October 2, 2014
The number of new malicious programs for Android and the rate at which they emerge never cease to amaze information security experts. To a large extent, criminals are interested in these devices because they are extremely popular worldwide, and they offer cybercriminals lucrative opportunities. In particular, criminals are getting increasingly interested in mobile remote banking which must look particularly appetising to them. In September, Doctor Web's security researchers registered the emergence of new banking Trojans designed to gain unauthorised access to user accounts.
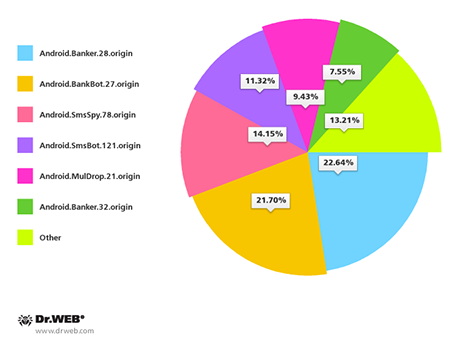
Many of the discovered threats targeted smart phones and tablet PCs in South Korea. Traditionally, most Android Trojans in this country are spread with unwanted SMS containing malware download links. In September, Doctor Web registered more than 100 of these spam campaigns. The most common malicious applications distributed by means of short messages included Android.Banker.28.origin (22.64%), Android.BankBot.27.origin (21.70%), Android.SmsSpy.78.origin (14.15%), Android.SmsBot.121.origin (11.32%), Android.MulDrop.21.origin (9.43%) and Android.Banker.32.origin (7.55%).
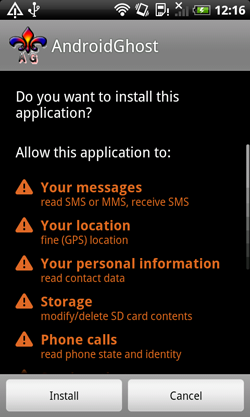
Users from China came under attack as well. Threats to Android examined by virus analysts in September include a spy Trojan that steals confidential information from devices found in China. Classified by Doctor Web as Android Spy.130.origin, this program is particularly dangerous because it provides attackers with information about SMS correspondence, the call history, current GPS coordinates and can also discreetly call a specified number, effectively turning an infected smart phone or tablet into an eavesdropping device.
Ransomware programs that lock Android handhelds and demand a ransom to unlock them are still quite popular, and their number is still growing. Android.Locker.38.origin somewhat stands out from the others, because—in addition to locking the screen and displaying a ransom demand—it is equipped with an extra extortion tool. Similarly to other programs of this kind, it gets onto a device in the guise of a harmless application (e.g., a system update) and, when launched, requests access to the handheld’s administrative features. Next, Android.Locker.38. origin locks it and demands a ransom.
 |
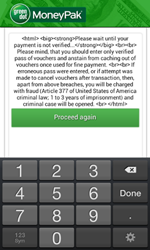 |
When the user attempts to revoke the permissions granted to the Trojan horse, the malware uses the standard system feature to lock the screen, and once it is unlocked it threatens the owner of the infected Android smartphone or tablet with wiping all the data stored on the device. If the user ignores the threat and revokes the privileges, Android.Locker.38.origin will set a password for switching the mobile device from the standby mode. Consequently, one may have to resort to a factory reset to regain control over the device. For more information about this Android threat, please refer to the corresponding publication.
Android.Elite.1.origin, on the other hand, wasn't designed for profit. However, it posed a severe threat to Android-based devices. Once launched on an infected smart phone or tablet, Android.Elite.1.origin wiped all the data from the memory card and also blocked a number of applications for online chat and SMS correspondence. Furthermore, this malicious program dispatched a bulk of short messages to all the contacts found in the phone book which could serve to rapidly empty the affected user's mobile account. Learn more about Android Elite.1.origin in our review.
 |
 |
Neither did criminals allow devices running iOS to go unnoticed. In September, the definition for a component of the malicious program IPhoneOS.PWS.Stealer.2, which targets jailbroken iOS devices, was added to the Dr.Web virus database. Discovered in spring 2014, the program steals authentication information including the App Store login and password, allowing criminals to purchase contents at their victims' expense.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments