December 30, 2015
The last year proved to be another challenging period for the smartphones and tablets owners. Cybercriminals continued to target users of Android devices—thus, the majority of “mobile” threats and unwanted software discovered in 2015 were intended for this platform. In particular, banking Trojans, Android ransomware, advertising modules, and SMS Trojans expanded their activity. Besides, this year witnessed a growing number of malware pre-installed into Android firmware. A large number of Trojans were trying to get root privileges on Android devices and infect the system directory with various rootkits. Furthermore, cybercriminals focused on the owners of Apple products as well—quite a number of threats for iOS-based smartphones and tablets were detected in 2015.
PRINCIPAL TRENDS OF THE YEAR
- Distribution of Android banking Trojans
- Growing number of Trojans that get root privileges and infect the system directory of Android devices
- Growing number of malware incorporated into Android firmware
- Appearance of new malicious programs for iOS
Virus situation with mobile devices
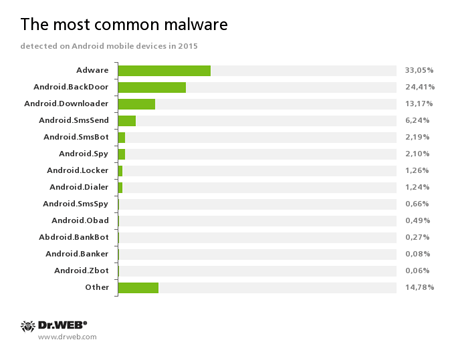
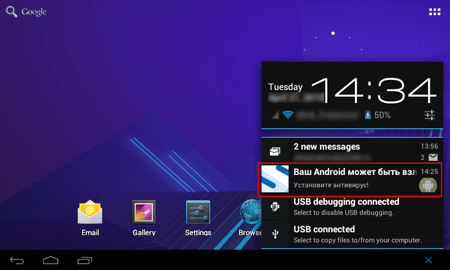
In 2015, cybercriminals continued to target Android mobile devices. The main aim of the cybercriminals was still to profit at the expense of others. However, during 12 months, virus makers’ tactics suffered significant changes—if previously they sent short messages to premium numbers, now they employ other money-making ways more and more often. According to statistics by Dr.Web anti-viruses for Android, the most common Android malware programs in 2015 were the following:
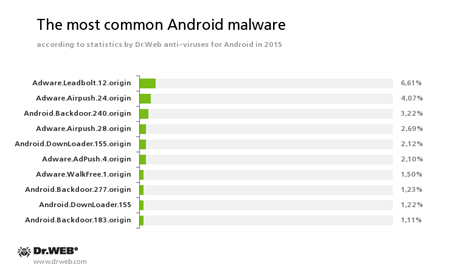
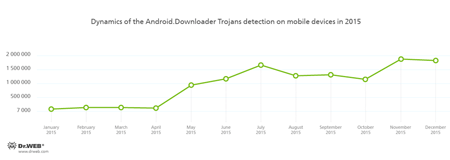
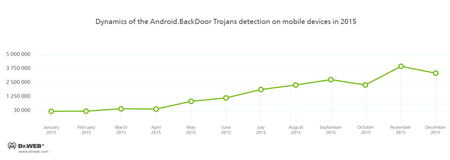
This statistics shows that the most frequently detected “mobile” threats are various advertising modules that display annoying notifications. Backdoors and downloader Trojans are also popular. They install unwanted software on infected mobile devices. At that, such malicious programs often tried to acquire root privileges for covert software installation. We can definitely say that the number of such Trojans was constantly increasing during the year. It is proved by the statistics showing the dynamics of detections by Dr.Web anti-viruses for Android: Android.BackDoor.240.origin and Android.DownLoader.155.origin, that tried to get root privileges in order to covertly install any software, are among the ten most common malware in 2015.
The following graphs illustrate the dynamics of Android backdoors and downloader programs detections in 2015. Most of them tried to get root privileges.
Trojans that get root privileges
As we mentioned before, one of the main trends in terms of information security in 2015 is a growing number of Trojans trying to get root privileges on Android mobile devices. If they succeeded, the Trojans gained full control over the device and were able to covertly install any software including its embedding into the system directory, which, in fact, compromised mobile devices with rootkits.
One of the first such Trojans was detected in March when security researchers detected Trojans belonging to the Android.Toorch family that were distributed via popular Chinese websites with downloadable software. Furthermore, the malware could be downloaded to mobile devices with the help of numerous aggressive advertising modules embedded into different applications. Once launched, such Trojans tried to acquire root privileges and install one of its components into the system directory. Upon a command from cybercriminals, Android.Toorch could download, install, and remove different software without user knowledge.
Another Trojan, Android.Backdoor.176.origin, tried to get root privileges using a modified version of the Root Master utility. If successful, the Trojan copied several malicious modules to the system directory, which made it possible for the Trojan to install and remove applications upon cybercriminals’ command. What is more, Android.Backdoor.176.origin was capable to transmit information about the infected device to the server and monitor incoming and outgoing calls and messages. A peculiar feature of this Trojan is that it set special system attributes due to which it was impossible to remove it from an infected device.
Some time later, security researchers detected a new modification of this malicious program and dubbed it Android.Backdoor.196.origin. Similar to the first version, it also tried to acquire root privileges. If successful, the Trojan launched its second component that, depending on the modification of Android.Backdoor.196.origin, was either downloaded from a remote server or extracted from the Trojan’s body and then decrypted. This module, detected by Dr.Web for Android as Adware.Xinyin.1.origin, performed all malicious activities. In particular, it was able to download and install various programs, send text messages, monitor incoming and outgoing calls and messages.
Android.Backdoor.273.origin, another Trojan for Android devices that tried to acquire root privileges, was distributed via Google Play under the guise of a benign application called Brain Test. The Trojan downloaded several exploits from the server in order to elevate its privileges. If successful, the Trojan downloaded another malicious component which got installed into a system folder. Upon a command from cybercriminals, this module can stealthily download and install other malware on the compromised device. Moreover, to stay on the device as long as possible, Android.Backdoor.273.origin installed into a system folder several additional malicious components that constantly checked integrity of each other and, if one of them (or Android.Backdoor.273.origin) was removed, the Trojan reinstalled them once again.
Another dangerous Trojan for Android devices dubbed Android.DownLoader.244.origin was distributed through websites that hosted various software for mobile devices and was incorporated into originally harmless games and applications. The Trojan tried to get root privileges and then, upon a command from cybercriminals, was able to download software from the server and install it into the system directory. It should be noted that, once the Trojan was launched, it prompted the user to enable the malicious accessibility service. If the victim followed the instructions and granted necessary privileges to the Trojan, Android.DownLoader.244.origin became able to monitor all system events and install various applications specified by cybercriminals on behalf of the user and without their consent. As a result, the Trojan had a “plan B” for its malicious activity to be carried out if it failed to get root privileges.
Firmware Trojans
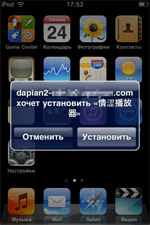
Also, in the last year, firmware Trojans became an important issue once again. Such way of malware spreading poses a serious threat because mobile gadgets owners often have no idea about such “present” inside fairly believing that their devices are benign. Even if a hidden malicious program is detected, a user will need to acquire root privileges or reinstall the operating system, which is very problematic. However, the user may have troubles with installation of third party firmware as well since virus makers manage to incorporate Trojans even into it.
One of such malicious programs—Android.CaPson.1—was detected in January 2015. It was embedded into various images of the Android platform and was able to send and intercept SMS messages, open webpages, transmit information about a compromised device to the remote server, and download other programs.
Later in September, Doctor Web security researchers found that the Android.Backdoor.114.origin Trojan was pre-installed on the Oysters T104 HVi 3G tablet. This malware can stealthily download, install, and remove applications upon a command from the command and control server. Moreover, the Trojan can activate the disabled option to install applications from unreliable sources. Android.Backdoor.114.origin also gathers and sends to the command and control server information about an infected device. For more information about this incident, refer to the review published by Doctor Web.
Already in October 2015, a pre-installed Android.Cooee.1 Trojan was detected on several mobile devices. It was incorporated into a launching application (Android graphical shell) and was designed for showing advertisements. Moreover, it was able to download and run not only additional advertising packages but also other applications, including malicious ones.
Advertising modules
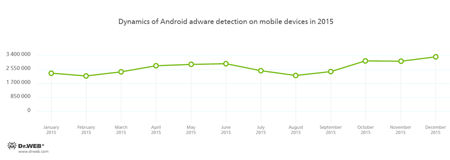
Developers of advertising modules incorporated into the Android applications earn profits from them, while such software continues to be free of charge, which is suitable for most of the users as it allows them to save their money. However, dishonest developers and, frankly speaking, virus makers of such applications more often use aggressive advertising modules that display annoying advertisements, steal confidential information, and perform another malicious activity. This tendency remained in 2015. The number of Android adware detected on mobile devices in 2015 is shown in the graph below:
In January, an unwanted advertising plugin—Adware.HideIcon.1.origin—was found on Google Play. Once those applications were installed, users encountered a barrage of annoying messages. In particular, this unwanted module displayed update notifications in the status bar of mobile devices, and imitated the process of downloading important files which, once opened, redirected a user to “paid” websites. Moreover, at launching other applications, Adware.HideIcon.1.origin was able to display full screen advertisements.
Later in February, several new unwanted modules were detected. One of these modules named Adware.MobiDash.1.origin was embedded in applications published on Google Play and downloaded by tens of millions of users. Every time the compromised device's screen was unlocked, the program loaded webpages with various ads in the browser and also displayed suspicious messages about allegedly found problems and prompted the user to install updates or certain applications, etc. It was also able to show ads or other messages in the status bar or display advertisements on top of the operating system interface and running applications. The special feature of Adware.MobiDash.1.origin lied in the fact that its unwanted activity started not right after the installation or running of the malicious applications containing this module but in a period of time, so it was difficult for users to find a true source of the unwanted activity on their devices.
In April, a new version of this module named Adware.MobiDash.2.origin was detected on Google Play as well. In total, these applications had been installed more than 2,500,000 times. For more information about Adware.MobiDash.2.origin, refer to the review.
Also in February, other aggressive advertising modules for Android were detected. One of them—Adware.HiddenAds.1—was installed by means of other malicious programs. It did not have an icon or the GUI, ran in a stealth mode, and displayed advertisements in the status bar. Another module—Adware.Adstoken.1.origin—was incorporated in applications, showed advertisements, displayed messages in the status bar, and was able to open webpages with ads in a browser. In the end of the year, Doctor Web security researchers detected yet another advertising plugin for Android that was spread with the help of the Android.Spy.510 Trojan and was added to the Dr.Web virus database as Adware.AnonyPlayer.1.origin. This malicious program displayed advertisements on top of majority of launched applications. As a result, users might think that it were the launched applications that were responsible for annoying notifications.
Banking Trojans
Trojans covertly stealing logins and passwords of mobile banking accounts and money from users’ bank accounts continue to present a threat to Android devices' users and their financial well-being. In 2015, cybercriminals continued to use such programs for their attacks, which was proved by the dynamics of adding entries to the Dr.Web virus database. Thus, during 12 months, Dr.Web anti-viruses for Android detected 880,000 cases of compromising mobile devices by banking Trojans. At that, among them are the representatives of the well known Android.BankBot, Android.Banker families, and others.
However, in the past year, Doctor Web security researchers detected a lot of new banking Trojans of the Android.ZBot family. Aside from covertly transferring money from users’ accounts to the cybercriminals’, these dangerous malicious programs can display fake dialogs and input forms for confidential data (usually a login and password for mobile banking services) on top of running applications.
The victim may be in the wrong belief that these forms belong to the running programs and, therefore, can provide their important information to the cybercriminals. Having obtained necessary data, the Android.ZBot banking Trojans send it to cybercriminals’ server—thus, virus makers gain full control over their victims’ accounts and covertly steal their money.
One of the popular ways to spread banking Trojans is distribution of unwanted text messages prompting a potential victim to follow a given link under some pretext or other. If an Android device user falls for it, they either see a scam website that distributes a malware under the guise of a useful app, or are redirected to the Trojan file automatic download from some Internet resource. Thus, in Russia, cybercriminals distributed text messages that asked potential victims to view an allegedly received MMS. Having followed a link given in the SMS, users visited fraudulent websites imitating websites of popular mobile service providers. Trojans of the Android.SmsBot family, including Android.SmsBot.269.origin and Android.SmsBot.291.origin, were among the Trojans distributed in this manner.
Cybercriminals also sent scam messages under the name of purchasers allegedly attracted by victim’s ads offering something for sale.
Aside from distribution of unwanted SMS messages with links to download a Trojan, cybercriminals use other ways of spreading banking Trojans. For instance, Android.BankBot.65.origin, a malicious program found in June, was implemented to an official app for mobile banking access and distributed under the guise of an update for this app via a popular website dedicated to mobile devices. The modification created by cybercriminals could perform all original functions of the app, so that potential victims had no reason to be suspicious. By cybercriminals’ command, Android.BankBot.65.origin can stealthily send and intercept SMS messages, thus being able to manage users’ bank accounts by means of special commands of the mobile banking services. Besides, virus makers can use this Trojan to organize fraudulent schemes by implanting various SMS messages with specified text to the list of incoming messages.
Android ransomware
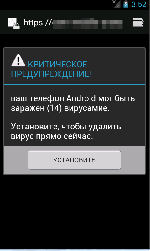
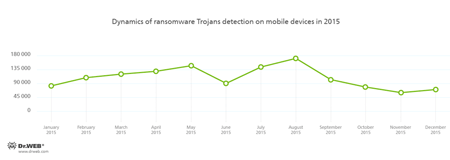
In 2015, ransomware Trojans posed a serious threat to Android users. During 2015, such malicious applications were detected more than 1,300,000 times.
Such Trojans lock mobile devices and demand a ransom to unlock them. Most of the Android ransomware follow this scheme; however, there are especially dangerous ones among them. In particular, a new modification of the Android.Locker.71.origin locker was discovered in February. This Trojan encrypted all accessible files, locked infected mobile devices, and demanded $200 as a ransom. Files were encrypted with a unique encryption key for each device, so decryption of affected data was almost impossible.
In September 2015, yet another Android ransomware that locked infected mobile devices setting unlock passwords on them was detected. Although this method is not new and was used by cybercriminals earlier, ransomware for Android are still detected rather seldom. This ransomware program was added to the Dr.Web virus database as Android.Locker.148.origin. Right after it is launched, the Trojan attempts to acquire administrator privileges. To do that, the Trojan displays a notification message on top of a standard system dialog prompting a user to install some update. By giving their consent, the user grants the Trojan administrator privileges. If this happens, Android.Locker.148.origin can lock the device without any problems setting an unlock password and demanding a ransom.
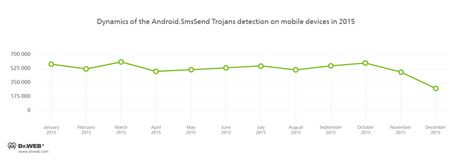
SMS Trojans
Although SMS Trojans that send text messages to premium short numbers and subscribe users to chargeable services are still a popular way of money making among cybercriminals, such Trojans little by little give a place to other malicious programs. Despite the fact that these Trojans were detected on Android devices more than 6,000,000 times, by the end of the year, the tendency to decrease of their spreading was registered.
Trojans on Google Play
Despite the fact that Google Play is an official and reliable source of software for Android, from time to time, various Trojans still can be found in the Google Play applications. This year is not the exception. At that, in July, Doctor Web security researchers detected the Android.Spy.134 and Android.Spy.135 Trojans that were incorporated into harmless games. Also, they were able to display a fake Facebook authentication form prompting users to enter their login and password details into that form. The divulged data was forwarded to the remote server. Subsequently, users from the victim's contact list received a message from their “friend” advising them to download some game. This scheme allowed cybercriminals to distribute their creations on a large scale—thus, Android.Spy.134 and Android.Spy.135 had already been downloaded from Google Play more than 500,000 times before they were removed from the website.
Also in this July, Doctor Web analysts detected another Trojan on Google Play—Android.DownLoader.171.origin whose main purpose was to download and install different applications. Moreover, it was able to remove previously installed software upon a command from cybercriminals. Android.DownLoader.171.origin was also capable of showing advertisements in the status bar of an infected device. Before this Trojan was detected on Google Play, it had already been downloaded by more than 100,000 users. However, cybercriminals also used other Internet resources (mostly oriented towards Chinese users) to distribute the malware. As a result, the total number of downloads exceeded 1,500,000 million. Find out more about Android.DownLoader.171.origin in the article published by Doctor Web.
In September 2015, Android.MKcap.1.origin incorporated into games was detected on Google Play. It was also employed to automatically subscribe users to various chargeable services. To do this, the Trojan recognized the CAPTCHA images and intercepted and processed SMS messages with confirmation codes.
Later this month, a new dangerous Trojan—Android.MulDrop.67—was detected on Google Play. Once launched, the Trojan extracted a downloader Trojan from its body trying to install it on a device. Its main purpose was to display advertisements and download and install other Trojans.
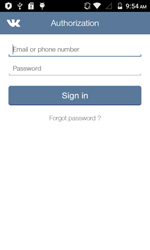
In October, the Android.PWS.3 Trojan was detected on Google Play. It was disguised as a benign audio player for listening to the VK music. However, it prompted the potential victim to log in to their VK account displaying an appropriate authorization form. Once the user entered their login and password, the Trojan forwarded this information to cybercriminals. Then it automatically added users of compromised devices promoting the communities.
Trojans for iOS
Unlike Android mobile devices, iOS smartphones did not attract virus makers for a long time. However, since 2014, security researchers have been detecting new malicious and unwanted applications for iOS more and more frequently. This tendency remained in 2015.
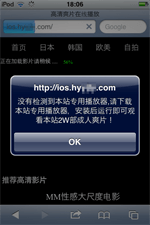
In August, the Dr.Web virus databases were updated with an entry for IPhoneOS.BackDoor.KeyRaider, a malicious program distributed in modified applications compromising jailbroken Apple devices. IPhoneOS.BackDoor.KeyRaider stole confidential data from infected gadgets and transmitted it to the server.
In September, IPhoneOS.Trojan.XcodeGhost, a dangerous Trojan for iOS, was detected in the App Store. Cybercriminals found a way to bypass the store's protection system by modifying one of Apple's official developer tools called Xcode. At that, the modified version injected the malicious code into applications already at the assembly stage. This led to originally harmless games and applications, which were “infected” using this method, being able to make their way past Apple's stringent review process and get into the App Store. The main purpose of IPhoneOS.Trojan.XcodeGhost is to show fake dialogs in order to carry out phishing attacks and to open links specified by cybercriminals. Besides, the Trojan gathers information about an infected device and forwards it to the server. In November, Doctor Web specialists detected one of the IPhoneOS.Trojan.XcodeGhost’s modifications that possessed the same features.
In October, yet another Trojan for iOS, IPhoneOS.Trojan.YiSpecter.2, was detected. It was distributed as a harmless application mainly among users in China. Since in order to spread IPhoneOS.Trojan.YiSpecter.2 cybercriminals used a corporate software distribution method, the malware could be installed on smartphones and tablets with or even without jailbreak. This Trojan also installed additional malicious modules, was able to display advertisements and, upon cybercriminals’ command, remove applications and replace them with their fake versions.
In the end of the year, IPhoneOS.Trojan.TinyV came into light. This malicious program was distributed via modified harmless applications and was downloaded to a device once a user visited websites related to mobile software. The Trojan was installed on a jailbroken Apple device and, upon receiving a command from the server, was able to covertly download and install various software and modify the hosts file. As a result, users could be redirected to non-recommended websites.
Apart from Trojans, Adware.Muda.1, an adware that infected jailbroken Apple devices, was detected in 2015. It displayed advertisements on top of launched applications and in the status bar. It also downloaded and promoted software without user knowledge.
Prospects
The events of the last year showed that cybercriminals are still interested in targeting Android devices users. At that, their main purpose—to make as much money as possible—is still the same. Thus, we can suppose that users will be threatened by numerous malicious programs.
During the last 12 months, Trojans trying to get root privileges on Android devices were actively spreading. This tendency will possibly remain in 2016. Besides, there may be new cases of malware incorporation into firmware of mobile gadgets.
New attempts to steal money from victims’ bank accounts using specially designed banking Trojans are very likely to be made.
Moreover, we should expect that a big number of new aggressive advertising modules incorporated into distributed applications will emerge.
Meanwhile, the owners of Apple devices should get ready to possible increase of attacks in 2016 as virus makers become more and more interested in targeting iOS devices as well. Thus, they will possibly make new attempts to infect Apple smartphones and tablets. Such Trojans as IPhoneOS.Trojan.XcodeGhost and IPhoneOS.Trojan.YiSpecter.2 proved that the danger to compromise iOS devices without jailbreak is quite real, so the owners of unmodified Apple mobile gadgets should be on their guard.