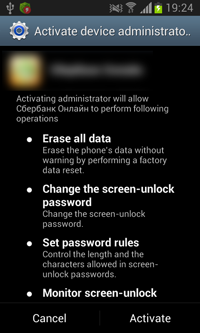
October 26, 2015
A Trojan, dubbed Android.BankBot.80.origin, is disguised as an official banking application of a Russian financial organization and has a corresponding name and an icon borrowed by cybercriminals from the original application. Once the malicious program is installed and run, the Trojan makes an attempt to acquire administrator privileges prompting the user again and again to give their consent. If the user agrees to grant the malware necessary privileges, Android.BankBot.80.origin removes its shortcut from the Home Screen and starts performing its malicious activities.
In particular, the Trojan scans the user's contact list sending to all numbers SMS messages that look as follows: Hi! Vote for me http://******konkurs.ru/ (“Привет, проголосуй за меня http://******konkurs.ru/”). The link from such a message leads to a fraudulent website supposedly related to some photo contest. From this website, a modification of Android.BankBot.80.origin detected by Dr.Web as Android.SmsBot.472.origin gets downloaded to the victim's device. Moreover, depending on the operating system of the device, the website offers owners of smartphones and tablets to install a special program for voting. However, this is just a decoy used by cybercriminals to make the website look more “real”—regardless of the operating system the user chooses, the same banking Trojan is downloaded to all mobile device.
While sending spam messages, Android.BankBot.80.origin connects to the command and control server forwarding it information about the infected Android device. The information includes the following data:
- Mobile network operator
- Device model
- IMEI
- Phone number
- OS version
- Current system language
After that, Android.BankBot.80.origin waits for further commands from cybercriminals periodically connecting to the remote node to get new instructions. The Trojan can execute the following commands:
- call_number—forward calls to a specified number;
- sms_grab—set a time interval for concealing incoming SMS messages (if a message is received during this interval, the Trojan blocks the corresponding system prompt deleting the message);
- sms_send—send an SMS message;
- ussd—send a USSD query;
- delivery—send an SMS message with specific text to all numbers from the contact list;
- new_url—set a new command and control server address.
The main purpose of the Trojan is to steal money from Russian users of several mobile network operators, financial organizations, and well-known payment systems. In particular, Doctor Web security researchers registered a few cases of this Trojan checking balances of mobile accounts, bank accounts, and accounts in a well-known payment system. For example, if the victim had some money in their mobile account, Android.BankBot.80.origin attempted to transfer it to cybercriminals' account using such service numbers as 7878 and 3116. If the user had money in a bank account or in an account in a payment system, the Trojan tried to steal it by sending an appropriate service command via SMS. Moreover, the malware tried to get access to a user account of a service provided by a mobile network operator and a Visa account in one payment system.
Doctor Web security researchers registered the use of the following phone numbers and bank card numbers belonging to cybercriminals:
- Phone numbers—9612490525, 9605116893
- Bank card numbers—VISA 4276880172933990, VISA 4276880101136772
Virus makers implemented a rather interesting feature in this Trojan—it serves the purpose of prolonging the time of the malware's presence in the system at least till the moment when the necessary funds are stolen. Since Android.BankBot.80.origin sends spam messages to all contacts from the user's phone book, sooner or later a recipient should start having doubts regarding the origin of such texts. The easiest and most reliable way to find out whether the message has been sent by your friend, relative or colleague is to call them. However, to make it impossible for other people to inform the victim about the Trojan, cybercriminals implemented in Android.BankBot.80.origin an option to block “dangerous” calls. Once SMS spam messages are sent, the malware starts forwarding all incoming calls to +79009999999 preventing the victim from being warned about the issue and cutting them off from the outside world.
Once again Doctor Web security researchers would like to warn users against installing applications downloaded from unreliable sources and opening links from dubious SMS messages. Dr.Web for Android successfully detects and removes all known modifications of Android.BankBot.80.origin, and, therefore, this malicious program poses no threat to our users.



![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments