January 24, 2014
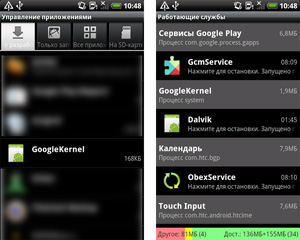
To spread the Trojan, which entered the Dr.Web virus database as Android.Oldboot.1.origin, attackers have used a very unusual technique, namely, placing one of the Trojan components into the boot partition of the file system and modifying the init script which is responsible for the initialisation of OS components. When the mobile phone is turned on, this script loads the code of the Trojan Linux-library imei_chk (Dr.Web Anti-virus detects it as Android.Oldboot.1), which extracts the files libgooglekernel.so (Android.Oldboot.2) and GoogleKernel.apk (Android.Oldboot.1.origin) and places them in /system/lib and /system/app, respectively. Thus, part of the Trojan Android.Oldboot is installed as a typical application which further functions as a system service and uses the libgooglekernel.so library to connect to a remote server and receive various commands, most notably, to download, install or remove certain applications. Reflashing a device with modified firmware that contains the routines required for the Trojan’s operation is the most likely way this threat is introduced.
This malware is particularly dangerous because even if some elements of Android.Oldboot that were installed onto the mobile device after it was turned on are removed successfully, the component imei_chk will still reside in the protected memory area and will re-install the malware after a reboot and, thus, re-infect the system.
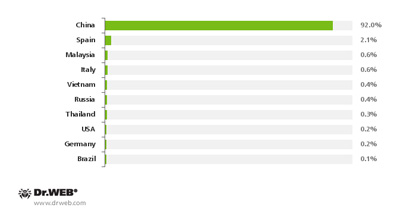
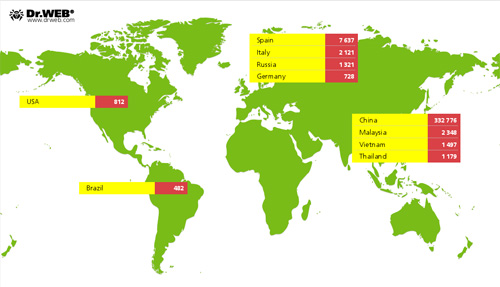
According to information acquired by Doctor Web's virus analysts, currently, this malignant program operates on more than 350,000 mobile devices belonging to users in various countries, including include Spain, Italy, Germany, Russia, Brazil, the USA and some Southeast Asian countries. However, most of the compromised devices (92%) are located in China, which is not surprising, since the Trojan Android.Oldboot is intended for Android-powered devices in China.
The geographical distribution of the compromised devices is shown on the following image.
To prevent infection by this malware or other similar Trojans, Doctor Web warns users against purchasing devices of unknown origin and using OS images from unreliable sources.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments