April 2015 virus activity review from Doctor Web
April 30, 2015
PRINCIPAL TRENDS IN APRIL
- Cybercriminals' attempts to attack a number of Russian defense enterprises
- New multicomponent banking Trojan targeting customers of several credit organizations
- Distribution of dangerous backdoors for Windows and Linux OSes
- New malicious programs for Android
Threat of the month
At the beginning of April, Doctor Web security researchers finished their examination of the dangerous multicomponent banking Trojan named Trojan.Dridex.49. This malware has a component that generates configuration required for the Trojan's functioning and launches the Trojan. It also includes the engine and additional modules. The Trojan's special feature is the use of a P2P protocol for establishing connection to the server.
Depending on the specified parameters, Trojan.Dridex.49 embeds itself in processes of Explorer (explorer.exe) or web browsers (chrome.exe, firefox.exe, iexplore.exe). All information transmitted between the server and the Trojan is encrypted. The Trojan can have one of the following roles on the infected computer:
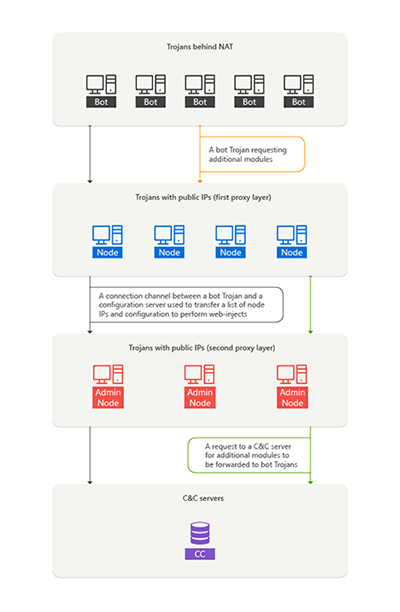
- Bot—if launched on a computer with no external IP address.
- Node—if launched on a computer with an external IP address; the Trojan receives messages from Trojans of the first type and transmits these messages to Trojans of the third type.
- Admin mode—if launched on a computer with an external IP address; the Trojan transmits messages received from Trojans to other admin nodes or to the command and control server.
In other words, the Trojan.Dridex.49 botnet uses the following scheme for message exchange: bot → node → admin node → other admin nodes → command and control server. For security reasons, the Trojans exchange keys. The entire interaction pattern of the botnet is as follows:
The main purpose of Trojan.Dridex.49 is web injection; that is, injecting arbitrary content into web pages viewed by customers of financial organizations.
The Trojan can collect confidential data entered in web forms, which allows cybercriminals to get access to victims' bank accounts and steal their money. Doctor Web's security researchers have learnt about more than 80 bank websites and other Internet resources, where the Trojan can steal confidential data; among them are well-known financial organizations such as Royal Bank of Scotland, TCB, Santander, Bank of Montreal, Bank of America, HSBC, Lloyds Bank, Barclays and many more. The signature of Trojan.Dridex.49 has been added to virus databases; so, Dr.Web users are protected from this malware.
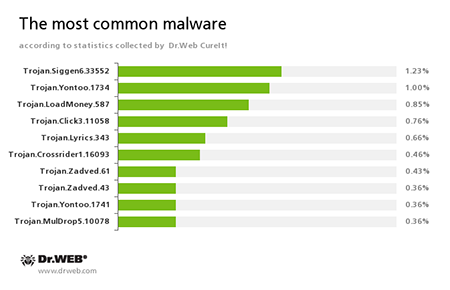
According to statistics gathered by Dr.Web CureIt!
In April, 73 149 430 malicious programs and riskware were detected.
Trojan.Siggen6.33552
This malicious program is designed for installation of another malware.
Trojan.Yontoo
Plugins for popular browsers that demonstrate ads to users as they browse web pages.
Trojan.LoadMoney
Downloader programs generated by servers belonging to the LoadMoney referral programme. These programs download and install various unwanted software programs on a victim's computer.
Trojan.Click
Malicious programs designed to generate traffic for various sites by redirecting users to the corresponding web pages.
Trojan.Lyrics
A family of Trojans that display annoying ads and open objectionable web pages without user consent.
Trojan.Zadved
Browser plugins that display fake search results and pop-up messages from social networking sites. Furthermore, their payload enables them to replace advertisements on various sites.
Trojan.MulDrop5.10078
This malicious program installs various unwanted applications and adware on an infected computer.
Trojan.Crossrider1.16093
This Trojan is designed to display various ads to Internet users.
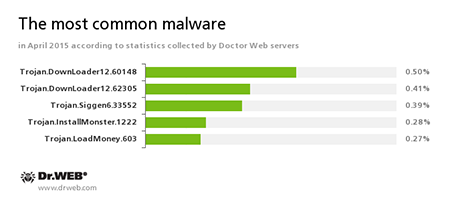
According to Doctor Web's statistics servers
Trojan.DownLoader
A family of malicious programs designed for downloading other malware to the compromised computer.
Trojan.Siggen6.33552
This malicious program is designed for installation of another malware.
Trojan.LoadMoney
Downloader programs generated by servers belonging to the LoadMoney referral programme. These programs download and install various unwanted software programs on a victim's computer.
Trojan.Installmonster
A family of malicious programs designed with the use of the affiliate program Installmonster. These programs install various unwanted software on a victim's computer.
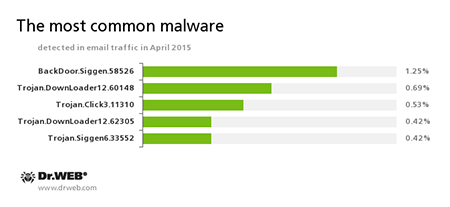
Statistics concerning malicious programs discovered in email traffic
BackDoor.Siggen.58526
The Trojan that covertly downloads and launches other malicious programs on the infected computer and executes commands of the cybercriminals.
Trojan.DownLoader
A family of malicious programs designed for downloading other malware to the compromised computer.
Trojan.Click
Malicious programs designed to generate traffic for various sites by redirecting users to the corresponding web pages.
Trojan.Siggen6.33552
This malicious program is designed for installation of another malware.
Botnets
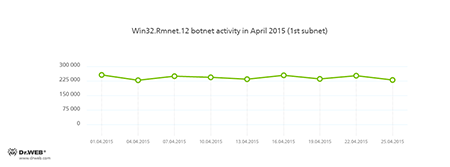
Doctor Web's security researchers continue to monitor the botnet created by criminals with the file infector Win32.Rmnet.12.
Rmnet is a family of viruses spread without any user intervention. They can embed content into loaded webpages (this theoretically allows cybercriminals to get access to the victim's bank account information) as well as steal cookies and passwords stored by popular FTP clients and execute other commands issued by cybercriminals.
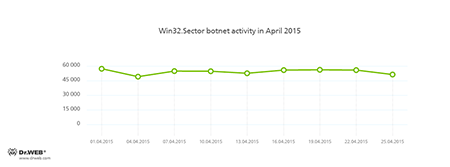
The botnet consisting of computers infected with the Win32.Sector file virus is still active. This malware can perform the following actions:
- Download various executable files via a P2P network and launch them on the infected machines.
- Inject their code into running processes.
- Can prevent some anti-viruses from operating and block access to the sites of their respective developers.
- Infect files on local disks, removable media (where it creates the file autorun.inf during the infection process), and in shared folders.
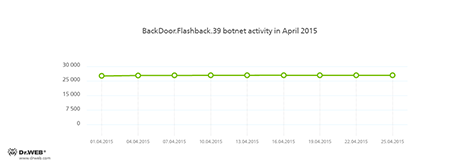
The number of Apple computers infected with the BackDoor.Flashback.39 Trojan remains almost the same and equals about 25 000:
BackDoor.Flashback.39
The Trojan for Mac OS X which was distributed on a wide scale in April 2012. The infection was carried out via Java vulnerabilities. The purpose of this Trojan is to download and run a payload on the infected machine; the payload can be any executable file specified in the directive the Trojan receives from the hacker who controls it.
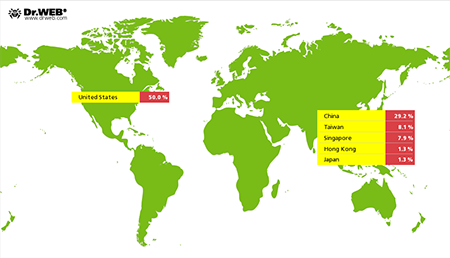
In April, cybercriminals intensified their attacks on Internet resources with the use of Linux.BackDoor.Gates.5. In comparison with the previous month, the number of attacked IP addresses increased by more than 48 per cent and was estimated 3320. Curiously, most targets of the attacks were located in the USA, but previously the country leading in the number of compromised resources was China. The image below provides information about the geographic distribution of the attacks.
Encryption ransomware
The number of requests for decryption received by the Doctor Web technical support service
| March 2015 | April 2015 | Growth |
|---|---|---|
| 2361 | 1359 | - 42.4 % |
The most common ransomware programs in April 2015
- Trojan.Encoder.761;
- Trojan.Encoder.567;
- Trojan.Encoder.741;
- Trojan.Encoder.888;
- BAT.Encoder.
Dr.Web Security Space 10.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Preventive protection | Data Loss Prevention |
|---|---|
 |  |
Threats to Linux
In April, Doctor Web security researchers examined a new Trojan that can infect computers with Linux operating system — Linux.BackDoor.Sessox.1. Cybercriminals can control the backdoor by using the IRC (Internet Relay Chat) text-messaging protocol: the bot receives their commands from a chat running on the cybercriminals' server. To spread itself, the Trojan scans remote computers and searches for a vulnerability which allows starting a third-party script on an unprotected server. The script then installs a copy of the Trojan in the infected system.
The Trojan can launch an attack by sending repeating GET requests to the website specified by cybercriminals.
Learn more about Linux.BackDoor.Sessox.1.
Other threats in April
At the beginning of the month, Doctor Web security researches detected targeted mass mailing to work and personal email addresses of Russian defense enterprises employees. The mass mailing distributed a dangerous Trojan.
Upon receiving a command from cybercriminals, this malicious program, named BackDoor.Hser.1, can send the remote server a list of active processes running on the infected computer, as well as download and launch another malicious program, open the command console and execute input/output redirection to the cybercriminals’ server, which allows cybercriminals to get control over the infected computer. Find out more about the incident in this news item.
Another malicious program, named VBS.BackDoor.DuCk.1, was also examined in April. This malware can execute cybercriminals’ commands and send the remote server screenshots made on the infected computer. This backdoor is able to check the infected computer for virtual environment and anti-virus programs. News item about this dangerous Trojan was published on the Doctor Web's site.
Dangerous websites
During April 2015, 129,199 URLs of non-recommended sites were added to Dr.Web database.
| March 2015 | April 2015 | Growth |
|---|---|---|
| 74 108 | 129 199 | + 74.3% |
Malicious and unwanted programs for Android
In April, cybercriminals continued their attacks on users of Android devices. Thus, this month was rich in virus events. Among the most noticeable events related to malicious and unwanted programs for Android we can mention
- Detection of Android.Toorch.1.origin, which is a very dangerous Trojan and is able to get root access for hidden installation and removal of various applications.
- Emergence of applications with aggressive advertising module on Google Play
- High activity of banking Trojans
Find out more about malicious and unwanted programs for Android in our special overview.
Find out more with Dr.Web
Virus statistics Virus encyclopedia All virus reviews Laboratory-live
[% END %]