Doctor Web’s annual virus activity review for 2021
January 21, 2022
Among the email threats, the most popular were stealers and various backdoor modifications written in VB.NET. Cybercriminals were also actively distributing malicious PDFs, trojan downloaders, and web pages. These pages represent a credential entry form that simulates authorization on well-known sites. Some of the threats spread through mail accounted for programs that exploit various vulnerabilities in Microsoft Office documents.
In 2021, Doctor Web Virus Lab published several research pieces. One of them was the research of Spyder, a module backdoor for targeted attacks. Our experts recorded that the Winnti hacker group used this sample to attack corporations in Central Asia.
Last year, Doctor Web analysts also investigated targeted attacks on Russian research institutes. During the research, we uncovered the unauthorized presence of the APT group, whose activities remained hidden for almost 3 years.
However, cybercriminals have not limited themselves to the Windows platform. Android users were regularly attacked. Cybercriminals were actively distributing trojans in the Google Play catalog, and we also discovered the first trojans on AppGallery. The most popular threats to mobile devices were spying apps, banking trojans, malware downloaders, and trojans capable of executing code.
Principal trends of the year
- Active malware distribution on Android devices, even through the official catalogs
- Increased number of encoder incidents
- Growing number of fraudulent sites
- Spread of network fraud
Most notable events of 2021
In March, Doctor Web specialists released large-scale research of a modular backdoor designed for targeted attacks. A Central Asian telecommunication company contacted our virus laboratory. We found that the Winnti hacker group had compromised their network. The backdoor we considered for targeted attacks, the BackDoor.Spyder.1, was remarkable because its code doesn’t perform direct malicious functions. One of the main issues with this trojan is that it functions discreetly in the infected system. It also establishes a connection with the control server and waits for operator commands.
A month later, Dr.Web specialists published another research. A Russian research institute asked us for help–employees noticed some technical problems that indicated the presence of malware on a local network server. Virus analysts found that the research institute was attacked by multiple backdoors, including BackDoor.Skeye and BackDoor.DNSep. It’s noteworthy that the network was first compromised back in 2017. Since then, it has faced numerous attacks by several hacker groups at once.
In the summer, Doctor Web shared information about the critical vulnerabilities in the Windows print manager. These vulnerabilities affected all popular versions of the operating system. Cybercriminals exploited the victims’ computers for their own purposes. For example, they downloaded malicious encoders demanding a ransom for decrypting corrupted files. The CVE-2021-34527 and CVE-2021-1675 vulnerabilities are called PrintNightmare. Official patches soon appeared for them both.
The massive introduction of vaccine QR codes marked the beginning of autumn. This technology allowed fraudsters to become more active. Cybercriminals often faked the Russian Federation Government Services Portal site (Gosuslugi). Cybercriminals often faked the Russian Federation Government Services Portal site (Gosuslugi). They designed phishing sites to steal people’s credentials, then used them to perform unauthorized actions on behalf of the victims. The number of phishing sites has increased unexpectably by almost 30%. Hundreds of fake sites fill the Dr.Web SpIDer Gate database during the most active days.
The coronavirus agenda maintenance continued in December. Cybercriminals created vaccination QR code generators. Users who downloaded the malicious programs received several trojans at once. The downloaded archive contained an executable file, which the miner and clipper delivered to the victim's computer.
In 2021, the Log4j 2 logging library vulnerability also threatened users. The most critical vulnerability, Log4Shell (CVE-2021-44228), is based on Log4j 2 log message generation. When the messages are generated in a specific way, a call to a server controlled by the attackers occurs, followed by the code’s execution. Through these vulnerabilities, cybercriminals spread miners, backdoors, and Trojan-DDoS. Our products successfully detect the malware payload that penetrates devices through the Log4j 2 vulnerabilities.
Malware landscape
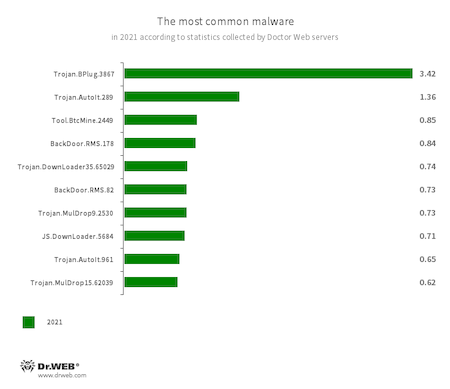
An analysis of Dr.Web’s statistics showed that in 2021, users were most often exposed to trojan droppers that installed other malicious applications. Various backdoors and trojans designed for hidden mining also threatened users throughout the years.
- Trojan.BPlug.3867
- A malicious browser extension designed to perform web injections into viewed web pages and block third-party advertisements.
- Trojan.AutoIt.289
- Trojan.AutoIt.961
- A malicious utility program written in AutoIt language. It’s distributed as part of a miner, or RAT trojan. It performs various malicious actions that make it difficult to detect the main payload.
- Tool.BtcMine.2449
- Malicious program for hidden mining.
- BackDoor.RMS.178
- BackDoor.RMS.82
- Backdoor for remote computer administration.
- Trojan.DownLoader35.65029
- Trojan for downloading malicious programs on the victim’s computer.
- Trojan.MulDrop9.2530
- Trojan.MulDrop15.62039
- A trojan dropper that distributes and installs malware.
- JS.DownLoader.5684
- Malicious scripts written in JavaScript. They download and install other malware programs on the computer.
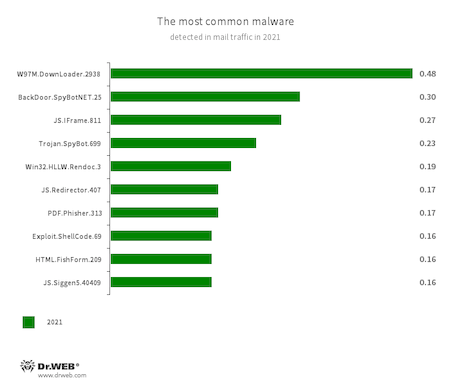
Bankers, backdoors, and malware that exploit office document vulnerabilities dominated email traffic. Besides that, cybercriminals sent fake entry forms and malicious PDF files in phishing emails.
- W97M.DownLoader.2938
- A family of downloader trojans that exploit vulnerabilities in Microsoft Office documents. It can also download other malicious programs to a compromised computer. It’s designed to download more malware onto a compromised computer.
- BackDoor.SpyBotNET.25
- A backdoor script that’s written in .NET. It’s designed to operate with a file system when copying, creating, deleting, etc, which can terminate processes and take screenshots.
- JS.IFrame.811
- A script incorporated into HTML pages. Upon opening these pages, the script redirects users to malicious or unwanted websites.
- Trojan.SpyBot.699
- A multi-module banking trojan. It allows cybercriminals to download and launch various applications on an infected device and run arbitrary code.
- Win32.HLLW.Rendoc.3
- A network worm that, among other channels, spreads via removable storage media.
- JS.Redirector.407
- Malicious JavaScript script placed in the code of web pages. It’s designed to redirect users to phishing or advertising sites.
- PDF.Phisher.313
- A PDF document used in phishing newsletters.
- Exploit.ShellCode.69
- Another malicious Microsoft Office Word document. It uses vulnerability called CVE-2017-11882.
- HTML.FishForm.209
- A web page spread via phishing emails. It’s a bogus authorization page that mimics well-known websites. The attacker receives the credentials a user enters on the page.
- JS.Siggen5.40409
- A malicious script written in JavaScript.
Encryption ransomware
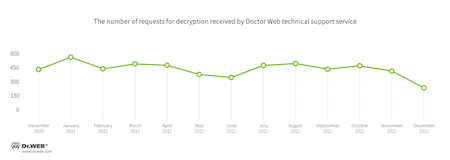
In 2021, Doctor Web’s virus laboratory registered 26.6% fewer requests to decode files encoded by trojan ransomware than in 2020. Let’s see the request dynamics for 2021 below.
The most common ransomware programs in 2021:
- Trojan.Encoder.26996
- A trojan encoder known as STOP Ransomware. It attempts to obtain a private key from the server, and in case it fails, it uses the hardcoded one. It’s one of the few encoders that encrypts user data with the Salsa20 stream cipher.
- Trojan.Encoder.567
- A trojan encoder written in Delphi. This encoder has many versions that use various encryption algorithms. Generally, it’s distributed as email attachments.
- Trojan.Encoder.29750
- A trojan encoder that belongs to the Limbo/Lazarus family. It carries the hardcoded key, which is used when it isn’t possible to connect to the C&C server and upload the private portion of the generated key.
- Trojan.Encoder.30356
- A trojan encoder written in Delphi. It uses AES-256 symmetric algorithm to encrypt files, and asymmetric RSA-2048 to protect the private key.
- Trojan.Encoder.11539
- An encryptor that has different modifications for each different encryption algorithm set. Generally, it’s distributed as email attachments and uses AES-256 in CBC mode to encrypt files.
Network fraud
In 2021, Doctor Web analysts found many dangerous sites, most of which were related to QR codes. In May, we discovered pages that allowed users to buy fake documents, like vaccination certificates. The fraudsters have even published articles on their sites to expose other cybercriminals to disguise their illegal activities.
Since then, attackers have stuck to the coronavirus topic, creating new websites and resources every month for users to buy or generate a QR code. In the summer, Doctor Web specialists found private chats where cybercriminals offer QR codes for sale. Fraudsters confirm the procedure’s "safety” with enthusiastic reviews from those who have allegedly already bought a vaccination certificate.
In the wake of the coronavirus theme, attackers were distributing fake QR code generators. We should remember that we can’t receive the vaccination certificate in any special way. It’s only generated through a link to a specific page of the Gosuslugi portal or the information system of a constituent entity of the federation concerning a citizen's immunization fact.
Mobile devices
According to the stats Dr.Web for Android anti-virus products, in 2021, Android OS users most often encountered trojans of the Android.HiddenAds family. These displayed all kinds of advertisements. They accounted for more than 83% of all malicious applications detected on protected devices. Trojans have become widespread, with their main function being to download other programs and download and run arbitrary code. Compared to 2020, the banking trojans’ activity has increased by 43%.
The most active programs among the unwanted applications were those of the Program.FakeAntiVirus family. These imitate anti-virus operations. They allow users to purchase their full versions, apparently to cure detected infections. We also found various software that allows you to track their owners on Android devices.
The number of detected potentially dangerous tools has increased by more than 53%. They include tools like Tool.SilentInstaller, which can launch Android applications without installing them. While they may be used for harmless purposes they can also distribute trojans. We detected all kinds of adware modules and adware programs quite often–their share exceeded 10% of all detected threats.
Over the past month, Doctor Web virus analysts have discovered many threats on the Google Play catalog. Among them are fake applications of the Android.FakeApp family, which cybercriminals use in many fraudulent schemes. We also found the Android.Joker Trojans, which can download and execute arbitrary code and automatically subscribe users to paid mobile services. We also detected adware trojans, adware apps, and banking trojans. Besides that, cybercriminals also distributed malicious programs from the Android.PWS.Facebookfamily that stole data necessary to hack Facebook accounts.
We discovered trojans in the AppGallery catalog for Huawei's Android devices for the first time. They were familiar trojans of the Android.Joker family and the malicious module Android.Cynos.7.origin, which collected users' mobile numbers and displayed ads.
Among the threats our specialists found in 2021, was the Android.Triada.4912 trojan. Cybercriminals built it into one of the APKPure application versions, which is the client software for the Android programs alternative catalog of the same name. It downloaded various websites, other malicious modules, and various applications. What’s more, Doctor Web virus analysts have discovered a new family of modular banking Trojans: Android.BankBot.Coper. They intercept and send SMS messages, execute USSD requests, lock and unlock the screen, show push notifications and phishing windows, can uninstall programs, intercept information entered on the keyboard, and perform other malicious actions.
Last year, Doctor Web also analyzed the popular children’s smartwatch models in Russia, looking for possible vulnerabilities. The research showed that the safety level in these devices is unsatisfactory. For example, one of the models had pre-installed trojan applications.
Prospects and possible trends
First of all, the past year has shown how quickly cybercriminals can adapt to one or another relevant topic. We should expect even more sophisticated scams involving covid or the coming year’s other major themes.
What’s more, adware trojans, all kinds of ransomware, and other malware will remain active. Corporations and big companies should be more mindful of information security in this new year. As practice shows, neglecting digital security rules greatly increases the risks of compromising a corporate network. We’ll remember the year 2021 for its numerous "high-profile" incidents with ransomware trojans spreading through the Ransomware as a Service (RaaS) model. This trend will continue to gain momentum.
Android OS device users should also pay attention. The number of threats in the official app catalogs is expected to increase.