Gaining persistence in a compromised system using Yandex Browser. Failed spear phishing attack on Russian rail freight operator.
Real-time threat news | Hot news | All the news | Virus alerts
September 4, 2024
Spear phishing is a popular method of delivering malware to computers in large organizations. It differs from regular phishing in that the attackers gather information in advance and personalize the message they send to encourage the victim to perform an action that will result in a security breach. The primary targets are either high-level employees with access to valuable information, or employees in departments that interact with multiple recipients. This is especially true for HR staff who receive many emails from strangers that have attachments in a variety of formats. This is the attack vector of choice for the threat actors in the case we are about to discuss.
In March 2024, a large Russian company in the rail freight industry contacted Doctor Web. A suspicious email with an attachment caught the attention of their information security department. After trying to determine the threat posed by the attached file, they contacted our specialists. After reviewing the request, our analysts concluded that the company had almost been the victim of spear phishing. The goal of the perpetrators was to gather system information and launch modular malware on a compromised PC.
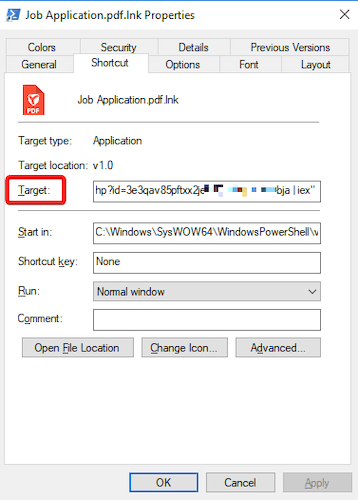
To carry out the attack, the criminals sent a phishing email disguised as a jobseeker's résumé to the company's email address. Attached to the email was an archive purporting to contain a PDF file containing a job application. That file had the so-called “double” extension of .pdf.lnk. Hiding malicious objects by using double extensions is a common tactic employed by attackers to fool their victims. By default, Windows hides file extensions as a convenience to the user. And when a file has a “double” extension, the system only hides the last extension. In this case, the victim could see the first extension—.pdf, while the .lnk extension was hidden. Moreover, even if the display of full filenames is enabled, the .lnk extension is always hidden by the operating system.
The idea of compromising systems using lnk files is not new. The most notable attack occurred in 2010, when uranium enrichment facilities in the Iranian city of Natanz suffered an unprecedented cyberattack. A worm called Stuxnet attacked the PLCs that controlled gas centrifuges, spinning them to extreme speeds and then stopping abruptly, destroying their casings. In addition to damaging the equipment, the worm infected more than 200,000 computers in many countries around the world. The primary attack vector was an lnk file that ended up on a USB drive on a corporate control computer. To run the malicious program, the user simply had to navigate to the folder containing the weaponized lnk file. The attack exploited four zero-day vulnerabilities, most notably the CPLINK exploit, which allowed the Stuxnet worm to launch without user involvement.
Metadata stored in an lnk file
The real .lnk extension is an extension for shortcuts in Windows. In the Target field, you can specify the path to any operating system object, such as an executable file, and run it with the required parameters. This attack covertly launched the PowerShell command prompt, which downloaded from the attackers' website two malicious scripts, each of which launched its own payload.
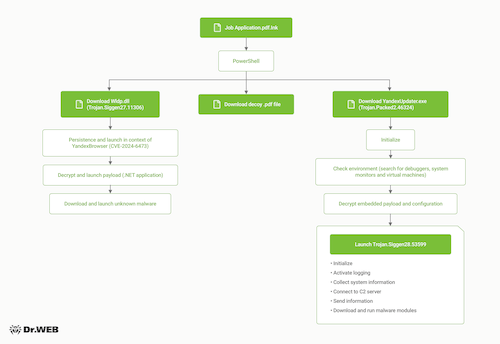
Attack chain
The first was a decoy PDF and executable file called YandexUpdater.exe, which posed as a component for updating Yandex Browser (the name of the real component is service_update.exe). This executable is a malware dropper called Trojan.Packed2.46324, which, after conducting a series of checks to determine whether it is running in an emulated environment and whether debugging software is present, unpacks Trojan.Siggen28.53599 on the compromised system. The latter has remote control capabilities, collects system information and downloads various malicious modules. In addition to these functions, the trojan also has anti-debugging capabilities. If antivirus, virtual machine and debugger processes are detected, the trojan overwrites its file with zeros and deletes it and the folder in which it was stored.
Decoy PDF file
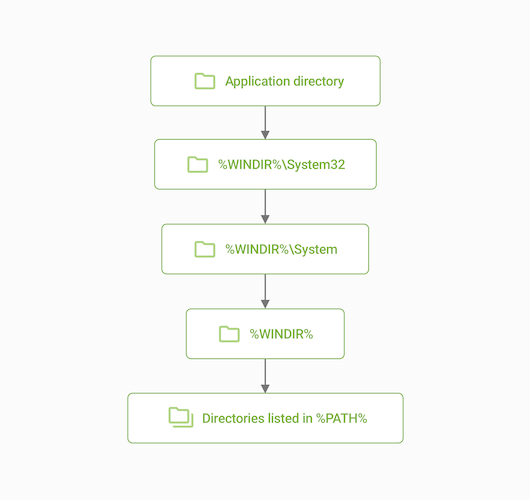
The second payload consisted of a decoy PDF file and Trojan.Siggen27.11306. This trojan is a dynamic library (DLL) with an encrypted payload. A unique feature of this trojan is that it exploits the vulnerability of Yandex Browser to DLL Search Order Hijacking. In Windows, DLL files are libraries that applications use to store functions, variables and interface elements. When launched, the applications search for libraries in several data stores in a specific order, so attackers can try to “jump the queue” and place a malicious library in the folder where DLL searches are prioritized.
Simplified DLL search prioritization scheme
This trojan is stored in the hidden %LOCALAPPDATA%\Yandex\YandexBrowser\Application folder under the name Wldp.dll. This is the directory where Yandex Browser is installed and where the browser looks for the libraries it needs at startup. In turn, the legitimate Wldp.dll library, whose function is to ensure the security of application startup, is an OS system library and is located in the %WINDIR%\System32 folder. Since the malicious library is located in the Yandex Browser installation folder, it is loaded first. At the same time, it gets all the permissions of the main application: it can execute commands and create processes on behalf of the browser, as well as inherit firewall rules for Internet access.
After the browser is launched, the malicious Wldp.dll library decrypts the payload embedded in it. Note that the decryption is done twice. The first time it is done using a key generated from the hash of the path where the malicious DLL is located, and then using a global key embedded in the body of the trojan. The decryption results in shell code, the execution of which allows attackers to run an application, written in the .NET language, on the compromised system. This executable, in turn, downloads malware from the network. Unfortunately, at the time of our investigation, the server that the downloader was communicating with was down, and we were unable to determine what specific trojan was being downloaded in this case.
Thus, we see a multi-vector, multi-stage infection scheme with two different trojans that are delivered to a compromised system when a file from a phishing email is opened. Despite the complexity of the implementation, preventing and protecting against such attacks is quite simple:
- Raise employee awareness of information security issues (carefully check links and filenames, and do not open suspicious objects).
- Use software products that perform email filtering, such as Dr.Web Mail Security Suite, to prevent the delivery of malicious emails and attachments.
- Install antivirus software, such as Dr.Web Desktop Security Suite and Dr.Web Server Security Suite, on all network nodes, which will prevent a dangerous file from getting through when users are working on the Internet or block suspicious activities on user computers if a file was delivered on a USB drive.
- Regularly apply software updates that fix program bugs.
Having discovered this vulnerability in Yandex Browser, we submitted our findings to Yandex. The developers promptly released an updated version of Yandex Browser (24.7.1.380) where this vulnerability (CVE-2024-6473) is fixed.
To ensure the safety of Yandex Browser users, we have coordinated the release date of this article with browser developers to allow users to upgrade to a patched version of Yandex Browser before the details of this attack are made public.