Trojan.DownLoad2.29598 tries to protect itself from anti-viruses
Real-time threat news
July 14, 2011
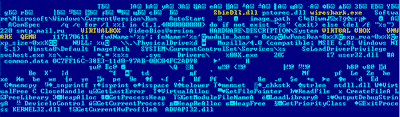
Once launched on an infected computer, Trojan.DownLoad2.29598 adds the path to its executable file into the registry key specifying applications launched at start-up and then allocates for its own needs a certain amount of memory and loads system libraries necessary for its operation into the memory. In other words, the Trojan horse features its own library loader and therefore can successfully evade hooks set by security software.
As a consequence, most debuggers are unable to determine the names of the routines used by the malware which often hampers analysis of such threats. Also the Trojan horse uses a special routine to check if it is running on a virtual machine. Thus, this malicious program protects itself from the analysis with auxiliary tools typically used by developers of anti-virus software.
When downloaded to the victim's computer, Trojan.DownLoad2.29598 sends a request to the server smtp16.mail.ru to check if an Internet connection is available. After that the Trojan horse attempts to connect to a remote control centre and sends an encrypted request. In response it receives either an instruction to download a malicious file and launch it as a background process or to inject its code into a running process or to launch a driver.
The signature of Trojan.DownLoad2.29598 is already added into the Dr.Web virus databases, so our users are completely protected from this Trojan horse program. We also recommend you to perform a full scan of your computer's hard drive regularly.