November 11, 2014
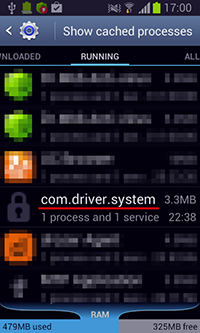
This new threat to Android is registered in the Dr.Web virus database under the name Android.Wormle.1.origin and comes with a wide array of features. After installation, the bot creates a shortcut on the home screen and operates as the system service com.driver.system.
Android.Wormle.1.origin connects to a command and control (C&C) server and awaits further directives from the intruders. It is noteworthy that cybercriminals can control the bot directly via their C&C server as well as via Google Cloud Messaging—a service that enables developers to communicate with their applications on targeted devices with active Google accounts.
This program has a very extensive set of features. In particular, it can perform the following tasks:
- Send an SMS with a given text to one or several numbers specified in a command;
- Send an SMS with a given text to all the phone numbers found in a phone book;
- Add a specific phone number onto the blacklist to block incoming SMS and calls from that number;
- Send a USSD query - (the target USSD number is blacklisted to ensure that the user won't get replies);
- Forward information about all received SMS messages and outbound calls to the C&C server;
- Toggle on the voice recorder or stop a recording in progress;
- Get information about accounts associated with an infected device;
- Get information about all the installed applications;
- Acquire contact information;
- Collect information about the mobile carrier;
- Determine the OS version;
- Determine the country in which the SIM card was registered;
- Determine the subscriber's phone number;
- Remove a specified application (to accomplish this, the bot displays a special dialogue box that forces the user to delete the program);
- Gather information about files and directories found on the SD card;
- Upload a zip-archive containing a file or folder, specified in an instruction, to the C&apm;C server;
- Delete a given file or directory;
- Delete all the SMS messages stored on a device;
- Mount a DDoS attack on a specified website;
- Establish a connection to the C&C server in accordance with special parameters;
- Change the control server address;
- Clear the blacklist.
Thus, with Android.Wormle.1.origin, criminals can accomplish a variety of tasks, ranging from sending paid SMS messages and stealing confidential data to orchestrating DDoS attacks on various websites. In addition, it can acquire bank account information which expands the program's scope of application even further.
Android.Wormle.1.origin operates as an SMS worm and spreads onto Android devices via SMS messages containing its download link. Such messages may look like this:
"I love you http://[]app.ru/*number*", where "number" is the recipient’s number.
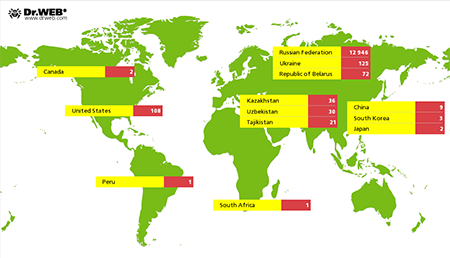
Messages like these are sent to all the numbers found in the phone book, so Android.Wormle.1.origin can infect a large number of devices in a short period of time and thus expand the botnet significantly. Statistics collected by Doctor Web indicate that, as of this moment, the malware has infected over 14,000 Android handhelds belonging to users residing in over 20 countries. Most of them—12,946 (91.49%)—reside in Russia, followed by Ukraine (0.88%), the USA (0.76%), Belarus (0.51%), Kazakhstan (0.25%), Uzbekistan (0.21%) and Tajikistan (0.15%). The Android.Wormle.1.origin botnet’s geography is presented in the figure below:
Doctor Web analysts are continuing to monitor the situation closely. An entry for detecting this malicious program has been added to the virus database, so devices running Dr.Web for Android and Dr.Web for Android Light are well protected from this malware.




![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments