December 2, 2013
Viruses
According to statistics provided in November by Dr.Web CureIt!, the Trojan that entered the virus database as Trojan.Packed.24524 became the absolute leader among malware detected on PCs. This application has been detected on computers 12,450 times, accounting for 2.88% of the total number of identified threats. This nondescript name belongs to the installer of adware and other applications of dubious utility, which attackers spread under the guise of another, legitimate piece of software. If one launches such an installer on their computer, they run the risk of becoming the "lucky" user of several toolbars that will disfigure the browser window or of an application that will display annoying ads on the screen.
The advertising Trojans—Trojan.LoadMoney.1, Trojan.InstallMonster.38, Trojan.LoadMoney.225 and Trojan.InstallMonster.28—rank second through fifth in the November list of threats detected by Dr.Web CureIt!. The top twenty most frequently detected malignant programs, according to November statistics, are presented below:
| Name | Quantity | % |
|---|---|---|
| Trojan.Packed.24524 | 12450 | 2.88 |
| Trojan.LoadMoney.1 | 8281 | 1.91 |
| Trojan.InstallMonster.38 | 7719 | 1.78 |
| Trojan.LoadMoney.225 | 7712 | 1.78 |
| Trojan.InstallMonster.28 | 7069 | 1.63 |
| BackDoor.IRC.NgrBot.42 | 5990 | 1.38 |
| Trojan.LoadMoney.76 | 5819 | 1.35 |
| Trojan.Hosts.6815 | 5580 | 1.29 |
| Trojan.StartPage.56734 | 4840 | 1.12 |
| Trojan.Fraudster.502 | 4159 | 0.96 |
| Trojan.Siggen5.63980 | 3837 | 0.89 |
| Trojan.Fraudster.524 | 3835 | 0.89 |
| Trojan.Lyrics.11 | 3511 | 0.81 |
| BackDoor.Maxplus.24 | 3461 | 0.80 |
| Trojan.Hosts.6838 | 3074 | 0.71 |
| Win32.HLLP.Neshta | 2831 | 0.65 |
| Trojan.StartPage.52545 | 2743 | 0.63 |
| BackDoor.Andromeda.178 | 2351 | 0.54 |
| Trojan.Zekos | 2080 | 0.48 |
| Win32.HLLW.Gavir.ini | 2042 | 0.47 |
Botnets
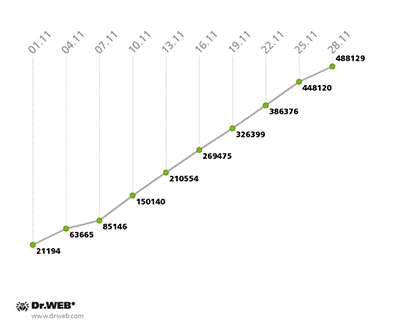
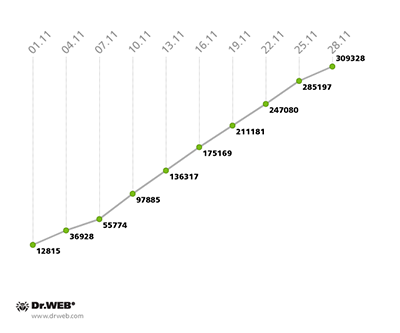
The growth rate of the botnet consisting of machines compromised by the file infector Win32.Rmnet.12 increased somewhat, with 20,000 new bots joining the first subnet daily in November against 15,000 new bots joining daily in October. In the second subnet, the figure also increased slightly—from an average of 11,000 to 12,500.
The growth of both Win32.Rmnet.12 subnets can be traced on the diagram below:
Win32.Rmnet.12 botnet growth in November 2013 (1st subnet)
Win32.Rmnet.12 botnet growth in November 2013 (2nd subnet)
The number of PCs on which Dr.Web anti-virus software detected Trojan.Rmnet.19 slightly decreased—from 3,851 in late October to 3,345 in November. The size of the botnet created by means of BackDoor.Bulknet.739 remained virtually unchanged in the past month: at the end of October, its total amounted to 1,539 infected machines, while in late November the figure dropped slightly to 1,270. The number of Macs on which anti-virus software is detecting BackDoor.Flashback.39 rose insignificantly in November—from 31,553 to 32,939. The largest number of infected Macs (16,928) is located in the United States; Canada ranks second (6,469 infected machines); and the United Kingdom ranks third (4,791 infection incidents). Australia ranks fourth for the number of infected Macs: 2,217.
The threat of the month
In early November, Doctor Web warned users about the distribution of another banking Trojan modification belonging to the family Trojan.PWS.Ibank. The main distinctive feature of this malware modification is its ability to verify the names of running programs and inject its code into their processes, particularly, into processes of the SAP business suite. This suite incorporates many modules, including components for managing taxation, sales and turnover. So infected machines can process very sensitive company information. The first version of the Trojan that checks whether SAP software is present in an infected system became widespread in June: it was added to the Dr.Web virus database as Trojan.PWS.Ibank.690. The latest modification is designated Trojan.PWS.Ibank.752. Trojan.PWS.Ibank Trojans can operate under 32-bit and 64-bit versions of Windows, and have a very wide range of malicious features which include:
- Stealing passwords entered by users and transferring the data to criminals.
- Blocking access to anti-virus company websites.
- Executing commands from a C&C server.
- Running a proxy server and a VNC server on an infected computer.
- Inflicting irreparable damage to the operating system or boot sectors.
To date, Trojans of the Trojan.PWS.Ibank family take no destructive action in respect of SAP software, but check whether it is present in an infected system and then try to inject their code into the corresponding process if it is running. It is possible that in the days to come virus makers intend to realise the malicious potential available to them. More information about this threat can be found in a review on Doctor Web's site.
Threats to Android
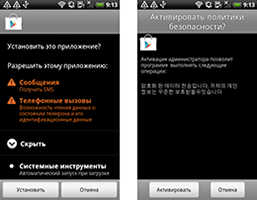
In November Doctor Web's virus analysts registered an increase in the number of Trojan spies stealing confidential information from mobile devices. Entries for several new versions of malware from the families Android.Spy, Android.SmsSpy and Android.Tempur — designed to intercept SMS messages and other personal information — were added to the Dr.Web virus database. These Trojans pose a severe threat because they intercept messages that may contain confidential information, personal and business correspondence, bank account information and mTAN codes used to verify transactions.
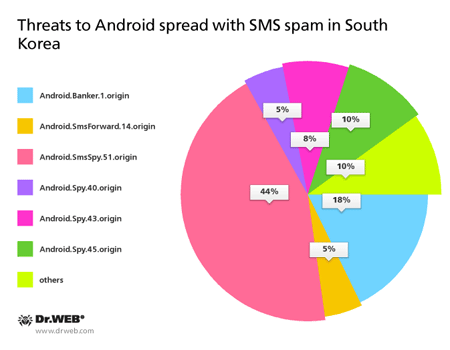
The geographical spread of these malicious programs encompasses many countries, however, a considerable proportion of them is found in South Korea. It is noteworthy that in this region, mobile Trojans usually get to target devices by means of unwanted SMS messages containing a link to download a malicious application. Over the past month, Doctor Web's analysts discovered more than a hundred incidents when such programs were spread with a bulk of short messages. The chart below provides information about the percentage of Android threats distributed in South Korea in November.
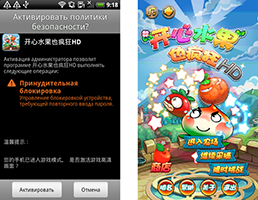
In the last month, Chinese users weren't overlooked either by cybercriminals. In November Doctor Web's analysts found a new representative of the famous family of malware Android.SmsSend, which was added to the virus database as Android.SmsSend.946.origin. This particular Trojan was distributed on various Chinese websites providing access to software for Android. To increase the likelihood of infection, attackers employed a technique which is widely used by criminals in China—namely, embedding Trojan code in several popular games. Once on a mobile device, Android.SmsSend.946.origin can covertly send premium messages and thus subscribe the user to unwanted services.
Other threats in November
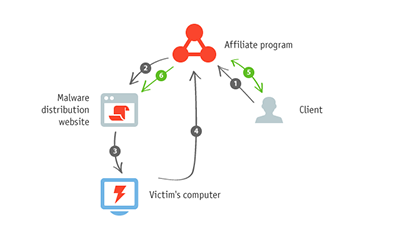
Multiple incidents involving Trojan.Hiloti spreading from compromised sites were discovered by Doctor Web's analysts in the middle of the month. This threat generates fake search results in a compromised system. Attackers offer the malware’s distributors a fairly simple working scheme:
1 - A customer enters into an agreement with an affiliate programme’s organisers to promote certain URLs. 2 - The affiliate programme’s organisers deliver malware to distributors who make sure it can be downloaded from various sites. 3 - When users visit such sites, their computers get infected with the malware. 4 - When the users resort to the help of search engines, they end up clicking on links displayed by the malicious software in the browser window. The information is transmitted to the affiliate programme’s organisers. 5 - The customer pays the affiliate programme’s organisers for clicks on the links. 6 - The malware distributors get their portion of these funds.
The vulnerabilities CVE-2012-4969, CVE-2013-2472, CVE-2013-2465 and CVE-2013-2551 are exploited and social engineering techniques are used to facilitate the downloading of the Trojan on target machines. For more information about the incident, you can refer to informational material published by Doctor Web in the past.
Also discovered in November was a mass distribution via Skype of a banking Trojan from the family BackDoor.Caphaw. Messages that were sent to users included a link to an archive with the name invoice_XXXXX.pdf.exe.zip (where XXXXX is an arbitrary string of digits). In turn, the archive contained an executable file — the Trojan program BackDoor.Caphaw.
Malware of the BackDoor.Caphaw family have a wide array of malignant features and pose a severe security threat. A detailed description of the threat and information about how to neutralise it is presented in a related article published on Doctor Web's site.
In pursuit of profit, cybercriminals usually stop at nothing, trying all possible ways to mislead potential victims and to lure them into installing malicious software on their computers. Distributors of Trojan.Lyrics, which displays annoying ads in browser windows, do the same thing.
With this program, music lovers will supposedly be able to play any song posted on YouTube and read the lyrics at the same time—i.e., turn watching videos into a karaoke experience. Links to download this program can be found on various torrent, music and social networking sites. Trojan.Lyrics can be downloaded from several official websites of its developers, but it is more often secretly installed on computers along with free software downloaded from the Internet. Recently, analysts registered a significant increase in the number of incidents involving infection with this malware.
Malicious files detected in mail traffic in November
| 01.11.2013 00:00 - 30.11.2013 23:00 | ||
| 1 | Trojan.DownLoad3.28161 | 1.59% |
| 2 | Trojan.DownLoad3.30075 | 0.92% |
| 3 | Trojan.DownLoader9.22851 | 0.84% |
| 4 | Trojan.DownLoader10.50838 | 0.63% |
| 5 | Trojan.PWS.Panda.4795 | 0.57% |
| 6 | BackDoor.Maxplus.13093 | 0.54% |
| 7 | BackDoor.Maxplus.13104 | 0.52% |
| 8 | BackDoor.Maxplus.13201 | 0.50% |
| 9 | Trojan.Packed.25001 | 0.49% |
| 10 | Trojan.PWS.Panda.547 | 0.47% |
| 11 | Trojan.PWS.Panda.2401 | 0.47% |
| 12 | BackDoor.Maxplus.13177 | 0.45% |
| 13 | Trojan.Oficla.zip | 0.42% |
| 14 | Win32.HLLM.MyDoom.33808 | 0.42% |
| 15 | Trojan.DownLoad.64687 | 0.39% |
| 16 | Trojan.DownLoad.64697 | 0.39% |
| 17 | Trojan.Winlock.8811 | 0.37% |
| 18 | Trojan.PWS.Multi.911 | 0.37% |
| 19 | Trojan.Inject.64578 | 0.36% |
| 20 | Trojan.Fraudster.517 | 0.36% |
Malicious files detected on user computers in November
| 01.11.2013 00:00 - 30.11.2013 23:00 | ||
| 1 | Trojan.Fraudster.524 | 0.60% |
| 2 | Trojan.LoadMoney.225 | 0.52% |
| 3 | BackDoor.PHP.Shell.6 | 0.48% |
| 4 | Trojan.InstallMonster.38 | 0.45% |
| 5 | Trojan.Fraudster.589 | 0.45% |
| 6 | Trojan.Fraudster.502 | 0.45% |
| 7 | BackDoor.IRC.NgrBot.42 | 0.38% |
| 8 | Trojan.InstallMonster.28 | 0.36% |
| 9 | Trojan.LoadMoney.188 | 0.36% |
| 10 | Trojan.Packed.24524 | 0.34% |
| 11 | Trojan.LoadMoney.227 | 0.31% |
| 12 | Win32.HLLW.Shadow | 0.29% |
| 13 | Trojan.LoadMoney.1 | 0.26% |
| 14 | Trojan.Fraudster.430 | 0.25% |
| 15 | Trojan.MulDrop4.25343 | 0.25% |
| 16 | Win32.HLLW.Autoruner.59834 | 0.25% |
| 17 | Trojan.LoadMoney.224 | 0.24% |
| 18 | Trojan.Hosts.6838 | 0.23% |
| 19 | Trojan.Packed.24814 | 0.23% |
| 20 | Trojan.SMSSend.4196 | 0.21% |



![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments