December 29, 2014
Although incorporating malicious code in Android firmware is nothing new, criminals do not use this technique often. Yet, they don't discard it altogether, and security researchers occasionally come across a new Trojan for Android embedded in firmware or pre-installed on some handset model. In December several such incidents occurred. As before, the malicious programs detected were used by cybercriminals to covertly perform various actions to their advantage. In particular, the backdoor that entered the Dr.Web virus database as Android.Backdoor.126.origin could be instructed by criminals to add various text-specific SMS to the messages coming in on the infected mobile device. This feature provided criminals with the most diverse scam opportunities. Another malicious program lurking in Android firmware imparted its makers with an even more ample supply of features facilitating illicit activities. In particular, the program Android.Backdoor.130.origin (under the Dr.Web classification) could send short messages; make calls; display ads; download, install and launch applications without user consent; and transmit to its command and control (C&C) server all sorts of information including call history, SMS correspondence and location data. Furthermore, Android.Backdoor.130.origin could delete applications installed on the infected device. Since this backdoor was actually a system application, it didn't require user intervention to perform its tasks—this makes Android.Backdoor.130.origin particularly dangerous.
Android.SmsBot.213.origin, which can also perform unwanted actions on an infected device, is another noteworthy malicious program for Android that was detected in December. In particular, it could intercept and send SMS messages, and forward confidential information found on the device to its C&C server. Here, the main danger lies in the malware's ability to provide criminals with access to bank accounts involved in online banking. By sending and intercepting SMS messages used in remote banking, Android.SmsBot.213.origin could covertly transfer all the available funds to the attackers' account. Interestingly, criminals spread this program in the guise of a popular game which would eventually be installed onto the compromised device. In particular, once installed and launched by the user, Android.SmsBot.213.origin would begin installing the game that is incorporated into the malware, delete its shortcut and further operate as a system service. This trick helped criminals reduce the risk of users getting upset after failing to acquire an expected game and deleting the malware. It also improved the program's chances of successfully accomplishing its tasks.
 |
 |
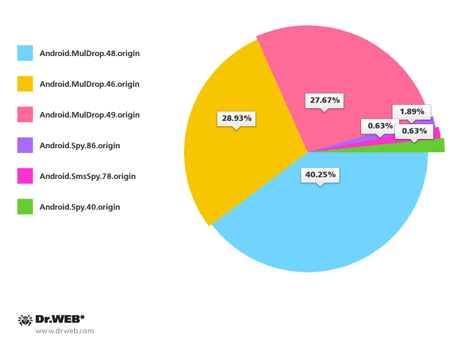
Also in December, cybercriminals targeting devices in South Korea carried on with their attacks. As before, they spread Android Trojans with unwanted SMS containing the relevant download links. Doctor Web registered about 160 spam campaigns of this sort throughout the month. The most common malicious programs spread in this way included Android.MulDrop.48.origin (40,25%), Android.MulDrop.46.origin (28,93%), Android.MulDrop.49.origin (27,67%) and Android.Spy.86.origin (1,89%).




![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments