Malware found on the AppGallery app store for the first time
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
April 7, 2021
Android.Joker is relatively old malware family known since the fall of 2019. Doctor Web malware analysts come across new versions and modifications of these trojans almost daily. They were formerly seen most often on the official Android app store―Google Play. The attackers, however, have apparently decided to expand the scale of their activity and shift their attention to alternative catalogs supported by major players on the mobile device market.
Similar to other Android.Joker trojans, the discovered modifications were spread under the guise of harmless apps that, when launched, worked as users would have expected. This technique allows attackers to stay below the radar for prolonged periods of time and infect as many Android devices as possible. For victims, the trojans acted like virtual keyboards, a camera app, a launcher, an online messenger, a sticker collection, coloring programs, and a game. 8 of these apps were distributed by the developer Shanxi kuailaipai network technology co., ltd, while the other 2 by the developer 何斌.
The Android.Joker trojans are multi-component threats capable of executing various tasks depending on the attackers’ needs. The decoy apps spread by the malware creators and installed by the victims typically represent basic trojan modules with minimal functionality. With that, the primary malicious tasks are executed by other modules downloaded from the Internet. New modifications operate the same way. Since several virus records have been created to detect these new modifications, further description of their work will be based on the modification dubbed Android.Joker.531.
Once the malware is launched, users interact with full-fledged applications. However, behind the mask of harmless software, the trojans connect to the C&C server, receive necessary configuration and download one of the additional components, which is then launched. The downloaded component is responsible for automatically subscribing Android device users to premium mobile services. In addition, the decoy apps request access to notifications that they will later need to intercept incoming SMS from premium services with subscription confirmation codes. The same apps set the limit on the number of successfully activated premium services for each user. By default, the limit is set to 5, but it can be increased or decreased upon receiving the configuration from the C&C server. For example, in the configurations our specialists intercepted, the number reached 10.
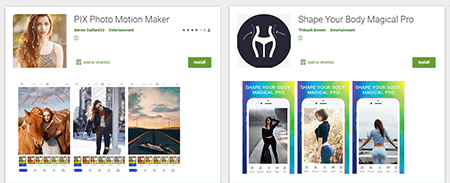
The downloaded trojan module is detected by Dr.Web as Android.Joker.242.origin. The same virus record successfully detects other similar modules downloaded by all 10 new malware modifications. Moreover, the same modules were used by some other versions of the Android.Joker, which were spread, among other places, on Google Play, for example, by apps such as Shape Your Body Magical Pro, PIX Photo Motion Maker, and others.
The Android.Joker.242.origin connects to the remote server and requests the configuration. This configuration contains the list of tasks with the websites of premium services, JavaScript scripts used to imitate user actions on the targeted websites, as well as other parameters.
Next, following the specified subscription limit, the trojan attempts to activate paid services listed in the command. In order for the subscription to be successful, the infected device must be connected to mobile Internet. Android.Joker.242.origin checks the current connection and if it detects an active Wi-Fi connection, it tries to disconnect it.
After that, for each task, the malicious module creates a non-displayable WebView and sequentially loads the website address of the paid service into each of them. The trojan then loads JavaScript. It uses it to click on the buttons contained in the web form of the targeted website, automatically substituting the victim’s phone number and the PIN with the confirmation code, intercepted by the base module, for example―Android.Joker.531.
At the same time, these malicious applications not only search for the activation codes, but also transmit the contents of all notifications about incoming SMS to the C&C server, which can lead to data leaks. Over 538,000 users have downloaded these malicious apps.
“After receiving an alert from Doctor Web, Huawei hid the trojans in the AppGallery store to protect users. The company will conduct an additional investigation to minimize the risks of such apps appearing in the future”, AppGallery press service noted.
Dr.Web anti-virus products for Android successfully detect and delete these and other modifications of the Android.Joker trojans, so they pose no threat to our users.
More details on Android.Joker.531
More details on Android.Joker.242.origin

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products