February 3, 2015
According to Doctor Web's security researchers, in the first month of 2015 cybercriminals organised mass mailings of malware designed to install other dangerous applications on infected computers. In January, many Windows users suffered under the effects of encoders. As before, the number of Trojans and other malware programs threatening users of Android-powered devices remained high.
PRINCIPAL TRENDS IN JANUARY
- Mass mailings of Trojans designed to install other malicious applications.
- The spread of encryption ransomware, posing a serious hazard to Windows users.
- New malicious applications for Android-powered devices.
Threat of the month
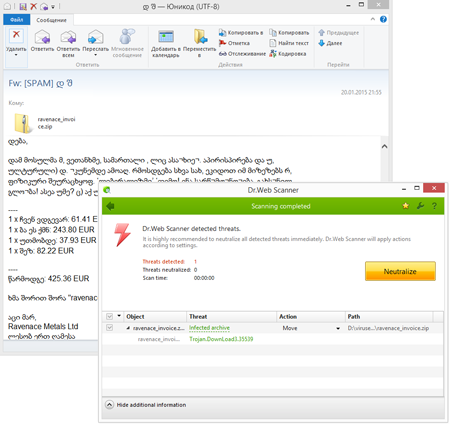
In mid-January, attackers carried out a mass mailing of Trojan.DownLoad3.35539.
- It is distributed in email messages as an attached ZIP archive.
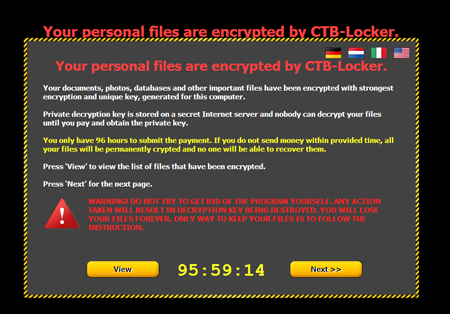
- The program's main objective is to download and launch Trojan.Encoder.686 (a.k.a. CTBLocker) on infected machines.
According to Doctor Web security researchers, messages of this kind come in many languages including English, German, and even Georgian.
Files compromised by this encryption Trojan can't be recovered.
However, this malware is successfully detected by Dr.Web Anti-virus and, thus, users are protected from this Trojan’s activities.
More information about this incident can be found in a news article published by Doctor Web.
Encryption ransomware
The number of requests for decryption received by the technical support service
| December 2014 | January 2015 | Movement |
|---|---|---|
| 1096 | 1305 | +16,1% |
In January, the number of users compromised by Trojan.Encoder.686 increased — the anti-virus laboratory recorded 51 requests. Trojan.Encoder.686 was compiled using TOR and OpenSSL libraries and relies heavily on their encryption routines. While encrypting data, the ransomware uses CryptoAPI to generate random data as well as elliptic curve cryptography.
Virus writers give their victims only 96 hours to pay the ransom required to recover their files and threaten that a failure to comply with their demands will result in permanent data loss. To acquire information about the terms and the ransom amount, users are directed to a site residing in the TOR network
Unfortunately, it is currently impossible to decrypt files affected by Trojan.Encoder.686. However, Dr.Web successfully detects this malicious program, and users of our products are protected from its actions.
The other most common encoders:
- Encoder.556
- Encoder.858
- Encoder.567
- Encoder.398.
By performing timely backups and placing reasonable restrictions on user privileges, and by using a state-of-the-art anti-virus equipped with routines that neutralise such threats, PC owners can protect their data from encryption ransomware. Dr.Web Security Space 10.0 possesses effective tools for countering encoders; these include special preventative protection components that keep data safe from the activities of ransomware.
Use Data Loss Prevention to protect your files from encryption ransomware
| Only available in Dr.Web Security Space 9 and 10 |
| More about encryption ransomware |  |
Configuration presentations tutorial |  |
Free decryption |
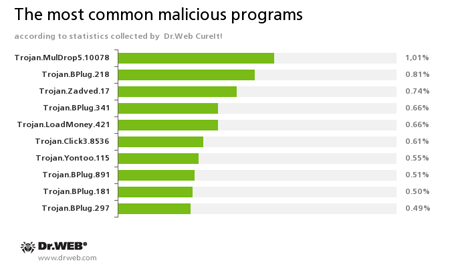
According to statistics gathered by Dr.Web CureIt!
Trojan.MulDrop5.10078
Installs various unwanted applications and adware on an infected computer.Trojan.BPlug
These plugins for popular browsers display annoying ads to users as they browse web pages.Trojan.Zadved
Add-ins designed to spoof browser search engine results as well as to display fake pop-up messages in social networks. In addition, these Trojans are capable of replacing advertising messages displayed on various websites.Trojan.LoadMoney
Downloader programs generated by servers belonging to the LoadMoney referral programme. These programs download and install various unwanted software programs on a victim's computer.Trojan.Click
A family of malicious software that uses cheating techniques to bring more visitors to various Internet resources. This involves redirecting victims to certain sites by controlling browser behavior.Trojan.Yontoo
Plugins for popular browsers that demonstrate ads to users as they browse web pages.
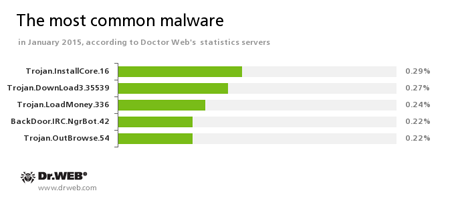
According to Doctor Web's statistics servers
Trojan.InstallCore.16
The Trojan that installs ads and suspicious applications (a.k.a.Trojan.Packed.24524).Trojan.DownLoad3.35539
The downloader Trojan that spreads via email as a ZIP archive containing a .SCR file. When you try to open the file, the Trojan saves the RTF document to your infected computer’s drive and then displays it on your screen. Simultaneously a malware program loads the payload (i.e., Trojan.Encoder.686, a.k.a CTB-Locker) from the attackers’ remote servers and runs it on your PC.Trojan.LoadMoney.336
A representative of the family of downloader programs generated by servers belonging to the LoadMoney referral programme. These programs download and install a variety of unwanted software on their victim's computers.BackDoor.IRC.NgrBot.42
A fairly common Trojan, known to information security researchers since 2011. Malicious programs of this family are able to execute intruder-issued commands on infected machines, and cybercriminals use the text-messaging protocol IRC (Internet Relay Chat) to control those PCs.Trojan.OutBrowse.54
One of the representatives of a family of adware Trojans which are spread via referral programmes that focus on generating income from file downloads.
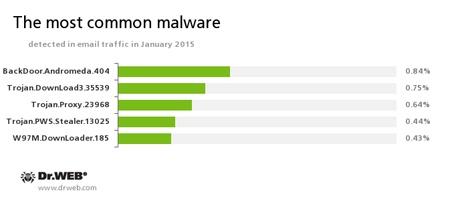
Statistics concerning malicious programs discovered in email traffic
BackDoor.Andromeda.404
This downloader Trojan is designed to download other malware from remote, hacker-controlled servers and run it on infected machines.Trojan.DownLoad3.35539
The downloader Trojan that spreads primarily via email as a ZIP archive containing a .SCR file. When you try to open the file, the Trojan saves the RTF document on your infected computer’s drive and then displays it on your screen. Simultaneously the malware loads the payload (i.e. Trojan.Encoder.686, a.k.a CTB-Locker) from the attackers’ remote servers and runs it on your PC.Trojan.Proxy.23968
The Trojan designed to be installed in an infected proxy server system; its role is to intercept confidential information when working with the remote banking service systems of several Russian banks. Once launched on a victim’s machine, it changes the network connection settings, writing into them a link to an automatic configuration script. User traffic is redirected through a hacker proxy server, which can substitute a “Bank-client” system webpage for a malicious one. To organise HTTPS connections, the Trojan sets a bogus digital certificate in the system.Trojan.PWS.Stealer.13025
Malware designed to steal confidential information from an infected machine, including passwords of email programs, ftp clients, browsers, and messengers.W97M.DownLoader.185
Representative of the family of malware that spreads primarily by email in Microsoft Word documents. It is designed to download other malicious applications during a computer attack.
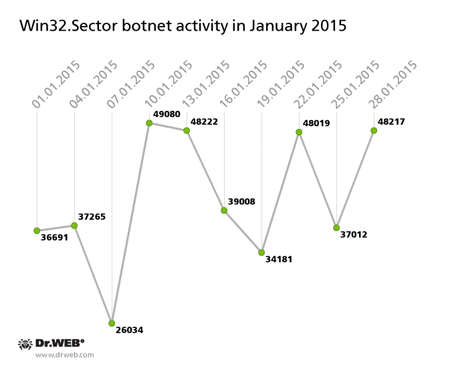
Botnets
Win32.Sector has been known since 2008 and is a complex polymorphic virus that can spread on its own (without user participation) and infect file objects.
Its key functions are to:
- download various executables via P2P networks and run them on infected machines;
- inject its code into running processes;
- terminate certain anti-viruses and block access to the sites of their respective developers;
- infect file objects on local disks and removable media (where during the infection process, it creates an autorun.inf file) as well as files stored in public network folders.
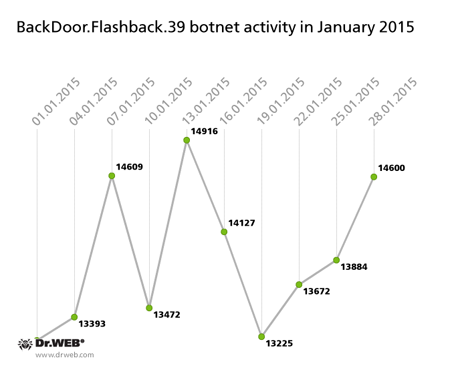
BackDoor.Flashback.39
The Trojan for Mac OS X which was distributed on a wide scale in April 2012. Infection was carried out via Java vulnerabilities. The purpose of this Trojan is to download and run a payload on an infected machine; the payload can be any executable file specified in the directive the Trojan receives from the hacker who controls it.
Threats to Linux
In January 2015 Doctor Web's security researchers discovered several new samples of malware for Linux, the most interesting of which is the file virus Linux.EbolaChan.
- The main purpose of Linux.EbolaChan is to execute the scheduled launch of a special script that downloads other sh-scripts from a criminal-owned, malicious website and executes those scripts on an infected machine.
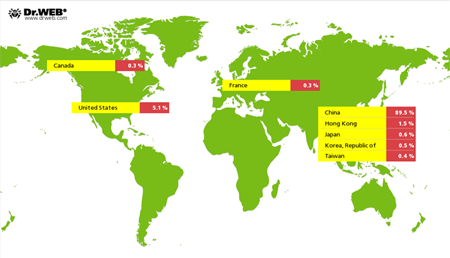
Still active, Linux.BackDoor.Gates.5 continues to carry out DDoS attacks on various Internet resources. In January 2015, Doctor Web's security researchers registered attacks on 5,009 unique IP addresses. As before, most of them are located in China:
Fraudulent and non-recommended sites
During January 2015, we added 10,431 Internet addresses to the Dr.Web database of non-recommended sites.
| December 2014 | January 2015 | Movement |
|---|---|---|
| 10 462 | 10 431 | +0,3% |
Parental Control, which is available in Dr.Web Security Space 10.0, can provide protection from various Internet scams. The Parental Control component lets you limit access to websites related to a certain topic and filter suspicious content. And, using its database of non-recommended URLs, the component can shield users from fraudulent sites, potentially dangerous and shocking content, and from sites which are known to distribute malware.
Learn more about Dr. Web non-recommended sites
Malicious and unwanted software threatening Android
In January 2015 a large number of new malware programs as well as other dangerous Android programs were detected. The newest among them are the following:
- Trojans spreading inside hacker-modified Android firmware;
- Banking Trojans
These malicious applications were particularly active in South Korea where they are spread with unsolicited short messages containing their download links.
We detected over 40 such spam campaigns involving several malicious programs.
Commercial spyware
In January, the Doctor Web virus database expanded with the addition of a large number of records for various commercial spyware applications designed to be installed on Android-powered devices and track their owners.Threats on Google Play
Aggressive and potentially dangerous advertising network modules for mobile devices remain an urgent problem. One such system has been implemented in a number of free programs hosted on Google Play.
Find out more about malicious programs for Android in our special overview.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live