April 29, 2016
This April was marked by a noticeable increase in activity of aggressive advertising modules—they once again turned out to be the most frequently detected malicious applications. Besides, Doctor Web security researchers discovered a new Trojan designed to install various software, together with a Trojan incorporated into more than 190 Android applications.
PRINCIPAL TRENDS IN APRIL
- Increase in activity of aggressive advertising modules for Android
- Detection of a Trojan in more than 190 Google Play apps
- Emergence of a new Trojan that covertly installs various software
Mobile threat of the month
Yet another threat was detected on Google Play in April—Android.Click.95. This Trojan infected more than 190 applications that were distributed by at least 6 developers. The total number of downloads has exceeded 140,000.
Android.Click.95 checks whether an application specified by the Trojan is on the device. Depending on the result, the Trojan opens a bogus website with the warning and prompts the user to install the relevant software to solve the problem. To ensure its downloading, the Trojan displays this website every 2 minutes, which makes it almost impossible to use the device normally. If the user agrees to install the program, it is redirected to the relevant Google Play section. For more information about this Trojan, refer to the review.
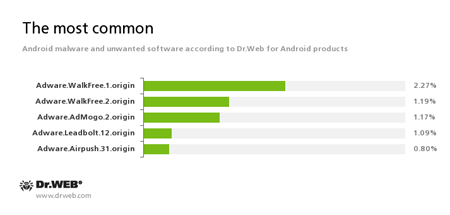
According to statistics collected by Dr.Web for Android
- Adware.WalkFree.1.origin
- Adware.WalkFree.2.origin
- Adware.AdMogo.2.origin
- Adware.Leadbolt.12.origin
- Adware.Airpush.31.origin
An unwanted program module that is incorporated into the Android applications and is responsible for advertising on mobile devices.
Downloader Trojans
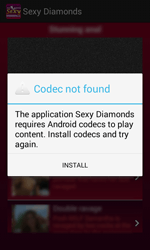
Today, one of the popular way of money making among cybercriminals is to contrive malicious programs that can download and install software picking up its rating. Yet another example of such-like application is Android.GPLoader.1.origin, which was detected in April. This Trojan comes with Android.GPLoader.2.origin that is masqueraded as an adult video player. Once launched, it prompts the user to install some multimedia codec that is, in fact, a malicious application containing Android.GPLoader.1.origin.
When running, Android.GPLoader.1.origin prompts the user to grant it access to Accessibility Service. Then the Trojan connects to the server and receives a list of programs to install. When the device goes to sleep mode, and its home screen is off, Android.GPLoader.1.origin opens Google Play and starts to download and install specified applications, which automatically picks up their rating.
Such-like malicious and unwanted applications become more and more widespread. If you want to reduce the risk of your device being infected, Doctor Web strongly recommends you not to download dubious applications and to protect your mobile devices with anti-virus software.