Doctor Web’s December 2022 review of virus activity on mobile devices
January 27, 2023
PRINCIPAL TRENDS IN DECEMBER
- An increase in the activity of adware trojans
- Increased spyware activity
- The discovery of new threats on Google Play
According to statistics collected by Dr.Web for Android
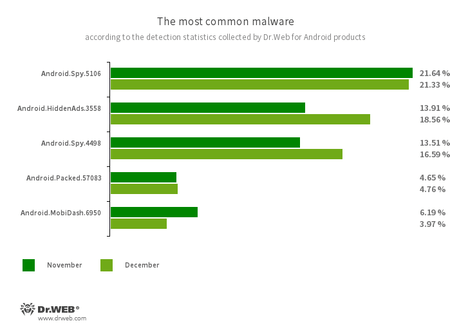
- Android.Spy.5106
- Android.Spy.4498
- The detection name for various modifications of the trojan that steals the contents of other apps’ notifications. In addition, it can download apps and prompt users to install them, and it can also display various dialog boxes.
- Android.HiddenAds.3558
- A trojan designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.Packed.57083
- The detection name for malicious applications protected with an ApkProtector software packer. Among them are banking trojans, spyware, and other malicious software.
- Android.MobiDash.6950
- A trojan that displays obnoxious ads. It is a special software module that developers incorporate into applications.
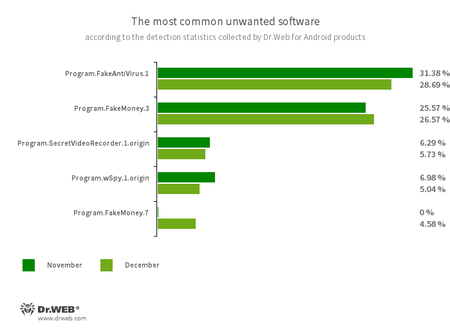
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.FakeMoney.3
- Program.FakeMoney.7
- The detection name for Android applications that allegedly allow users to earn money by watching video clips and ads. These apps make it look as if rewards are accruing for completed tasks. To withdraw their “earnings”, users allegedly have to collect a certain sum. But even if they succeed, in reality they cannot get any real payments.
- Program.SecretVideoRecorder.1.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
- Program.wSpy.1.origin
- A commercial spyware app designed to covertly monitor Android device user activity. It allows intruders to read SMS and chats in popular messaging software, listen to the surroundings, track device location and browser history, gain access to a phonebook and contacts, photos and videos, and take screenshots and pictures through a device’s built-in camera. In addition, it has keylogger functionality.
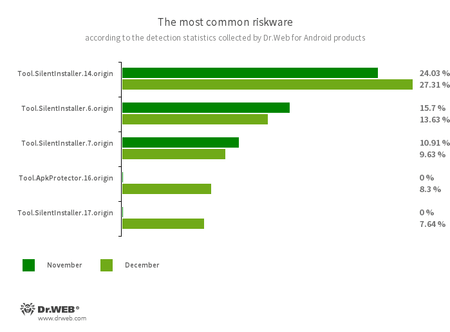
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.17.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
- Tool.ApkProtector.16.origin
- The detection name for Android apps protected by the ApkProtector software packer. This packer is not malicious in itself, but cybercriminals can use it when creating malware and unwanted applications to make it more difficult for anti-virus software to detect them.
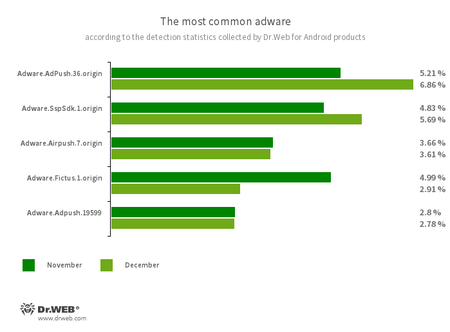
Program modules incorporated into Android applications. These are designed to display obnoxious ads on Android devices. Depending on the family and modification involved, they can display full-screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
- Adware.AdPush.36.origin
- Adware.Adpush.19599
- Adware.SspSdk.1.origin
- Adware.Airpush.7.origin
- Adware.Fictus.1.origin
Threats on Google Play
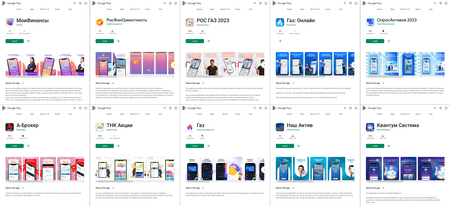
In December, Doctor Web’s specialists discovered many new threats on Google Play. Among them were dozens of trojan apps from the Android.FakeApp malware family. They connected to a remote server and, in accordance with the configuration received from it, instead of providing the expected functionality, they could display the contents of various websites—including phishing ones.
Some of these fake applications were distributed under the guise of investing software, directories, and questionnaires. Through them, users allegedly could improve their financial literacy, invest money in stocks and crypto markets, trade oil and natural gas, and even receive free shares of large companies. Instead, victims were asked to provide their personal data in order to submit an “application” for account registration or to communicate with a so-called “specialist”.
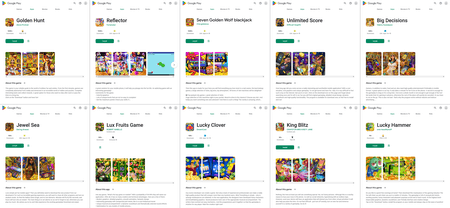
Other fake apps were hidden in numerous games.
Depending on the configuration received from a remote server, these apps could display either websites of various online casinos or a harmless game, as shown in the examples below.
Also discovered was yet another fake app distributed as a job-search tool. In reality, the app, called “SEEKS”, loaded websites with sham vacancies created by fraudsters and lured potential victims into their hands. This fake app was added to the Dr.Web anti-virus database as Android.FakeApp.1133.
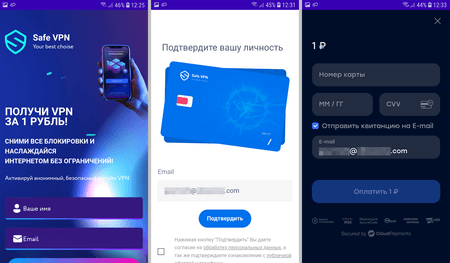
Dubbed Android.FakeApp.1141, another trojan was passed off by the attackers as a VPN client called “Safe VPN”. But it was also a fake application.
Upon launching, this app displayed the contents of a website where potential victims were offered the opportunity to obtain access to a VPN service for only 1 ruble. To do so, they were asked to create an account and pay with a bank card. In reality, they were purchasing a 3-day trial version of the service, and upon its expiration, would be charged 140 rubles daily. The information on these terms was present on the website but was placed in such a way that most victims of this scheme could miss it.
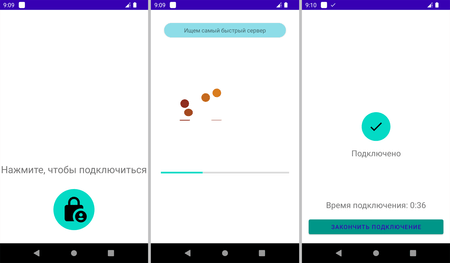
With that, this app simulated the ability to connect to a secure network, informing users of a successful connection. It was a scam as the declared functionality was not present in this fake app.
Other fraudulent apps were discovered that allegedly made it possible for users to make money by completing various tasks. One of them, “Wonder Time”, invited users to install, launch, and use other programs and games. By doing so, they received a virtual reward—tokens that could allegedly be converted into real money. However, to withdraw what they “earned”, users had to collect millions of these rewards, while only a small number of tokens was credited when tasks were completed. So even if users managed to collect the required amount, they would spend much more in time, effort, and other resources than the profit they expected to gain. Depending on the version, this app is detected by Dr.Web as Program.FakeMoney.4, Program.FakeMoney.5, and Program.FakeMoney.6.
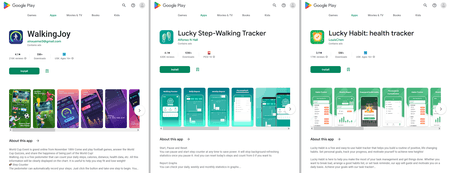
Several programs with similar operating routines were added to the Dr.Web anti-virus database as Program.FakeMoney.7. For instance, this virus record detects applications like “Lucky Habit: health tracker”, “WalkingJoy”, and some older versions of “Lucky Step-Walking Tracker”. The first was distributed as an app for developing good habits, while the others—as pedometers. Users accrued virtual rewards (“tickets” or “coins”) for various achievements, like the distance that users walked, when they followed a healthy daily routine, and so on. They also accrued additional rewards for watching ads.
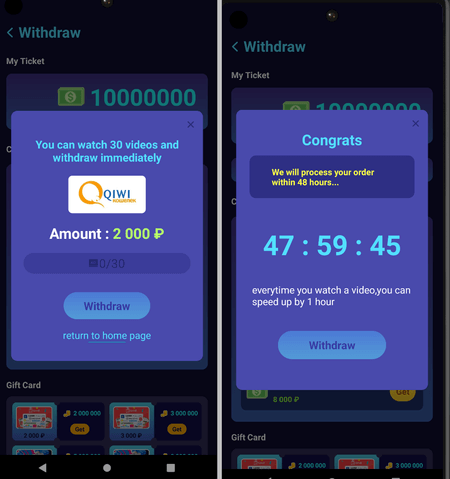
Similar to the previous case, in order to initiate the process of withdrawing what they “earned”, users had to collect a significant number of rewards. If they were able to do this, the applications additionally demanded that they watch dozens of advertising videos. They were then offered several dozen more ads to watch in order to “speed up” the withdrawal process. With that, the apps did not verify any of the payment-related data provided by users, so the chances of receiving any of the money promised from these apps are extremely small.
Moreover, earlier versions of the “Lucky Step-Walking Tracker” app, which Dr.Web detects, invited users to convert their rewards into various online store gift cards. However, with the release of the app’s update, the developers removed the functionality for converting rewards into real money by getting rid of the corresponding interface elements. As a result, all previously accumulated rewards became useless numbers. At the same time, all three apps—“Lucky Habit: health tracker”, “Lucky Step-Walking Tracker”, and “WalkingJoy”—share the same [string]richox[.]net[/string] C&C server. This might indicate that they are all connected and that at any moment “Lucky Habit: health tracker” and “WalkingJoy” users may also lose all hope of receiving payments.
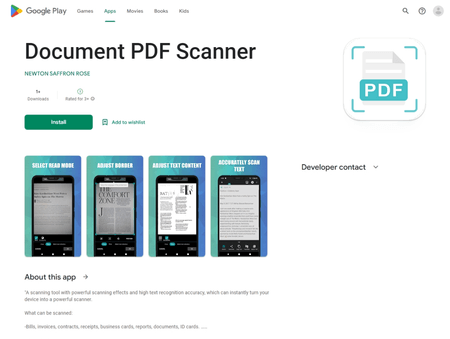
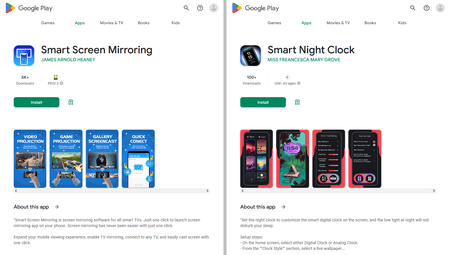
Among the threats discovered were also new trojan applications from the Android.Joker family that subscribe victims to paid services. They were hidden in such apps as “Document PDF Scanner” (detected by Dr.Web as Android.Joker.1941), “Smart Screen Mirroring” (detected as Android.Joker.1942), and “Smart Night Clock” (detected as Android.Joker.1949).
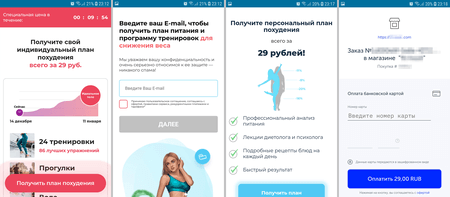
In addition, the app “FITSTAR”, disguised as a fitness app, was also distributed through Google Play.
When launched, it loaded websites where users—for the relatively low price of 29 rubles—were offered the opportunity to purchase an individual weight-loss plan. In reality, the displayed cost was not final. For this money, users were only purchasing 1-day trial access to the service. Upon the end of the trial period, an automatic 4-day prolongation would be made for the price of 980 rubles. And the cost of full access to the service could go as high as 7,000 rubles, while further automatic prolongation of the current subscription was also assumed.
As a result, Android device users who have inadvertently installed this app could lose a significant amount of money. This app was added to the Dr.Web anti-virus database as Program.Subscription.1.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products