Mobile threats in October 2014
Virus reviews | Hot news | Threats to mobile devices | All the news
November 5, 2014
Discovered in October, Android.Selfmite.1.origin is an Android threat designed to generate illicit profits. This malware is distributed in a tampered version of the official Google+ client application. The program's arsenal includes several money-generating features. First, once installed on an Android-powered smart phone or tablet, the program places several URL shortcut icons on the home screen which, depending on the device's location, lead to different websites promoted via various referral programmes and advertising networks. Every tap on an icons generates a profit for Android.Selfmite.1.origin‘s makers. Second, the malware is able to "advertise" certain applications available via Google Play by displaying respective sections of the software catalogue. Third, the malware can send SMS messages which, depending on what instructions it receives from a command and control server, may contain links to websites as well as download links for other applications and the malicious program itself. The main danger of Android.Selfmite.1.origin lies in its ability to send such messages to all the contacts found in a device's phone book. And, because the quantity of SMS is unlimited, the user could incur substantial financial losses and unwittingly help attackers spread this malicious application.
 |
 |
Another malicious profit maker discovered in October was dubbed Android.Dialer.7.origin under the Doctor Web classification system. This program belongs to the category of malicious diallers that earns money for criminals by calling premium numbers. When launched on an infected mobile device, Android.Dialer.7.origin dials a number specified in its settings, but it can also call other phones if commanded to do so by a command and control server. The Trojan has a number of features to help it stay operational as long as possible. In particular, the dialler's shortcut has neither an icon nor a caption, and once the program is launched, the shortcut is removed altogether, making Android.Dialer.7.origin "invisible" to the user. Also, the dialler removes information about all its calls from system logs and the call history. Moreover, the malware can resist its removal by preventing the user from accessing the corresponding system menu; therefore, Android.Dialer.7.origin poses a severe danger. More information about this threat can be found in the relevant publication on Doctor Web's site.
Another piece of Android ransomware created to help criminals make a living is the latest member of the Android.Locker family. Added to the Dr.Web virus database under the name Android.Locker.54.origin, it follows the well-tested pattern of locking the infected device's screen and demanding a ransom to unlock it. Unlike other similar programs, this ransomware can also send an SMS containing its download link to all the contacts found in a device's phone book. As a result, the devices affected were not only locked, but also could inadvertently contribute to the proliferation of the threat and increase the intruders’ chances of gaining illegal profits.
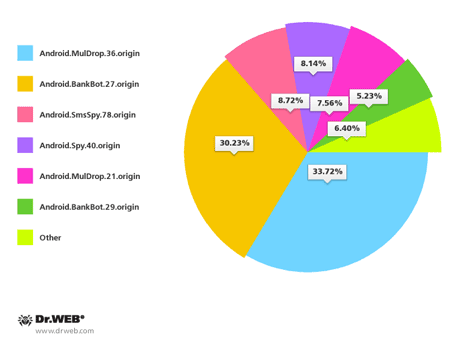
Criminals targeting users in South Korea were also rather active in October. Doctor Web registered over 170 spam campaigns organised to distribute various threats to Android. Most frequently, unsolicited short messages distributed download links for Android.BankBot.27.origin, Android.MulDrop.36.origin, Android.SmsSpy.78.origin, Android.Spy.40.origin, Android.MulDrop.21.origin and Android.BankBot.29.origin.
The new banking malware dubbed Android.BankBot.29.origin has been spreading in South Korea, too. It has been designed to steal authentication information from the clients of 17 financial institutions by simulating the operation of legitimate banking applications. To complicate its removal, Android.BankBot.29.origin like many other similar threats?attempts to acquire administrative privileges on a mobile device but does so in a peculiar fashion. In particular, it conceals the corresponding system prompt behind its dialogue box, so that the user is very likely to grant the requested permissions to the application.
 |
 |
Doctor Web continues to monitor the emergence of new Android threats and add the appropriate entries into the virus database to ensure that devices running Dr.Web Anti-virus for Android and Dr.Web for Android Light remain well protected.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live