September 29, 2014
Criminals developed this malware using C++ and Lua. It should also be noted that the backdoor makes extensive use of encryption in its routines. During installation it is extracted into /Library/Application Support/JavaW, after which the dropper generates a p-list file so that the backdoor is launched automatically.
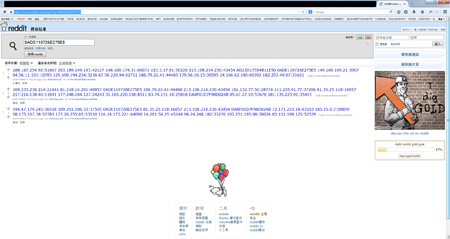
When Mac.BackDoor.iWorm is initially launched, it saves its configuration data in a separate file and tries to read the contents of the /Library directory to determine which of the installed applications the malware won't be interacting with. If ‘unwanted’ directories can't be found, the bot uses system queries to determine the home directory of the Mac OS X account under which it is running, checks the availability of its configuration file in the directory, and writes the data needed for it to continue to operate into the file. Then Mac.BackDoor.iWorm opens a port on an infected computer and awaits an incoming connection. It sends a request to a remote site to acquire a list of control servers, and then connects to the remote servers and waits for instructions. It is worth mentioning that in order to acquire a control server address list, the bot uses the search service at reddit.com, and—as a search query—specifies hexadecimal values of the first 8 bytes of the MD5 hash of the current date. The reddit.com search returns a web page containing a list of botnet C&C servers and ports published by criminals in comments to the post minecraftserverlists under the account vtnhiaovyd.
The bot picks a random server from the first 29 addresses on the list and sends queries to each of them. Search requests to acquire the list are sent to reddit.com in five-minute intervals.
While establishing a connection to the server whose address is picked from the list using a special routine, the backdoor attempts to determine whether the server address is on the exceptions list and engages in a data exchange with the server to employ special routines for authenticating the remote host. If successful, the backdoor sends the server information about the open port on the infected machine and its unique ID and awaits directives.
Mac.BackDoor.iWorm is able to perform two types of commands: different directives depending on the binary data provided and Lua scripts. Basic backdoor commands for Lua-scripts can be used to perform the following actions:
- Get the OS type.
- Get the bot version.
- Get the bot UID.
- Get a value from the configuration file.
- Set a parameter value in the configuration file.
- Remove all parameters from the configuration file.
- Get bot uptime.
- Send a GET query.
- Download a file.
- Open a socket for an inbound connection and then execute the commands received.
- Execute a system instruction.
- Sleep.
- Ban a node by IP.
- Clear the list of banned nodes.
- Get the node list.
- Get a node IP.
- Get node type.
- Get node port.
- Execute a nested Lua-script.
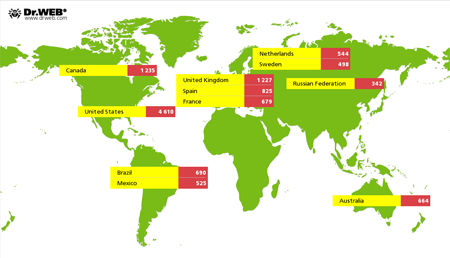
Information collected by Doctor Web's researchers shows that as of September 26, 2014, 17,658 IP addresses of infected devices were involved in the botnet created by hackers using Mac.BackDoor.iWorm. Most of them—4,610 (representing 26.1% of the total)—reside in the United States. Canada ranks second with 1,235 addresses (7%), and the United Kingdom ranks third with 1,227 IP addresses of infected computers (6.9% of the total). The late September 2014 geographical distribution of the botnet created with Mac.BackDoor.iWorm is shown in the following illustration:
The signature of this malware has been added to the virus database, so Mac.BackDoor.iWorm poses no danger to Macs protected with Dr.Web Anti-virus for Mac OS X.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments