October 27, 2014
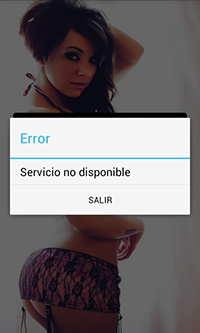
The malware for Android that entered the Dr.Web virus database as Android.Dialer.7.origin is a conventional malicious dialler, making calls to premium numbers. Spread in the guise of an application for adults, it places its shortcut, without an icon or any captions, on the home screen which can make users believe that the installation has failed. In some cases after its launch, Android.Dialer.7.origin can display an error message about the unavailability of the requested service, after which it hides its tracks in the infected system by deleting the shortcut, and operates in the guise of a system service. The service can be launched using the shortcut, but alternately the dialler can activate it automatically after a system restart, so it doesn't require user intervention to start its malicious activities.
 |
 |
The service started by Android.Dialer.7.origin periodically calls the number 803402470 which is stored in the dialler’s settings. However, if necessary, intruders can change the target phone number by issuing a corresponding command from the command and control server. This makes Android.Dialer.7.origin more flexible and enables criminals to profit from several chargeable services simultaneously.
To reduce the likelihood that users will detect its unwanted activities, the dialler disables the earpiece of the mobile device during unsolicited phone calls and removes all traces of its activities. It also clears the system log and call list of all damaging information.
However, the main distinguishing feature of this dialler is its ability to resist user attempts to remove it from an infected mobile device: whenever victims attempt to open the system settings section responsible for managing applications, Android.Dialer.7.origin redirects them to the home screen. In effect, manual removal of the malware becomes impossible.
Dr.Web anti-viruses detect and remove the dialler from protected mobile devices, so handhelds running Dr.Web for Android and Dr.Web for Android Light are well protected against this threat. If you are having trouble deleting Android.Dialer.7.origin, use the built-in emergency unlock feature and then repeat the scan and cure steps.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments