A new threat for the macOS system spreads disguised as WhatsApp
Real-time threat news | Hot news | All the news | Virus alerts
May 14, 2019
Our researchers discovered the new threat on April 29. This malware was named Mac.BackDoor.Siggen.20, and turned out to be a backdoor that allows hackers to upload malicious code from a remote server and execute it.
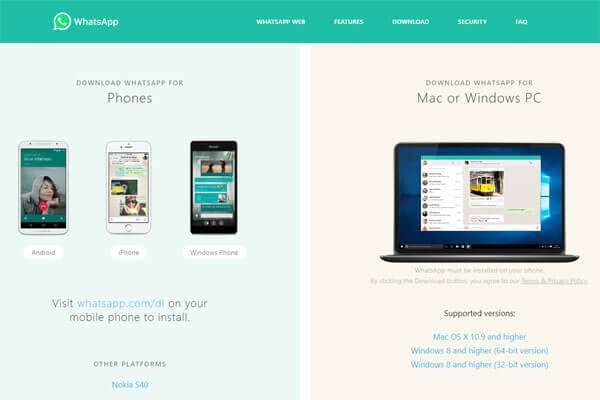
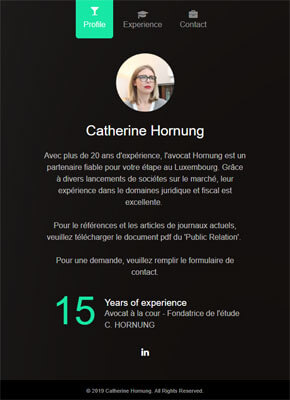
Mac.BackDoor.Siggen.20 gets on victims’ devices via websites controlled by its developers. One of the resources is disguised as a personal website with a nonexistent person’s portfolio. The other is disguised as the WhatsApp messenger official website.
When users open one of those websites, the embedded code detects the visitor’s operating system and depending on that uploads either the backdoor or a trojan. If a visitor uses macOS, their device gets infected with Mac.BackDoor.Siggen.20, and BackDoor.Wirenet.517 is downloaded on Windows devices. The latter is a well-known RAT trojan used by hackers for controlling a victim’s PC remotely. It has several malicious functions, including using the camera and microphone on the victim’s device. Additionally, the RAT trojan has a valid digital signature.
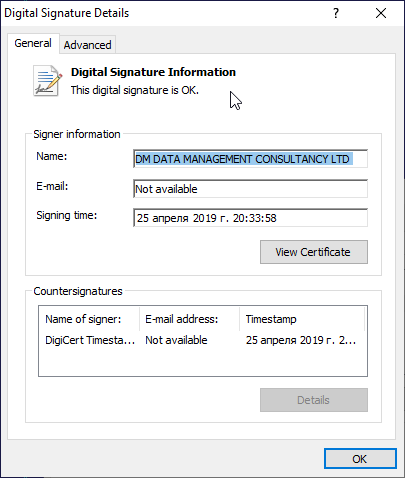
According to our information, the website spreading Mac.BackDoor.Siggen.20 under the cover of the WhatsApp messenger, was visited by about 300 visitors with unique IP addresses. The malicious resource has been active since March 24, 2019 and has not yet been used by hackers for large-scale campaigns. Nevertheless, Doctor Web’s researchers recommend staying cautious and keep the anti-virus updated. At the moment, all Mac.BackDoor.Siggen.20 components have only been detected successfully by Dr.Web anti-virus.