February 27, 2015
According to the news reports, on February 24, 2015 command and control servers of Rmnet botnet were shut down by combined efforts of several organizations. The operation involved the Europol's European Cybercrime Centre, CERT-EU (Computer Emergency Response Team), Symantec, Microsoft, AnubisNetworks and other European organizations. In particular, at Europole's web page it is reported that IT security specialists managed to intercept about 300 Internet domain addresses of command and control servers generated by a malicious program, and Reuters news agency informs that 7 command and control servers were shut down during the operation. According to Symantec, this operation phased down botnet consisting of 350,000 compromised devices, and according to Microsoft, their total number may reach up to 500,000.
Doctor Web's security researchers monitor several botnets' subnets, created by hackers, using different versions of the Rmnet file infector. Thus, the modification called Win32.Rmnet.12 is known since September 2011. Win32.Rmnet.12 is a complex multi-component file infector, consisting of several modules. This program is capable of self-replication. It can execute commands issued by criminals, embed content into loaded web pages (it theoretically allows cybercriminals to get access to the victim's bank account information) as well as steal cookies and passwords stored by the popular FTP-client programs, such as Ghisler, WS FTP, CuteFTP, FlashFXP, FileZilla, Bullet Proof FTP and others.
A later modification of the virus, Win32.Rmnet.16, differs from its predecessor for several architectural features, such as the use of a digital signature when selecting the command and control server. The virus is also able to execute commands to download and run arbitrary files, update itself, to take screenshots and send them to criminals, and even to render the operating system non-operational. Besides, the module can kill processes of the majority of popular anti-virus programs. Like its predecessor, Win32.Rmnet.16 can modify the MBR and store the files at the end of the disk in encrypted form.
Despite the fact that numerous news agencies report on successful operation to block the activity of the Rmnet botnet, Doctor Web's analysts do not register any decrease of the botnets activity monitored by the anti-virus laboratory. So far, Doctor Web's security researchers have learnt about at least 12 Rmnet's subnets that use algorithm of generating the control servers' domains and at least two Win32.Rmnet.12 subnets, that do not use the automatic domains generation (Symantec's specialists blocked only one subnet with seed 79159c10 from the first category).
In particular, two Win32.Rmnet.12 subnets still infect 250,000–270,000 hosts on a daily basis, as it is shown in the charts below:
Average daily activity of Win32.Rmnet.12 botnet,1st subnet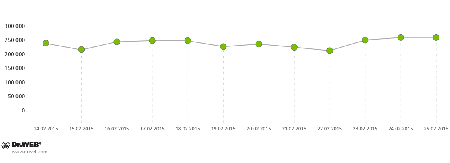
Average daily activity of Win32.Rmnet.12 botnet, 2nd subnet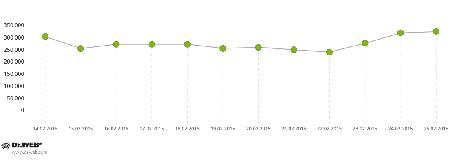
The Win32.Rmnet.16 subnet, monitored by Doctor Web's security researchers, has much smaller daily activity, but there is also no “failures” related to a possible command and control servers' shut down:
Average daily activity of Win32.Rmnet.16 botnet 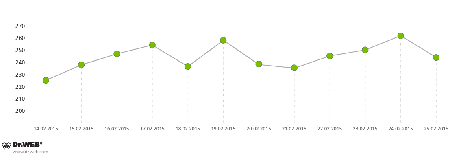
A similar situation exists when monitoring computers compromised with malicious modules, known as Trojan.Rmnet.19:
Average daily activity of Trojan.Rmnet.19 botnet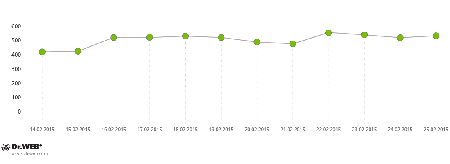
The given statistics shows that the organizers of the operation which was aimed to destroy the Rmnet botnet have apparently failed to eliminate all command and control servers of this botnet. At least no fewer than 500,000 computers, compromised with various modifications of this virus, still remain active and refer to the survivors command servers. Doctor Web will monitor the future situation.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments