various parameters. In most cases, this URL leads to a dubious webpage in order to get their mobile phone number and subscribe them to chargeable services. For example, the user can be offered to view some adult content or download popular software, which is, in fact, available for free on Google Play. Despite the fact that all information regarding subscription conditions is available on the webpage, the user can easily pass it unnoticed and specify their phone number.
Android.Valeriy.1.origin opens one of these websites in WebView and displays it as an advertisement. Then it starts monitoring all incoming SMS messages. If the user gives their phone number, a confirmation code for subscription is then sent. However, Android.Valeriy.1.origin intercepts and blocks all these messages. As a result, the victim does not have any idea that they are subscribed to some services and, therefore, a certain subscription fee will be written off from the user’s mobile account every day.
The Trojan can also perform another function—download software, including malicious programs. For instance, Doctor Web specialists detected the Android.DownLoader.355.origin downloader Trojan. Besides, instructions for Android.Valeriy.1.origin may contain various JavaScript scripts that are executed using WebView. These features can be implemented to covertly tap on interactive elements, advertisements and links on browsed webpages—for example, to confirm the phone number specified by the user or to increase various traffic statistics.
If you do not want to fall victim to these fraudulent schemes, we recommend you to pay careful attention to all pop-up messages and notifications and warn you against entering your phone number into suspicious input forms.
Most of applications compromised with Android.Valeriy.1.origin are protected with a special packer that complicates their analysis. However, Dr.Web for Android detects Android.Valeriy.1 and Android.Packed.1 and removes them from mobile devices. Therefore, they do not pose any threat to our users.





![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments