July 1, 2009
Doctor Web presents a virus activity review for June 2009. The last month proved that e-mail remained one of the best means for quick distribution of malware all over the Internet. Doctor Web virus monitoring service also registered a surging number of phishing attacks targeting customers of online banking and electronic payment systems. Cyber-criminals tended to become more interested in multi-platform malware.
Viruses via e-mail
Mail viruses came into the spotlight in the first days of June. The last month saw the biggest number of messages with attached malware or message providing links to malware downloads registered in this year. Cyber-criminals employed various techniques to attract users’ attention to malicious e-mails and to trick them into opening attached files.
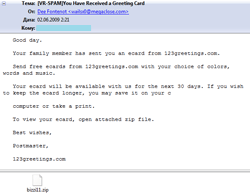
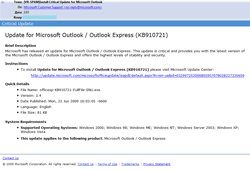
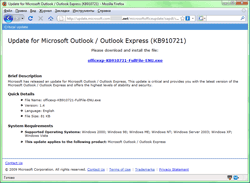
Most e-mails from cyber-criminals were plain-text. However, some of them featured design of e-mails from respected companies like Microsoft.
 |
 |
Malicious files were spread as attachments or a user received a link. Clicking on it started downloading of a virus but there were few virus-makers that used bogus web-sites to spread malware in June.
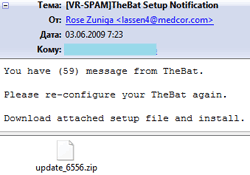
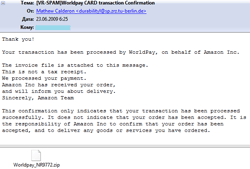
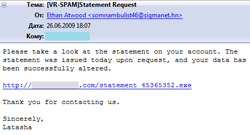
Messages were devoted to different topics. Many of them were greeting cards notifications. By now e-cards remain the most popular disguise. Cases of Trojans offered to victims as updates of e-mail clients (Microsoft Outlook, Ritlabs The Bat!) or as video codecs were more rare. Some users received messages concerning paid orders from an e-store. A user was informed about changes of parameters of his account (a message didn’t specify a payment system or any other online services web-site though).
 |
 |
 |
 |
In June e-mail was used to spread a wide range of malicious programs. Trojan.PWS.Panda.122 hidden with various packers became the leader among mailed malware that also included Trojan.Siggen.2447, Trojan.DownLoad.29459, Trojan.DownLoad.38602, Trojan.Fakealert.4471 and others.
At the end of June virus analysts also registered mailing of messages that contained links to web-sites advertising healthcare products. A wide variety of malicious programs and topic of messages featuring similar design show that several groups of cyber criminals are involved in distribution of malware over e-mail.
Multi-platform malware
In recent months virus makers showed growing interest in designing cross-platform malware that enabled them to target multiple computer platforms. Earlier there were quite few cross-platform implementations of malware (virus makers made several attempts to create viruses that would run under Windows as well as under Linux). However, nowadays the number of such malicious programs is growing.
The April virus activity review from Doctor Web described the Trojan.BrowseBan program that could be installed as a plugin for both Opera and Mozilla Firefox.
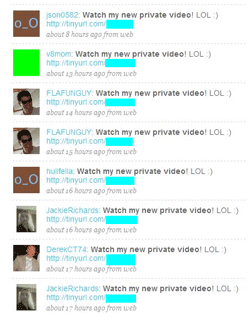
In June cyber-criminals shifted their aim towards users of Twitter. Given that the microblogging service has several millions of users worldwide and blogs are interconnected, a message with a link to a malicious program in one microblog followed by thousands of bloggers make all those bloggers potential targets of a virus attack.
It should also be noted that users of Twitter can be found among PC users as well as among those who prefer Mac which virus makers also took into account. The attack that was carried out June targeted PCs as well as Macs and the bogus web-site to which a victim was redirected detected the operating system of a target machine automatically and provided different files for downloading for different platforms.
Since Twitter post length is limited to 140 characters, malefactors often resorted to services that enabled them to use short aliases instead of long URL ((http://tinyurl.com, http://bit.ly) to direct users to malicious sites. Besides, a shortened link makes it hard to tell if it points to something nasty and therefore increases efficiency of an attack. Even though administration of some of the services attempt to monitor how the service is used, but such services play into hands of virus makers more often than not.
Another massive spreading of links to a fraudulent web-site over Twitter took placeat the end of June. This time Win32.Virut.56 was offered to users as a codec required to view a video clip.
Social networking web-sites
Popularity of social networking web-sites grows steadily among users as well as amid cyber-criminals striving to put their malicious plans into action. Trojan.Hosts and Trojan.Facebook became the most popular choices for cyber-criminals spreading malware over such web-sites.
Once installed Trojan.Hosts modifies the hosts file to redirect a user to a bogus web-site where a victim is offered a paid SMS registration on a social networking web-site.
Trojan.Facebook uses contacts information found in the compromised system to send a link to a supposed video codec to other users of a social networking resource. Of course, the codec is nothing more than the malicious program itself. When installed, it follows the same procedure.
Methods employed by cyber-criminals willing to spread malware over social networking web-sites or other similar means of communication (e.g instant messaging services, e-mail, etc.) do not change with the time. As a rule it is a download link or an attachment.
Users who have already been tricked into downloading malware by such messages can instantly tell if a message has been sent by a cyber criminal. That’s why targets of virus-makers are only new users but there are a lot of new-joiners every day.
Even though social networking web-sites are becoming more and more popular and their users grow in numbers, threats related to such web-resources are really view compared with the total number of malicious programs currently in the wild. The reason behind users knowing about Trojans links in messages but remaining unaware of viruses that travel between computers over removable data-storage devices is that social networking web-sites often become a topical issue for the media.
Spam
Spammers never hesitate to exploit breaking news in their mailings. In a few hours after death of Michael Jackson became known to the public it became one of the main subjects of spam e-mails replacing supposed news about events related to the latest Iran presidential election.
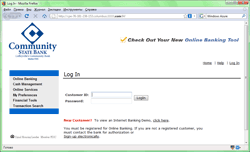
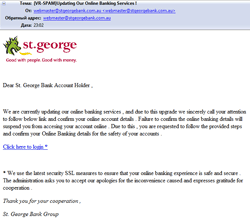
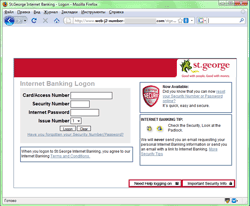
A number of phishing attacks also surged up .in June. The total amount of phishing e-mails increased as well as the target group that included customers of Bank of America, JPMorgan Chase Bank, Community State Bank, and St. George Bank as well as people that use PayPal, eBay and Amazon customers.
 |
 |
 |
 |
Malicious files detected in mail traffic in June
| 01.06.2009 00:00 – 01.07.2009 00:00 | ||
| 1 | Win32.HLLM.Netsky.35328 | 7128037 (25.13%) |
| 2 | Trojan.DownLoad.36339 | 5366428 (18.92%) |
| 3 | Win32.HLLM.MyDoom.33808 | 2716995 (9.58%) |
| 4 | Win32.HLLM.Beagle | 2205546 (7.78%) |
| 5 | Trojan.Botnetlog.9 | 1868590 (6.59%) |
| 6 | Win32.HLLM.MyDoom.based | 1653007 (5.83%) |
| 7 | Trojan.MulDrop.19648 | 843626 (2.97%) |
| 8 | Win32.HLLM.Beagle.32768 | 708903 (2.50%) |
| 9 | Trojan.MulDrop.13408 | 640380 (2.26%) |
| 10 | Win32.HLLM.MyDoom.44 | 536518 (1.89%) |
| 11 | Win32.HLLM.MyDoom.49 | 458717 (1.62%) |
| 12 | Win32.HLLM.Beagle.27136 | 453649 (1.60%) |
| 13 | Win32.HLLM.Perf | 446777 (1.58%) |
| 14 | Trojan.PWS.Panda.114 | 389041 (1.37%) |
| 15 | Exploit.IframeBO | 341159 (1.20%) |
| 16 | Win32.HLLM.MyDoom.54464 | 276624 (0.98%) |
| 17 | Win32.HLLM.Netsky.based | 256594 (0.90%) |
| 18 | Win32.HLLM.Beagle.pswzip | 255040 (0.90%) |
| 19 | Exploit.IFrame.43 | 247345 (0.87%) |
| 20 | Trojan.PWS.Panda.122 | 243606 (0.86%) |
| Total scanned: | 126,767,994,680 |
| Infected: | 28,362,114 (0.0224%) |
Malicious files detected on user machines in June
| 01.06.2009 00:00 - 01.07.2009 00:00 | ||
| 1 | Trojan.DownLoad.36339 | 4285602 (17.70%) |
| 2 | Trojan.Botnetlog.9 | 2539980 (10.49%) |
| 3 | Win32.HLLM.Beagle | 1746450 (7.21%) |
| 4 | Win32.HLLM.Netsky.35328 | 811987 (3.35%) |
| 5 | Win32.HLLW.Gavir.ini | 807672 (3.34%) |
| 6 | Win32.Virut.14 | 803513 (3.32%) |
| 7 | Win32.HLLW.Shadow.based | 641590 (2.65%) |
| 8 | Win32.HLLM.MyDoom.49 | 614335 (2.54%) |
| 9 | DDoS.Kardraw | 581880 (2.40%) |
| 10 | Trojan.MulDrop.16727 | 499697 (2.06%) |
| 11 | Win32.HLLM.MyDoom.33808 | 428111 (1.77%) |
| 12 | Trojan.WinSpy.145 | 424441 (1.75%) |
| 13 | Trojan.DownLoad.35128 | 381925 (1.58%) |
| 14 | VBS.Generic.548 | 366961 (1.52%) |
| 15 | Trojan.DownLoader.42350 | 362862 (1.50%) |
| 16 | Win32.HLLW.Autoruner.5555 | 279066 (1.15%) |
| 17 | W97M.Thus | 253182 (1.05%) |
| 18 | Trojan.PWS.Panda.122 | 242922 (1.00%) |
| 19 | Win32.Sector.17 | 242790 (1.00%) |
| 20 | Trojan.AuxSpy.13 | 242588 (1.00%) |
| Total scanned: | 185,717,797,971 |
| Infected: | 24,208,981 (0.0130%) |

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments