January 21, 2015
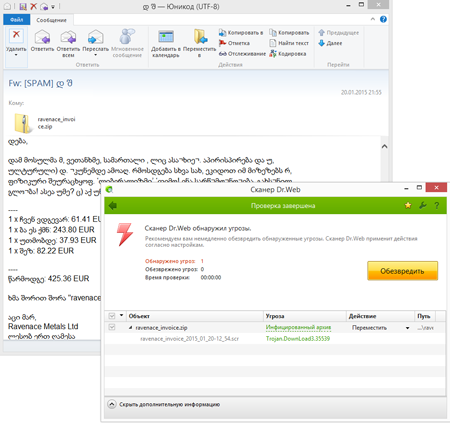
The downloader Trojan entered the Dr.Web virus database as Trojan.DownLoad3.35539. Criminals spread it as an attached ZIP archive in mass spam messages. According to Doctor Web security researchers, messages of this kind come in many languages including English, German and even Georgian.
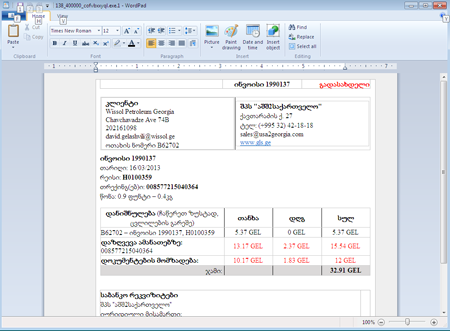
The archive contains an SCR file—by default, the .scr extension is utilised for Windows screen savers. These files are executable. If the archived file is launched, Trojan.DownLoad3.35539 extracts an RTF document from its body, saves it onto the hard drive and displays it on the screen.
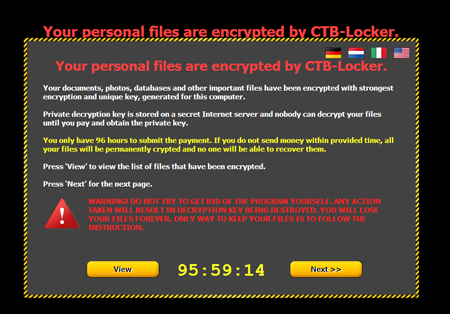
At the same time, Trojan.DownLoad3.35539 establishes a connection with one of the attackers' remote servers, downloads an archive containing the encryption ransomware Trojan.Encoder.686 (a.k.a. CTB-Locker), and then decompresses and runs it. Following its successful initialisation on the victim machine, Trojan.Encoder.686 encrypts files and displays the following message:
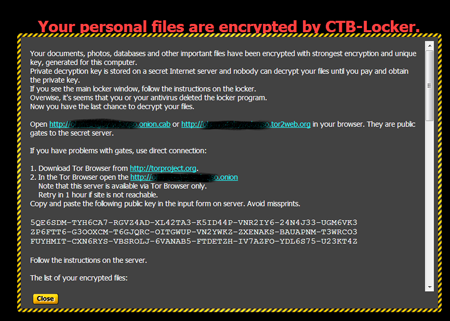
It is worth mentioning that attackers give their victims only 96 hours to pay the ransom required to recover their files and threaten that a failure to comply with their demands will result in permanent data loss. To acquire information about the terms and the ransom amount, users are directed to a site residing in the TOR network.
Trojan.Encoder.686 has been compiled using TOR and OpenSSL libraries and relies heavily on their encryption routines. While encrypting data, the ransomware makes use of CryptoAPI to generate random data as well as elliptic curve cryptography which for now makes it impossible to recover the affected data.
Doctor Web urges users to exercise caution and to never launch files received with emails, as well as to refrain from opening attachments in messages from unverified senders and to back up valuable data regularly.
In addition, please note that Dr.Web Security Space 9 and 10 incorporate several components that will facilitate automatic timely backups for your most valuable information and protect your computer from encryption ransomware and other malicious programs.
To keep your data safe, follow the recommendations below:
- Make sure that in the Dr.Web Security Space (9 and 10) settings, you toggle on the preventive protection which will protect your PC against threats yet unknown to Dr.Web.
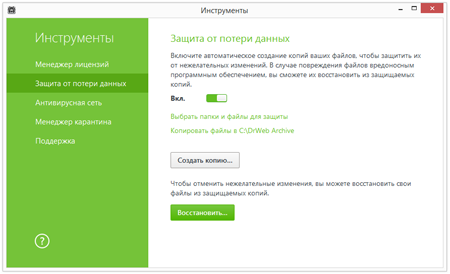
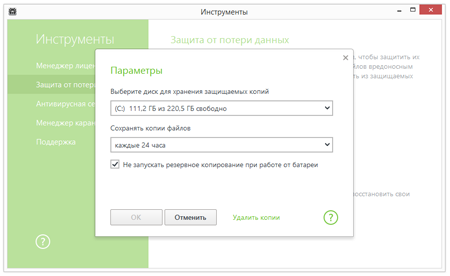
- Go to the ‘Tools’ menu to turn on ‘Data loss prevention’, and configure the parameters of the backup storage containing your important files.
- Create a custom schedule to back up your valuable data.
Supplemented by some caution when working with emails, these measures will keep your system safe from most modern threats including encryption ransomware.
Use Data Loss Prevention to protect your files from encryption ransomware
| Only available in Dr.Web Security Space 9 and 10 |
| Learn more about encryption ransomware |
 |
Configuration presentation tutorial |  |
Free decryption |

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments