September 1, 2014
Viruses
Statistics collected by Dr.Web CureIt! indicate that browser adware still leads in the rankings of the most frequently detected programs. As before, Trojan.BPlug.123, Trojan.BPlug.100, Trojan.BPlug.48, and the adware installer Trojan.Packed.24524 took the top spots.
The August list of detected threats, which was generated using information from the Dr.Web statistics server, differs little from the July list. As before, Trojan.Packed.24524, which installs unwanted programs in infected systems, ranked first. It accounted for almost 0.59% of all detections, against 0.56% in July. Trojan InstallMonster programs, which install unwanted applications under the InstallMonster referral programme, and various Trojan MulDrop Trojans are also among the leaders.
As in July, Trojan Redirect. 197, which redirects users to malicious sites, was most frequently detected in email traffic. The malicious downloader BackDoor.Tishop.122, which is distributed with spam messages, has moved into second position. It accounted for 1.6% of all incidents, compared with 1.15% in July. Various versions of Trojan.DownLoad programs and the dangerous banking malware Trojan.PWS.Panda were also actively distributed via email.
The size and behaviour of the botnets monitored by Doctor Web's security researchers also remained largely unchanged in August. Thus, on average, one of the two active Win.Rmnet.12 subnets experienced roughly 270,000 requests being made daily to the control server which is slightly higher than the July figure. The botnet created using the file infector Win32.Sector was still connecting 65,000-67,000 active bots every day. In contrast, the size of the botnet consisting of machines running Mac OS X and infected with BackDoor.Flashback.39 is gradually decreasing: in late August, it included about 13,000 infected machines, which is 1,000 fewer than the July figure.
Adware Trojans
Trojans showing annoying ads in pop-up windows or embedded in loaded web pages have recently been found in extremely large numbers. In terms of their prevalence, they are on par with encoders which encrypt user data stored in compromised systems. For already several months running, it is namely advertising Trojans that have been the absolute leaders in the statistics on threats detected by Dr.Web.
Trojans of this kind are usually spread by means of referral programmes which focus on generating income from file downloads. Advertising Trojans can be secretly installed along with other software. They often look like useful applications, but their developers add a malicious payload to the original legitimate features. Neither are criminals averse to using cyber fraud to spread this malware. For example, they create bogus file-sharing and torrent sites and lure their victims to those sites from fake forums and Q&A sites that have been optimised for specific search terms.
These malicious programs can be divided into two groups. The first includes representatives of the Trojan.BPlug family and also Trojan.Admess, Trojan.Triosir and Trojan.Zadved which are implemented as extensions to popular browsers and replace website advertisements or display pop-up banners. In such cases, users often do not even know that their machines have been infected.
This malware doesn’t just target Windows. Even Mac OS X machines have been impacted by specially designed and distributed Trojans from the Trojan.Downlite family that take the form of Safari and Google Chrome extensions.
Advertising Trojans belonging to the other group are much rarer and act autonomously, like normal malware. To replace web content, they resort to web injections which are often employed, for example, by banking Trojans. Once a web page is loaded by a browser, the malware embeds HTML or JavaScript code acquired from a command and control (C&C) server into the page and provides the browser with modified content. Trojan.Mayachok.18831 can serve as an example of a program that makes use of web injections .
In addition to displaying annoying ads, the program can modify social networking profile pages by publishing obscene photos and text and prompt the user to sign up for a paid subscription whenever they try to change their profile information. Trojan.Mayachok.18831 also has a range of other dangerous features which are described in detail in the corresponding Doctor Web review.
To avoid becoming an accidental victim of advertising Trojans, observe basic safety rules: do not download or install software from suspicious sources; do not run executable files distributed as email attachments; and, of course, always use up-to-date anti-virus software.
Threats of August
August witnessed numerous information security events involving the distribution of malware. For example, at the beginning of the month several users requested assistance from Doctor Web's support engineers to cope with another encryption Trojan. This incident would not have been out of the ordinary except for the fact that in all the cases, the encrypted files resided in Synology NAS storages. Trojan.Encoder.737 was the culprit behind the incident. It exploited a firmware vulnerability affecting DSM (DSM 4.3-3810 and earlier). More information about this event can be found in informational material published on Doctor Web's site.
Also in early August, security researchers discovered a clicker program designed to generate website traffic and fake banner clicks. The Trojan has been spreading under the Installmonster referral programme which specialises in distributing malware through gullible users. A description of this threat can be found in a Doctor Web review.
Chinese virus makers weren’t idle either; they made their mark in early summer by releasing an enormous quantity of Linux malware programs designed to mount DDoS attacks. By summer's end, these virus makers came up with ports of their malicious creations so that they could run them under Windows. Read more about this incident on Doctor Web's site.
The events of August
Many U.S. handhelds were compromised by Android.Locker.29.origin, a program that can lock devices and demand ransom to unlock them. According to information in the public domain, around 900,000 Android-powered devices were infected with this malware in August. The Trojan masquerades as anti-virus software and other legitimate applications. Originally Android.Locker.29.origin infected devices in Europe. However, recently virus makers designed a U.S. version. This is probably what caused the sharp increase in the number of infected smartphones.
In addition, a surge in infections of Android devices is expected thanks to the fact that the source code for Android.Dendroid.1.origin, a Trojan that steals confidential information and can make calls and open web pages without user knowledge or consent, was made available to the public in mid-August.
A spam mailing exploiting public interest in the Eastern Ukraine conflict was launched at the end of August. The spam contains download links for a program that is supposedly designed to mount DDoS attacks on Ukrainian government sites. In reality, the recipients of this spam download the malicious application BackDoor.Slym.3781 which then connects their infected computers to the Kelihos botnet and can control traffic and steal confidential information. The C&C servers communicating with the infected machines are located in Ukraine, Poland and the Republic of Moldova.
Threats to Android
As in previous months, in August cybercriminals again tried to infect mobile devices with various malicious applications, and the Dr.Web virus database expanded to include entries for a number of new Android Trojan horses.
For example, Chinese users had to deal with Android.smssend.1404.origin, which was designed to steal confidential information and install other malware onto mobile devices. This Trojan can also send short messages containing its download links. The malicious program it installs onto infected devices, which was added to the database under the name Android.SmsBot.146.origin, can execute commands issued by criminals and send and intercept SMS messages.
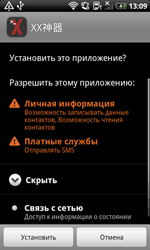 |
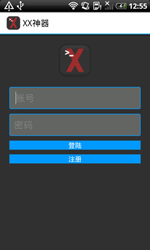 |
 |
August also had its share of ransomware that locks Android devices. Android.Locker.27.origin was one such program, but unlike many other species of this kind, it enabled users to unlock their devices completely for free. All they had to do was enter a 14-digit payment code that did not contain certain combinations of digits. If the requirements were met, the Trojan would unlock the device and remove itself. You can learn more about this Trojan in the relevant review on Doctor Web's site.
 |
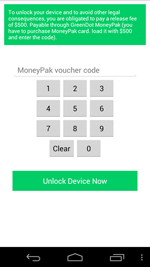 |
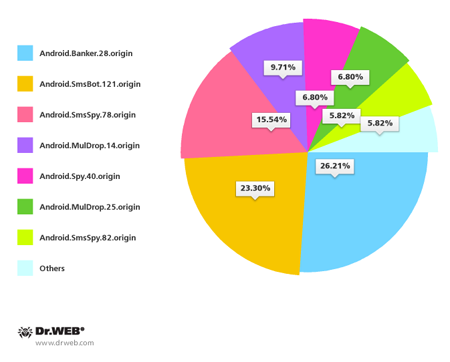
South Korean users also came under fire again. In August Doctor Web's security researchers registered over 100 spam campaigns aimed at spreading Android malware by means of SMS. Handhelds in South Korea were most endangered by Android.Banker.28.origin, Android.SmsBot.121.origin, Android.SmsSpy.78.origin and Android.MulDrop.14.origin.
Apart from actively using SMS, cybercriminals are also using other means to mass distribute malware. In the past month, information security experts learnt about a massive spam mailing containing a download link for the dangerous mobile backdoor Android.Backdoor.96.origin, which is distributed under the guise of anti-virus software and capable of performing a variety of malicious tasks on infected devices. In particular, it could steal confidential information including SMS messages, call and browser history, contact information and GPS data. It could also display various messages, send USSD queries, activate device microphones, and record phone calls into audio files for subsequent uploading, along with other acquired information, to a remote server.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments