February 6, 2013
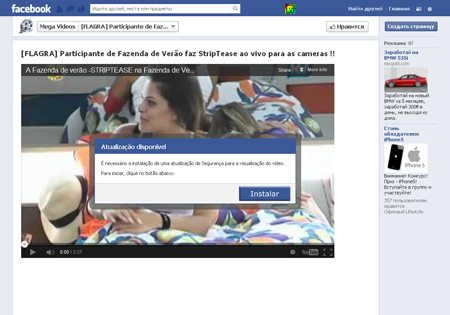
Entitled Videos Mega or Mega Videos, by February 5, 2013, the thematic groups totalled several hundred. When a visitor to one of these thematic groups clicks on a malignant link concealed by a flash player image, they trigger a script that prompts them to update the flash player. The prompt mimics the look and feel of Facebook.
If the user agrees to install the update, a self-extracting archive containing Trojan.DownLoader8.5385 is downloaded to their computer. Like other components downloaded by the malware, the Trojan has a legitimate digital signature issued in the name of the company Updates LTD by Comodo, so installation doesn't set off any operating system security alarms.
Trojan.DownLoader8.5385 is a typical malicious downloader, whose main task is to download and run other malware on an infected computer. This program downloads plugins for the browsers Google Chrome and Mozilla Firefox; the plugins are designed to send invitations to various Facebook groups and to “like” posts on the social networking site. In addition, these malignant extensions can do the following:
- Gather information about users of Facebook who are on the “friend list” of the individual whose system has been compromised.
- “Like” social networking pages or external materials.
- Share a photo album on a given page.
- Join groups.
- Send “join group” invitations to users on the “friend list”.
- Post links on a user's "wall".
- Change a user’s status.
- Open chat windows.
- Join activities.
- Invite users to activities.
- Post comments.
- Receive and send suggestions.
The plugin's configuration file is downloaded from a server belonging to the criminals. The malignant extensions are detected by Dr.Web software as Trojan.Facebook.310.
Trojan.DownLoader8.5385 also installs BackDoor.IRC.Bot.2344 in an infected system. This backdoor malware can connect infected machines into a botnet and execute various commands sent via a specific IRC chat channel created by the criminals. Directives that can be executed by BackDoor.IRC.Bot.2344 include the following:
- Execute CMD commands.
- Download a file from a specified location on the Internet and place it in the specified local folder.
- Check whether a process specified in the directive is running.
- Send a list of running processes collected with the tasklist.exe utility to a remote server.
- Shut down a specified process.
- Launch an arbitrary application.
- Use a specified URL to download and install plugins for Google Chrome.
So, it can be concluded that the current security policy for Facebook applications provides a loophole for spreading malware. All the aforementioned malware has been added to the virus databases and poses no threat to systems protected with Dr.Web anti-virus products. Doctor Web urges the Internet community to exercise caution when visiting groups on Facebook and to install updates only from legitimate sources.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments