July 30, 2015
July 2015 witnessed a surge of activity on the part of virus makers specializing in malicious programs for Linux OSes. Moreover, cybercriminals could not leave Windows unattended either—entries for new Trojans targeting this operating system were added to Dr.Web virus databases. Creators of malware for Android devices were also as active as ever—in July, Doctor Web security researchers detected a number of Trojans targeting this popular mobile platform; one of suchlike programs has already been downloaded more than 1.5 million times.
PRINCIPAL TRENDS IN JULY
- Emergence of new Linux Trojans
- Growing number of malicious programs for Windows
- Distribution of malware for Android
Threat of the month
With each passing day, malicious programs that display annoying advertisements to users as they browse various webpages become more and more dangerous—with their algorithms getting more advanced and a total number growing larger. For example, in July 2015, Doctor Web security researchers detected a new Trojan named Trojan.Ormes.186 that injects arbitrary content into webpages loaded in browser windows.
Trojan.Ormes.186 is implemented as an add-on for Mozilla Firefox, Chrome, and Opera and is distributed by means of droppers. The Trojan has a list of about 200 website addresses hard-coded in his body. On these Internet resources, among which are popular search engines, job boards, and social networking websites, Trojan.Ormes.186 performs web injections.
Moreover, the malicious program can imitate mouse clicks of Megafon (“Мегафон”) and Beeline (“Билайн”) clients to confirm various subscriptions. One can easily see that this Trojan has a rather complicated structure that allows it to perform a number of different actions, including the following ones:
- Inject advertising modules into webpages
- Redirect the user to some file-sharing resource employed to generate income by means of paid subscriptions if they open webpages of Yandex (“Яндекс”), Youtube, or of such social networking websites as Vkontakte (“ВКонтакте”), Odnoklassniki (“Одноклассники”), and Facebook in the browser window
- Display fake search results
- “Like” specified Facebook webpages
- Automatically open webpages of online casinos or install casino applications for social networking websites
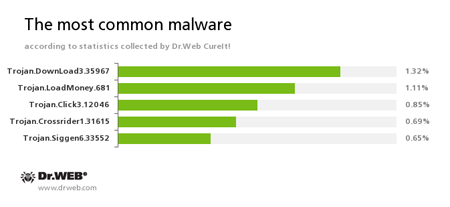
According to the statistics gathered by Dr.Web CureIt!
Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.
Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.
Trojan.Click
A family of malicious programs designed to generate traffic for various websites by redirecting users to the corresponding webpages.
Trojan.Crossrider1.31615
This Trojan is designed to display various advertisements to Internet users.
Trojan.Siggen6.33552
This malicious program is designed for installation of other malware.
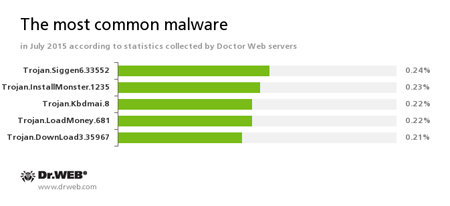
According to Doctor Web statistics servers
Trojan.Siggen6.33552
This malicious program is designed for installation of other malware.
Trojan.Installmonster
A family of malicious programs created using the Installmonster affiliate program. These programs install various unwanted software on the victim's computer.
Trojan.Kbdmai.8
A downloader Trojan designed to download other malicious programs from the Internet and run them on the infected computer.
Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.
Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.
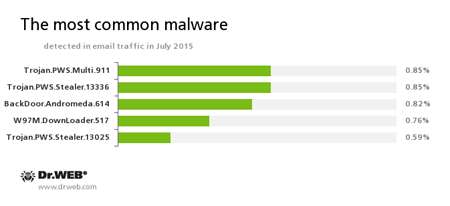
Statistics concerning malicious programs discovered in email traffic
Trojan.PWS.Multi.911
A banking Trojan that can steal various confidential data, including banking information, stored on the infected computer.
Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on the infected computer.
BackDoor.Andromeda
A family of downloader Trojans designed to download other malicious programs from remote servers of cybercriminals and run these programs on infected machines.
Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer.
Botnets
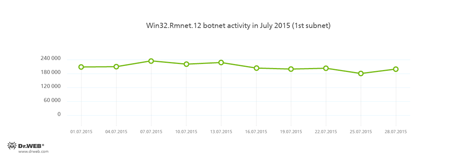
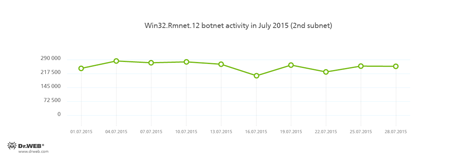
In July, the numerous botnets whose activities are being closely monitored by Doctor Web security researchers continued to remain operational. Among them is the botnet created by cybercriminals using the Win32.Rmnet.12 file infector. The average activity of the botnet's two subnets is shown in the following graphs:
Rmnet is a family of viruses spread without any user intervention. They can embed content into loaded webpages (this theoretically allows cybercriminals to get access to the victim's bank account information), steal cookies and passwords stored by popular FTP clients, and execute other commands issued by cybercriminals.
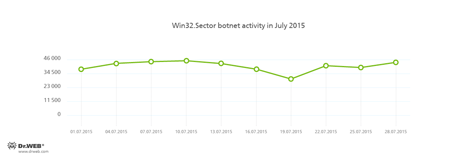
The botnet consisting of computers infected with Win32.Sector is still active, and its average daily activity can be seen in the following picture. The malicious program can perform the following actions:
- Download various executable files via P2P networks and run them on infected machines.
- Inject its code into running processes.
- Prevent some anti-viruses from operating and block access to the websites of their respective developers.
- Infect files on local disks, removable media (where the malware creates the autorun.inf file during the infection process), and in shared folders.
In comparison with the previous month, attacks on Internet resources with the use of Linux.BackDoor.Gates.5 became even less frequent. Thus, the number of attacked IP addresses decreased by 25.7 per cent and was estimated 954. Cybercriminals also considerably narrowed focus of their attacks—74.8 per cent of compromised resources were located in China, while 20.4 per cent of targeted websites were hosted in the United States.
Encryption ransomware
The number of requests for decryption received by Doctor Web technical support service
| June 2015 | July 2015 | Dynamics |
|---|---|---|
| 1,417 | 1,414 | –0.2% |
The most common ransomware programs in July 2015
- Trojan.Encoder.567
- Trojan.Encoder.858
Dr.Web Security Space 10.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Preventive Protection | Data Loss Prevention |
|---|---|
 |  |
Linux
Cybercriminals continue to create new malicious programs for Linux OSes. In July 2015, Doctor Web security researchers detected yet another Linux Trojan named Linux.BackDoor.Dklkt.1.
Its creators planned to equip the program with a large number of various features. However, at the moment, the malicious application ignores the majority of incoming commands. In fact, the Trojan can execute only the following commands: launch a DDoS attack, start a SOCKS proxy server, run a specified application, reboot the computer or turn it off. Moreover, virus makers attempted to make a cross-platform program out of their creation; so that the executable file could be assembled both for Linux and Windows architectures. Find out more about this malicious program in the news article published by Doctor Web.
Dangerous websites
During July 2015, 821,409 URLs of non-recommended websites were added to Dr.Web database.
| June 2015 | July 2015 | Dynamics |
|---|---|---|
| +978,982 | +821,409 | –16% |
Malicious and unwanted programs for Android
The previous month proved to be rather rich in terms of mobile security events—in July, new malicious programs for Android continued to appear, and users of mobile devices continued to fall victim to cybercriminals' attacks. In particular, at the end of the month, Doctor Web security researchers detected a Trojan named Android.DownLoader.171.origin that was distributed through Google Play. This malicious program has already been downloaded by about 1.5 million users. The Trojan can not only install but also remove programs without user knowledge. In addition to that, the Trojan can display fake email message notifications in the status bar. If the user taps such a notification, a website specified by cybercriminals will be loaded in the browser window. Find out more about the malware in this news article.
Among the most noticeable events related to malware for Android we can mention
- New cases of Android malware with incorporated advertising modules being employed by cybercriminals to generate income
- Emergence of new malicious applications on Google Play
- Distribution of new Android ransomware
- Emergence of new dangerous backdoors that can execute intruder-issued commands
- Growing number of SMS Trojans
Find out more about malicious and unwanted programs for Android in our special overview.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live