Mac OS X Trojans display ads
Real-time threat news | Hot news | All the news | Virus alerts
April 16, 2014
On the official Apple forum, several Mac OS X users published complaints about annoying ads they’d seen displayed in Safari and Google Chrome windows while viewing various web resources. It turned out that the problem was being caused by malignant plugins that were installed onto people’s systems when they visited certain sites. The plugins are bundled and distributed with legitimate applications that are capable of performing useful tasks on computers.
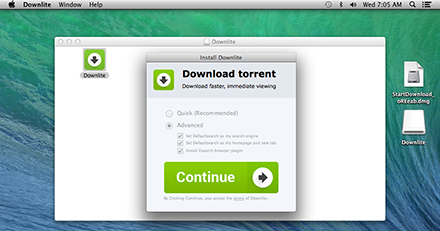
One such program called Downlite is spread via a popular torrent tracker site. As the user clicks Download, they are redirected to another site. It should be noted that the targeted redirect provides users of Mac OS X with the file StartDownload_oREeab.dmg—the Downlite installer—while users of other operating systems can be redirected to other sites. Once the file is downloaded, the installation of Downlite.app begins.
The installer (identified by Dr.Web as Trojan.Downlite.1) installs the legitimate application and several browser plugins. It also prompts the user to enter their password, and, if the user has administrative privileges, the applications will be installed into the root directory. To operate, DlLite.app requires Java; however, malicious plugins are written in Objective-C and start successfully when a browser window is opened. Also installed is the application dev.Jack which is designed to control Mozilla Firefox, Google Chrome and Safari. It is detected by Dr.Web anti-virus software as Trojan.Downlite.2.
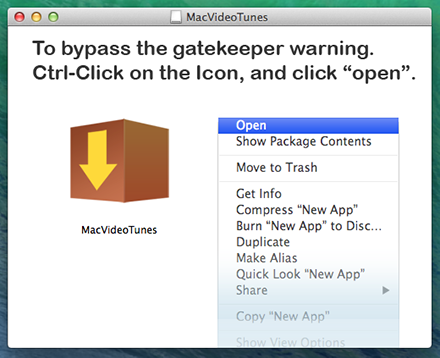
In addition, the advertising plugins are bundled with other applications (MacVideoTunes, MediaCenter_XBMC, Popcorn, and VideoPlayer_MPlayerX). MoviePlayer (MacVideoTunes) is one such application: during the first stage of its installation, the user is prompted to run the installer without a digital signature:
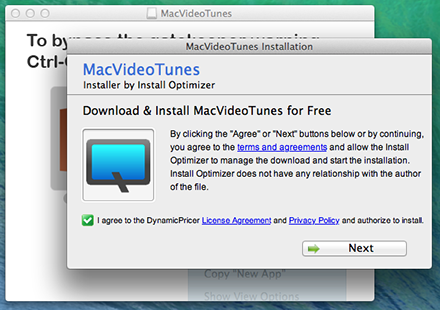
They are then invited to install an optimiser, but they are not allowed to clear the corresponding checkbox to decline the installation.
This installer, detected by Dr.Web Antivirus as Trojan.Vsearch.8, is very similar to Trojan.Downlite.1, but instead of dev.Jack, it installs takeOverSearchAssetsMac.app ( Trojan.Conduit.1 ).
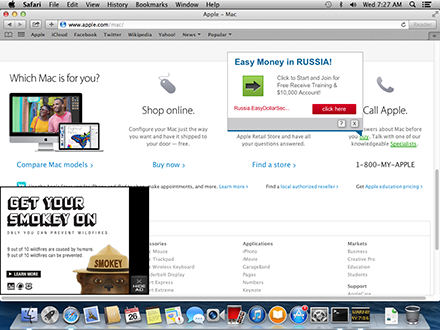
In all the aforementioned cases, the malicious payload installed in the system is implemented as the files VSearchAgent.app, VSearchLoader.bundle, VSearchPlugIn.bundle, libVSearchLoader.dylib and VSInstallerHelper. The outcome of all these manipulations is that annoying ads of the following types appear in browser windows:
- Underlined keywords; hovering the mouse cursor over such words invokes advertising pop-ups;
- A small window with the Hide Ad button displayed in the bottom left corner.
- Banners on search engine result pages and on popular sites.
Doctor Web recommends that users of Mac OS X refrain from downloading or installing applications from dubious sources, and use currentanti-virus software.