Android malware steals money and confidential information
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
November 26, 2014
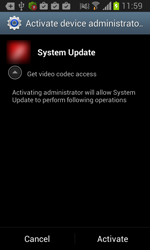
Android.BankBot.34.origin can only commence with its malicious activities after device owners install it on their handhelds. To increase the probability of the Trojan being installed and launched, Android.BankBot.34.origin is distributed in the guise of a system update and incorporates the icon of a popular legitimate program. It should be noted that the malware's disguise depends entirely on the intruders’ imagination and can be any application they want. After installation, the Trojan places its icon on the home screen. The icon can appear right next to the icon of the legitimate application if present in the system. This is how inexperienced users can confuse the applications and accidentally start the malware instead of the legitimate program. If the owner of the infected mobile device does not activate the malicious application after installing it, Android.BankBot.34.origin will still be launched automatically after a system restart.
When launched, Android.BankBot.34.origin prompts the user to grant it administrative privileges which can somewhat complicate its removal. Furthermore, if Android.BankBot.34.origin is launched by a device's owner, the malware will remove its previously created icon. The Trojan then commences its malicious activities.
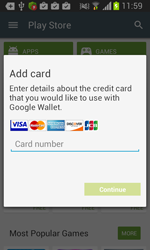
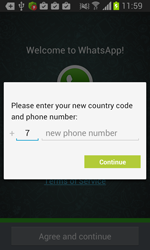
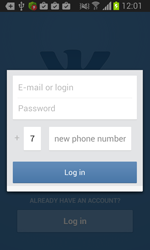
In fact, Android.BankBot.34.origin can implement two attack scenarios on an infected device. The first scenario depends on user behaviour and comes into play when the user attempts to start an application that is of interest to the intruders. If the owner of the infected smart phone or tablet launches such a program, Android.BankBot.34.origin displays a phishing dialogue box on top of the application's interface to prompt the user to divulge their confidential information—login and password, phone number, or credit card information. The malware imitates the dialogue boxes of the specific applications rather well, an indication that virus writers have committed significant resources toward ensuring that their victims remain unwary. To do so, criminals exploit the following mobile applications:
- Google Play;
- Google Play Music;
- Gmail;
- WhatsApp;
- Viber;
- Instagram;
- Skype;
- Vk;
- "Одноклассники";
- Facebook;
- Twitter.
Eventually, the data submitted by the user is forwarded to a remote server.
 |  |  |
The second attack scenario, on the contrary, does not rely upon user actions and is implemented solely in accordance with the instructions sent by the intruders via a remote host. In particular, a command and control (C&C) server can order Android.BankBot.34.origin to perform the following tasks:
- Start or stop intercepting inbound and outbound SMS.;
- Send a USSD query.
- Blacklist a specific number, so that all messages from that number are concealed from the user (by default, the list includes customer service numbers of certain carriers, a Russian online banking provider, and an e-commerce business);
- Clear the black list;
- Forward information about the applications installed on the device to the remote server;
- Send an SMS;
- Relay the malware’s ID to the server;
- Display a dialogue box or a message in accordance with parameters transmitted by the C&C server (e.g., a server instruction can specify the message text to be displayed on the screen, the number of input fields, etc.).
It is noteworthy that the address of the principal Android.BankBot.34.origin control server points to the anonymous Tor network. Furthermore, in order to use the corresponding secure protocol, the malware incorporates a piece of code from the official software that facilitates a connection to the hosts in the pseudo top-level domain .onion. This technique significantly improves security, so virus makers are tending to use it more frequently in malicious programs for Android.
Thanks to Android.BankBot.34.origin's ability to covertly send and intercept SMS, criminals can use the malware as a banking Trojan and send SMS commands used in online banking to steal money from bank accounts associated with compromised devices. Similarly, they can use USSD commands to transfer money from their victims' mobile accounts to their own. The list of targeted carriers and financial institutions is unlimited and can be changed depending on the malware makers’ current needs. In particular, customers of banks and e-commerce businesses that allow accounts to be managed via SMS face the biggest risk as do subscribers whose carriers let them transfer money from their mobile accounts.
Moreover, the malware’s ability to display on a mobile device any message or dialogue box of any form and content opens up almost unlimited opportunities for mounting the most diverse attacks. For example, criminals can steal the user's social networking credentials, change the password and instruct the malware to show messages like "Your account is locked; to have it unlocked, transfer funds to number 1234". The makers of Android.BankBot.34.origin can also "order" the Trojan to display a password prompt on behalf of a bank, allowing them to access the online banking account and gain control over a victim's funds. Therefore, the malware poses a severe threat to Android handhelds and their owners.
To avoid infection, Doctor Web recommends that users refrain from installing applications from dubious sources and disable the feature that lets them bypass Google Play to download software. In addition, when installing applications, pay attention to the list of features those applications will be accessing. If you have any doubts about a particular program, it is best not to install it.
An entry for detecting Android.BankBot.34.origin was promptly added to the virus database, so devices running Dr.Web for Android and Dr.Web for Android Light are well protected from this malware.