June 1, 2009
Doctor Web presents the virus activity review for May 2009. In the past month the share of ransomware among other malicious programs remained the same but virus makers honed their social engineering techniques and created new tools that would make their work easier. May also saw several new rootkits. Spammers were even more eager to advertise their services using new ways to bypass spam-filters.
Ransomware
As development of malicious programs became purely commercial, a new type of virus threats — ransomware — emerged in the Internet.
The first species of this type of malware were discovered in 2005. They were followed by Trojans that could encrypt files on a compromised machine and provide a victim with a ransom note offering to contact the virus maker to decrypt compromised data. In later versions of such malicious programs the note explicitly stated the amount one had to pay and how he could do that. These programs entered the Dr.Web classification as Trojan.PGPCoder and Trojan.Encoder with its numerous modifications. Special decryption utilities from Doctor Web are available for free download from the company web-site.
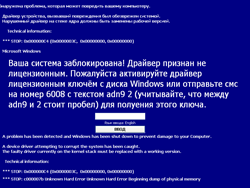
Even though Trojans locking the screen in Windows became known to the wide audience only in 2009, the first samples of such malicious programs (Trojan.Winlock) appeared in 2005, at the same time as Trojans encrypting user data.
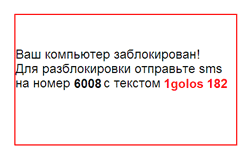
Later cyber-criminals chose to simplify the money transfer procedure and offered victims all over the world to send paid SMS.
Following the pattern new malicious programs appeared in 2008 (Trojan.Blackmailer). This time users had to pay for removal of an adult content banner displayed on every loaded web-page. Most of the Trojans targeted users of Internet Explorer. However, later variations of the blackmailer program could also jar on nerves of web-surfers using Mozilla Firefox and Opera.
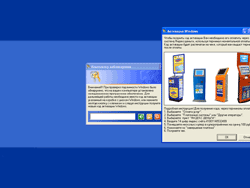
Authors of the new modification of Trojan.Winlock that locked the screen under Windows also chose paid SMS as the most convenient way to receive a ransom. Users whose machines have been compromised by the Trojan can use the special generator on the site of Doctor Web to unlock their systems. To ensure detection of numerous modifications of Trojan.Winlock virus analysts of the company created the special Trojan.Winlock.origin definitions that allow Dr.Web anti-viruses to detect modifications of the Trojan that have not been analyzed in the virus laboratory.
Latest modifications of Trojan.Winlock were somewhat more intimidating. They featured a countdown timer and warned a user against reinstalling the system that would allegedly lead to data losses.
Virus analysts also discovered many imitations of Trojan.Winlock. Such malicious programs were less sophisticated with the unlock password specified in the code of the Trojan. Some of these Trojans were never meant to unlock a system. ending an SMS at the suggested number would increase the rating of the virus maker on one of social networking web-sites but the system would still be locked.
Another innovation from the virus makers was a constructor of Trojans locking Windows systems that enabled them to create new versions of the Trojan with different ransom notes.
New versions of the GUI scanner
Aiming to ensure detection of the BackDoor.Maosboot rootkit and Trojan.AuxSpy, Doctor Web updated its scanner for Windows several times in May.
Trojan.AuxSpy blocks launch and disrupts operation of several utilities (.e that could help neutralize the malicious program Even though the Trojan doesn’t run in the system kernel mode, it adds its entry into the system Registry and can restore itself from the memory.
Malicious programs like these show that in order to remain protected users need to update software components of their anti-viruses as well as virus databases.
Safari vulnerability.
Vulnerability in the libxml library of Apple Safari 3.2.3 was discovered in the middle of May. It allows arbitrary code execution on the target machine if a user loads a specifically designed web-page. More detailed information about the vulnerability can be found in the Apple security bulletin dated of 12.05.2009. Note the vulnerability is relevant for the version of Safari for Mac OS X as well as for the Windows version. The vulnerability can also be used to install other malicious programs in the compromised system.
Cyber-criminals tend to pay more attention to Mac OS X as it becomes more popular.
Spam
The total amount of spam messages in May remained the same. However, the number of messages aiming to attract new customers willing to use services of spammers increased. Arguments aiming to encourage potential customers include supposedly high efficiency of this kind of advertising, its legitimacy, examples of large business customers, etc. Of course, most of the claims (if not all of them) have nothing to do with the truth.
The number of messages offering to make easy money in the Internet also kept growing. Many users now know better than to get involved in such dubious schemes. But the increasing share of such messages in the total amount of spam showed that analysts of Doctor Web came to the right conclusion.
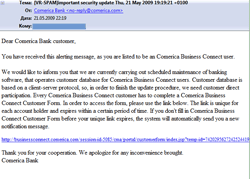
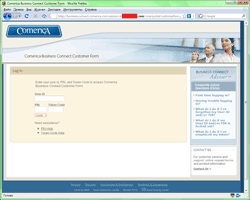
In spite of their low efficiency fishing attacks didn’t stop either. Preferences of cyber-fraudsters tend to shift towards users of online banking. In May customers of Comerica became the main targets of phishing attacks.
|
|
Malicious files detected in mail traffic in May
| 01.05.2009 00:00 - 01.06.2009 00:00 | ||
| 1 | Win32.HLLM.Netsky.35328 | 14813173 (41.31%) |
| 2 | Win32.HLLM.Beagle | 3612033 (10.07%) |
| 3 | Win32.HLLM.MyDoom.33808 | 3554352 (9.91%) |
| 4 | Win32.HLLM.Netsky.28672 | 2425299 (6.76%) |
| 5 | Win32.HLLM.MyDoom.44 | 1568617 (4.37%) |
| 6 | Win32.HLLM.Netsky.based | 1403727 (3.91%) |
| 7 | Win32.HLLM.Perf | 1056208 (2.95%) |
| 8 | Win32.HLLM.MyDoom.based | 820918 (2.29%) |
| 9 | Trojan.MulDrop.19648 | 661200 (1.84%) |
| 10 | Win32.HLLM.Beagle.32768 | 627811 (1.75%) |
| 11 | Trojan.MulDrop.13408 | 626816 (1.75%) |
| 12 | Win32.HLLM.Netsky | 578837 (1.61%) |
| 13 | Win32.HLLM.MyDoom.49 | 554956 (1.55%) |
| 14 | Exploit.IFrame.43 | 481410 (1.34%) |
| 15 | Trojan.PWS.Panda.114 | 391321 (1.09%) |
| 16 | Win32.HLLM.Beagle.27136 | 378735 (1.06%) |
| 17 | Win32.HLLM.Netsky.28008 | 362897 (1.01%) |
| 18 | Win32.HLLM.Graz | 277064 (0.77%) |
| 19 | Win32.HLLM.Beagle.pswzip | 260037 (0.73%) |
| 20 | Exploit.IframeBO | 175968 (0.49%) |
| Total scanned: | 163,867,066,697 |
| Infected: | 35,861,521 (0.0218%) |
Malicious files detected on user machines in May
| 01.05.2009 00:00 - 01.06.2009 00:00 | ||
| 1 | Win32.HLLW.Shadow.based | 2347116 (18.99%) |
| 2 | Win32.HLLW.Gavir.ini | 723353 (5.85%) |
| 3 | Trojan.AuxSpy.13 | 506981 (4.10%) |
| 4 | VBS.Generic.548 | 285643 (2.31%) |
| 5 | Win32.HLLW.Autoruner.2536 | 274582 (2.22%) |
| 6 | Win32.HLLW.Autoruner.5555 | 270656 (2.19%) |
| 7 | DDoS.Kardraw | 248823 (2.01%) |
| 8 | Trojan.DownLoad.35128 | 243625 (1.97%) |
| 9 | Trojan.DownLoader.42350 | 225703 (1.83%) |
| 10 | Win32.Sector.17 | 219578 (1.78%) |
| 11 | Win32.Alman | 210942 (1.71%) |
| 12 | Trojan.Starter.544 | 206115 (1.67%) |
| 13 | Win32.Virut.14 | 198389 (1.61%) |
| 14 | Win32.HLLM.Netsky.35328 | 196459 (1.59%) |
| 15 | Win32.HLLM.Beagle | 155071 (1.25%) |
| 16 | Trojan.AuxSpy.15 | 143727 (1.16%) |
| 17 | Win32.HLLW.Autoruner.274 | 136360 (1.10%) |
| 18 | Trojan.Botnetlog.9 | 131285 (1.06%) |
| 19 | Trojan.AuxSpy.7 | 122566 (0.99%) |
| 20 | Trojan.DownLoad.36194 | 121743 (0.99%) |
| Total scanned: | 99,061,889,355 |
| Infected: | 12,358,946 (0.0125%) |


![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments