April 24, 2015
Anti-virus specialists have been acquainted with the Android.BankBot Trojans for several years. However, the malware became widely known in the beginning of April, 2015, when the Ministry of Internal Affairs of the Russian Federation issued a statement regarding the arrest of the cybercriminals, who used different modifications of these malicious programs to carry out attacks on bank customers of a number of Russian and International organizations. Despite the fact that the cybercriminals got arrested, distribution of this malware continues by other virus makers, who created new versions of these applications.
Recently, Doctor Web analysts have discovered several suchlike Trojans, including Android.BankBot.43 and Android.BankBot.45. They are distributed under the guise of legal software (for example, games, media players, and system update packages) and due to the social engineering methods employed by cybercriminals are usually installed on Android devices by the users themselves.
Once these malicious programs are launched on the infected device, they attempt to acquire administrative privileges, which allow the Trojans to freely perform their activity and prevent the user from removing the malware from the device. To acquire administrative privileges, the Trojans use a rather interesting method. In particular, on top of a standard system notification they display a message prompting the user to install some “add-ins”. If the user agrees, the Trojans are granted administrative privileges since by clicking “Continue” the user activates the original OS function hidden behind the malware’s window.
 |
 |
If the user attempts to remove the Android.BankBot Trojans from the device, a special message box is displayed and uninstallation is terminated. Therefore, these malicious applications cannot be removed using standard system tools.
Once the Trojans are granted the privileges, they establish a connection to the command and control server and wait for further instructions. The malware can execute the following commands:
- Call the number specified in the command
- Use the web address specified in the command to establish a connection to the command and control server
- Execute the USSD request specified in the command
- Forward all incoming and outgoing SMS messages to the server
- Reset the device settings to default deleting all user data
- Send an SMS message with the specified parameters
- Send detailed information about the infected device to the server
- Run a search for the file specified in the command
- Use the specified phone number to receive duplicate commands
Since the majority of commands are duplicated by cybercriminals via an SMS channel, the malicious applications can perform many actions even if there is no connection to the Internet or to the server. This fact makes the malware highly dangerous.
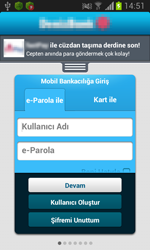
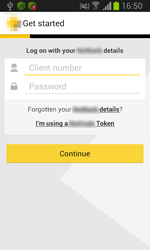
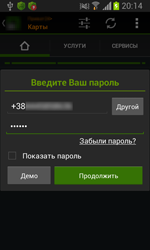
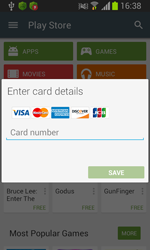
The Trojans belonging to the Android.BankBot family are designed not only to steal user’s confidential banking information but also their money. To be able to do this, the Trojans attack either online banking applications installed on devices of bank users or the Play Store application. In particular, once the user launches an online banking application, the Trojans imitate interface of these applications displaying a fake authentication form. If the user launches Play Store, the malicious programs imitate the standard form used by the user to add credit card details to their account. In fact, the Trojans force their victims to enter the necessary data since it is impossible to close the displayed message box and continue to work with Google Play. Once the divulged confidential information has been forwarded to the command and control server, cybercriminals can steal money from users’ bank accounts since all the SMS messages sent by banks’ security systems are intercepted by the malware.
 |
 |
 |
 |
However, the Android.BankBot Trojans can also perform other malicious activities. For example, many of them can interfere with attempts of various famous anti-virus applications to remove Banking Trojans from infected devices. Doctor Web issued a special update for Dr.Web anti-virus solutions for Android encompassing an effective mechanism to withstand such attacks. Therefore, the Trojans belonging to the Android.BankBot family no longer pose a threat to our users.
This update will be installed automatically on Android devices with Dr.Web anti-virus solutions. If automatic updates are disabled, visit Google Play and choose a corresponding version of the installed Dr.Web anti-virus for Android. Click “Update”. You can also download a new distribution file from Doctor Web official website.
We recommend the users, who do not have Dr.Web for Android and Dr.Web for Android Light installed on their mobile devices, to download and install these programs in order to protect themselves from the unwanted activity of Banking Trojans and other malicious applications.


![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments