Doctor Web’s September 2021 review of virus activity on mobile devices
October 15, 2021
Over the past month, Doctor Web’s malware analysts discovered dozens of new fake apps from the Android.FakeApp family. Cybercriminals used them in various fraudulent schemes.
PRINCIPAL TRENDS IN SEPTEMBER
- High activity of fake apps that were spread through the Google Play app store
- Trojans that download various software and execute arbitrary code, as well as adware remain among the most relevant threats
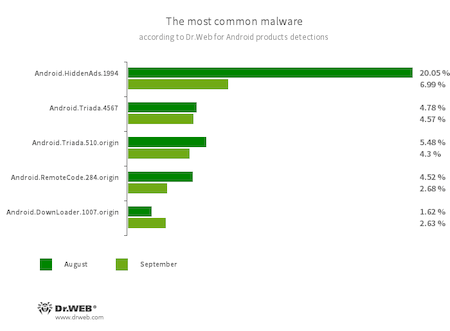
According to statistics collected by Dr.Web for Android
- Android.HiddenAds.1994
- A trojan that is designed to display obnoxious ads. Trojans of this family are often distributed as harmless applications and, in some cases, are installed in the system directory by other malware.
- Android.Triada.4567
- Android.Triada.510.origin
- A multifunctional trojans performing various malicious actions. This malware belongs to the trojan family that infects other app processes. Some modifications of this family were found in the firmware of Android devices, which attackers implanted during manufacturing. Some of them can also exploit various vulnerabilities to gain access to protected system files and folders.
- Android.RemoteCode.284.origin
- A malicious application that downloads and executes arbitrary code. Depending on their modification, trojans of this family can also load various websites, open web links, click on advertising banners, subscribe users to premium services, and perform other actions.
- Android.DownLoader.1007.origin
- A trojan that downloads other malware and unwanted software. It can be hidden inside seemingly harmless apps found on Google Play or malicious websites.
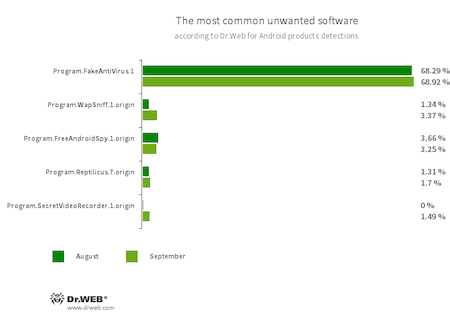
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them, and demand they purchase the full version of the software.
- Program.WapSniff.1.origin
- An Android program designed to intercept messages from WhatsApp.
- Program.FreeAndroidSpy.1.origin
- Program.Reptilicus.7.origin
- Applications that spy on Android users and can be used for cyber espionage. Depending on their modification and version, they can control the location of the device, collect information on calls, SMS, and social media chats, gain access to a phone book and user contact list, record the surroundings, and can also copy multimedia and other files, such as photos, videos, documents, etc.
- Program.SecretVideoRecorder.1.origin
- An application designed to record videos and take photos in the background using built-in cameras of Android devices. It can operate covertly, allowing to disable notifications about ongoing recordings, as well as to replace the app’s icon and name with the fake ones. Such functionality makes this software potentially dangerous.
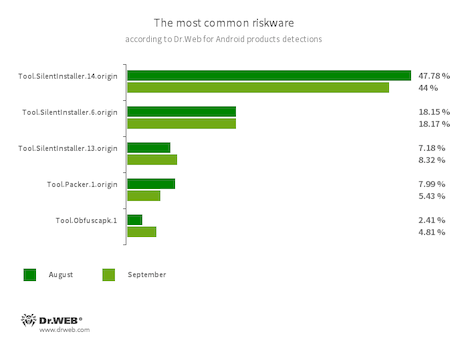
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.13.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from their unauthorized modification and reverse engineering. This tool is not malicious by itself, but it can be used to protect both harmless and malicious software.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble Android apps’ source code to make reverse engineering more difficult. Cybercriminals use the tool to protect malicious applications from being detected by anti-virus programs.
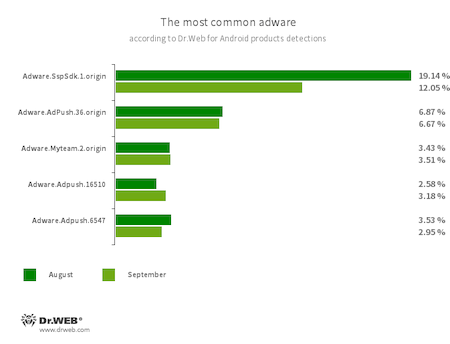
Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full-screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
- Adware.SspSdk.1.origin
- Adware.AdPush.36.origin
- Adware.Adpush.16510
- Adware.Adpush.6547
- Adware.Myteam.2.origin
Threats on Google Play
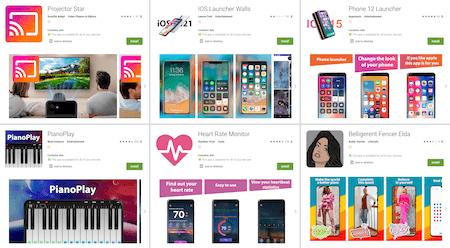
In September, Doctor Web’s specialists discovered dozens of new fake apps that helped cyber-attackers perform different fraudulent schemes. The Android.FakeApp.344 trojan was among these threats. Several of its modifications were spread as various apps, including phone launchers, image collection apps, piano-learning app, heart rate monitor software, and others.
Its main function is to load websites upon the attackers’ command. With that, the trojan can be used in many malicious scenarios. It can perform phishing attacks, subscribe victims to paid mobile services, promote websites of interest to cybercriminals, or load sites with ads.
The Android.FakeApp.344 is controlled through one of the GitHub accounts whose repositories contain trojan configuration files. Upon launch, the malware receives the necessary parameters. If there is a corresponding task in the received parameters, the trojan loads the target site. If there is no task or the malware failed to receive the configuration, it operates as a normal app. Users may not even suspect that there is something wrong with the application.
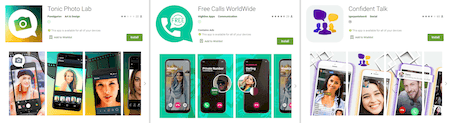
Other uncovered trojans were dubbed Android.FakeApp.347, Android.FakeApp.364, and Android.FakeApp.385. They also were spread under the guise of harmless and useful apps, such as software to make free calls, image editing software, religion-themed app, and an application to protect installed apps from unauthorized access.
However, they didn’t perform any of the declared functionality. They only loaded various websites, including those where users were asked to provide their mobile phone numbers. If they have done so, they were then redirected to the search engine main page, and the apps didn’t do anything else after that.
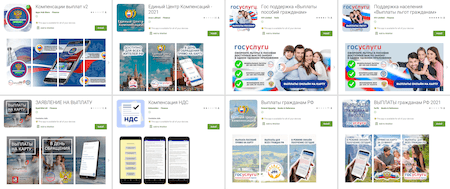
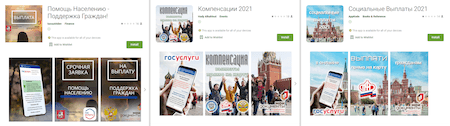
The trojans dubbed Android.FakeApp.354, Android.FakeApp.355, Android.FakeApp.356, Android.FakeApp.357, Android.FakeApp.358, Android.FakeApp.366, Android.FakeApp.377, Android.FakeApp.378, Android.FakeApp.380, Android.FakeApp.383, and Android.FakeApp.388 were allegedly designed to help Russian users search for information about government social support and receive social benefits and payouts, as well as to get VAT refunds. In reality, these fake apps only lured Android device owners to fraudulent sites where thousands of rubles were promised to absolutely any visitor. To “receive” the money, users were asked to pay a “bank commission” or “state fee” from few hundred to few thousand rubles. Victims of this scam didn’t receive any payments and transferred their own money to the fraudsters instead.
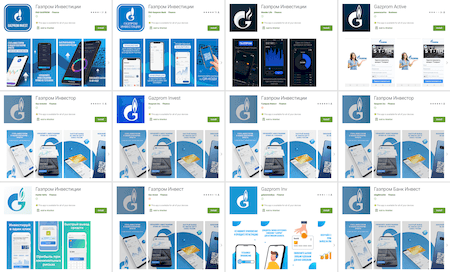
The malicious actors have also spread other fake apps which they passed off as official investing software from Gazprom company. They were added to the Dr.Web' virus base as Android.FakeApp.348, Android.FakeApp.349, Android.FakeApp.350, Android.FakeApp.351, Android.FakeApp.352, Android.FakeApp.353, Android.FakeApp.365, Android.FakeApp.367, Android.FakeApp.368, Android.FakeApp.369, Android.FakeApp.370, Android.FakeApp.382, Android.FakeApp.384, Android.FakeApp.387, and Android.FakeApp.389. With their help, Android users allegedly could receive significant passive income from investments without any economic knowledge or experience. All the work for them supposedly would have been done by a personal manager or special trading algorithm.
The examples of these apps’ pages on Google Play:
In reality, these trojan apps had nothing to do with famous companies and investments. They loaded fraudulent sites where Android users were asked to register an account by providing personal information and waiting for the “operator” to call them back. The information that victims provide to the fraudsters, including first and last names, mobile phone numbers, and emails, can be used to further trick them into scam schemes or sold on the black market.
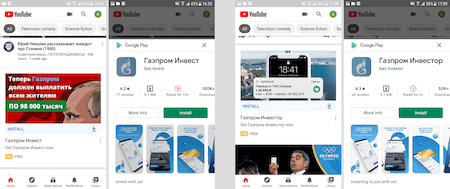
Moreover, to attract more victims and increase the installations of such fake apps, scammers are actively advertizing them on popular platforms, such as YouTube. The examples of such ads are shown below:
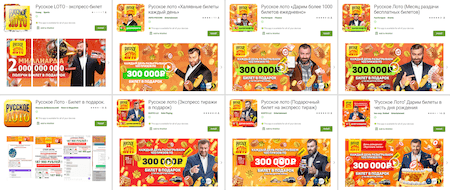
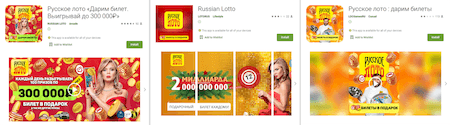
Other fakes disguised as official apps of popular Russian lotteries were also uncovered. They were added to the Dr.Web virus base as Android.FakeApp.359, Android.FakeApp.360, Android.FakeApp.361, Android.FakeApp.362, Android.FakeApp.363, Android.FakeApp.371, Android.FakeApp.372, Android.FakeApp.373, Android.FakeApp.374, Android.FakeApp.379, and Android.FakeApp.381. With the help of these apps, users allegedly could receive free lottery tickets and play lotto. But again, the only thing these apps did was that they loaded fraudulent sites where victims were asked to pay a “fee” to receive free tickets and money they “won”.
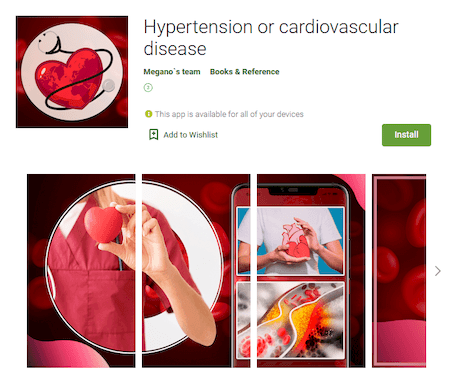
Also, our specialists discovered several modifications of the new Android.FakeApp.386 trojan that was spread as a reference software and guides with information about health and possible disease treatments. In reality, these were fakes that only loaded fraudulent sites that imitated popular online information resources. There, various drugs and pills of questionable quality and efficacy were advertized on behalf of famous doctors and media persons. Potential “clients” also had offers to allegedly get the medicine free of charge or with a significant discount. For that, users were asked to provide their names and mobile phone number and to wait for the “manager” to call them back.
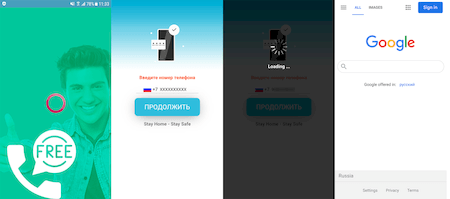
An example of one of these apps:
An example of how it operates:
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products