January 14, 2013
The largest botnet for Mac OS X
Perhaps the most dramatic event of 2012 in the field of information security was the emergence of the Trojan Backdoor.Flashback.39 Backdoor. Flashback. 39which provoked a real epidemic among Apple-compatible computers. Doctor Web discovered this malware first, at the end of March 2012, and news about the largest Mac OS X botnet ever discovered was published on April 4. In late March, the Doctor Web virus laboratory received reports about Trojans for Mac OS X propagating using a Java vulnerability, which gave ground to the supposition that Backdoor.Flashback.39 was able to bundle "Macs" into botnets. Doctor Web's virus analysts studied the algorithm used by this Trojan to generate control server names and registered several such names. The result exceeded all expectations: After just 24 hours, it was clear that the number of infected Macs exceeded 600,000 and was continuing to grow rapidly. The geographical spread of the infection was also quite extensive:
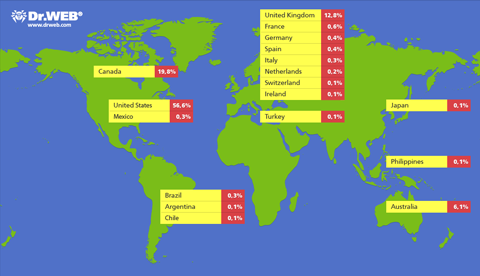
The geographical spread of Backdoor.Flashback.39
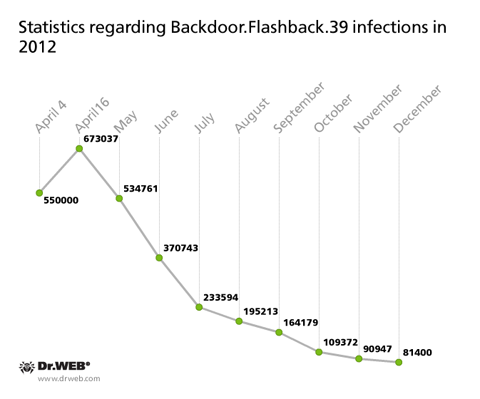
Over the next 10 days, the botnet peaked at about 670,000 infected computers (more than 800,000 individual computers, taking into account "cured" machines) and gradually went into decline. A Doctor Web news release describing this threat caused a stir in the world press and drew a wide public response. The myth that Mac OS X was one of the most secure operating systems in the world exploded overnight. The epidemic was chiefly caused by the fact that Apple released a security update for its own implementation of Java two months after a similar update was released by Oracle. This delay gave hackers a lot of time to distribute the malware with impunity. The other cause is, of course, the implicit faith Apple users have in the absolute security of the Mac OS X platform: this can be proved by the fact that the number of infected Macs kept growing even after Doctor Web informed the world about this threat.
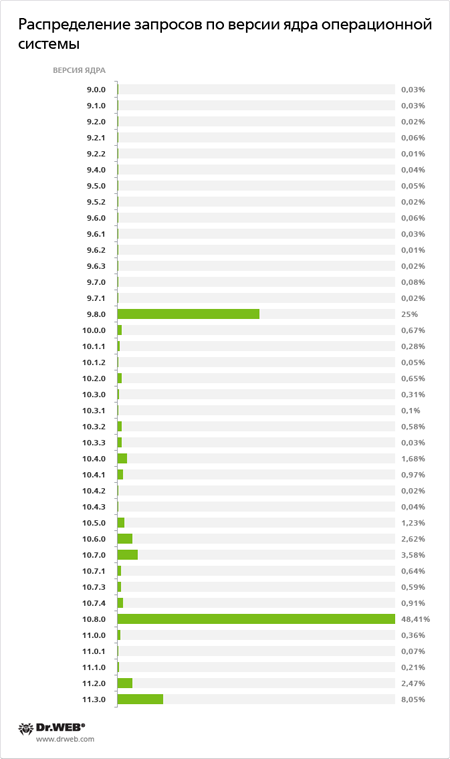
Investigations conducted by Doctor Web’s analysts made it possible to identify the version of the Mac OS X platform compromised by the malware, the OS kernel version, and other botnet characteristics derived by analyzing requests sent by this malicious program to control servers. The results, as of April 2012, are shown in the illustrations below.
In December 2012, the growth of the Backdoor.Flashback.39 botnet almost stopped, but it has yet to be vanquished; all over the world, there are still tens of thousands of infected Macs. As the Apple system platform becomes increasingly popular and the users of this OS aren't accustomed to using any anti-virus software, Mac OS X becomes a tasty morsel for many hackers. The average thief would never pass over a richly furnished apartment whose owners, for whatever ideological reason, do not lock the front door.
File viruses and other botnets
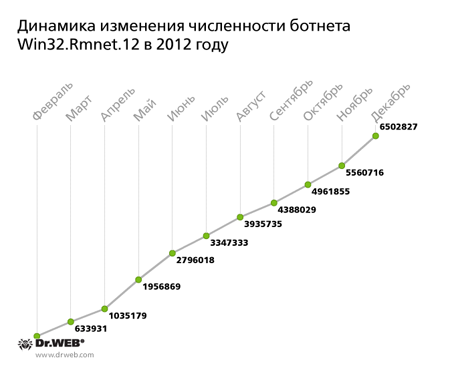
The file virus Win32.Rmnet.12, whose signature was added to the Dr.Web virus database in September 2011, has broken all possible records in the past 12 months, creating a botnet consisting of 6.5 million infected hosts. Win32.Rmnet.12 is a complex multi-component virus consisting of several modules and capable of self-replication. This virus infects Windows PCs, performs backdoor tasks and steals passwords stored by popular FTP clients. The passwords may later be used to mount network attacks and infect websites. When processing commands from a remote server, Win32.Rmnet.12 can bring down an OS. The virus can embed content into loaded web pages (i.e., make web injections), redirect a browser to a site specified by criminals, and send information entered into web forms by a user to remote hosts. Thus, this virus may really be dangerous for users. This virus was most widespread in Southeast Asian countries, such as Indonesia, Bangladesh, Vietnam, India and Pakistan. However, there are a significant number of infected machines in Russia. At first, the number of infections with Win32.Rmnet.12 was relatively small, but every month the number of infected PCs increased, until reaching a record 6.5 million PCs by the end of the year. The process is illustrated in the diagram below.
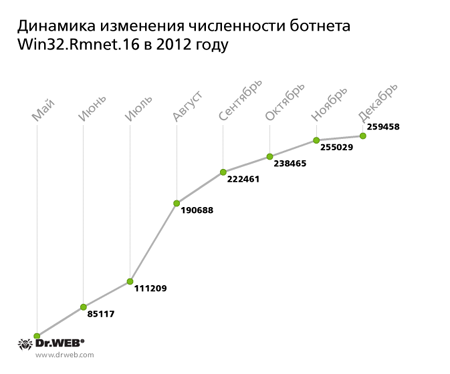
As there is no trend indicating that this virus will stop growing, we can assume that the virus Win32.Rmnet.12 Win32.Rmnet.12 will go on spreading. If the botnet's growth rate remains the same, in 2013 the total number of registered infected computers will exceed 10 million. One of the most widespread modifications of the file virus Win32.Rmnet.12 is its "brother" Win32.Rmnet.16. The main difference between this malicious program and its predecessor is that it uses a digital signature which is signed by a control server IP address. The virus makers also updated the virus's functional modules.
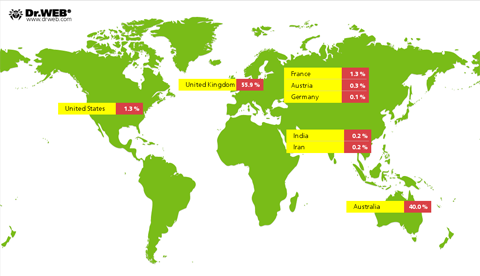
The botnet, consisting of workstations infected with Win32.Rmnet.16, is most widespread in Great Britain and Australia. However, this botnet is significantly smaller than Win32.Rmnet.12. The number of infections grew gradually during 2012, but the growth rate was lower. That is reflected in the diagram below.
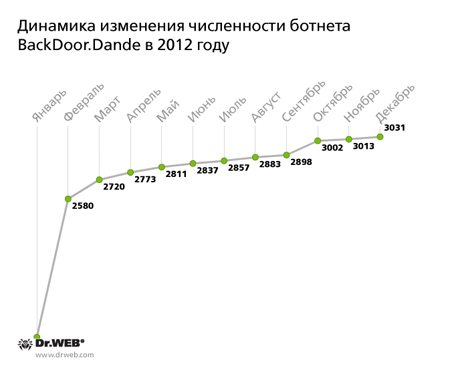
According to the statistics of Doctor Web’s specialists, we can assume that the growth of the Win32.Rmnet.16 botnet will decline, and the total number of infected hosts will not exceed one million, provided, of course, that some unforeseen circumstances do not lead to skyrocketing growth in the number of infections. Doctor Web specialists have full control of the Win32.Rmnet.12 and Win32.Rmnet.16 viral networks. In November 2011, Doctor Web warned users of the highly specialized Trojan BackDoor.Dande, which is designed to steal information from Russian pharmaceutical companies and pharmacies. BackDoor.Dande is a complex, multi-component Trojan that encrypts its modules with a key that is bound to a particular infected machine, and loads them into the memory. That's why its modules can be detected in the memory of an infected computer, and it's difficult to decrypt them separately from the infected PC. In addition, the module downloader is imbedded in the first section of one of the Windows system libraries, so that on its face, it cannot be distinguished from an uninfected library. This Trojan steals information from client applications used to order pharmaceutical products. These applications include a special configuration for 1S, "Analit: 7.7 formation, electronic medication order software EMOS-2 used by "Alliance Healthcare"; "Russian pharmacy", a program facilitating the formation of client applications; an electronic ordering system belonging to the pharmaceutical group ROSTA; the Katren WinPrice program; and several others. Despite the fact that the Trojan was added to the Dr.Web virus databases over a year ago, at the end of December 2012, the BackDoor.Dande botnet was still operating. Since the Trojan will operate only on computers running electronic medication ordering software, we can assume that the botnet BackDoor.Dande mostly incorporates computers owned by pharmacies and pharmaceutical companies. As of December 19, 2012, the botnet BackDoor.Dande included 3,031 infected computers. The network’s evolution is presented in the graph below.
Trojan encoders
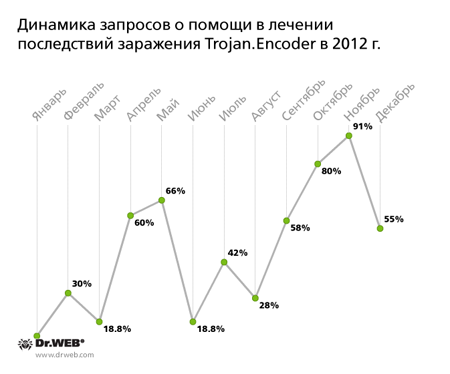
The year 2012 can perhaps be called the period of the greatest distribution of Trojan encoders: according to rough estimates, thousands of users all over the world have fallen victim to these malicious programs. During the year, the entries of many new modifications of this Trojan were added to the Dr.Web virus databases. The evolution of requests made to Doctor Web technical support from victims of Trojan encoders is presented in the graph below:
The first Trojan encoder modifications were detected in 2009. Encoders search for user files on disks available in an infected system; in particular, they search for Microsoft Office documents, music, photos, images and archives, and then encrypt them. Criminals demand that the user pay to decrypt the files. For a long time it was mainly users in Russia and other CIS countries who suffered from the actions of Trojan encoders, but in the spring of 2012, malware of the Trojan.Encoder family, which targets users in other European countries, was discovered. One of the first extortionist programs targeting European users was Trojan.Encoder.94. The Trojan featured an English interface, but infections were registered in Germany, Italy, Spain, England, Poland, Austria, Norway, Bulgaria and other countries. The first requests from Trojan.Encoder.94 victims outside Russia were received on April 9 and 10, 2012. Soon Doctor Web technical support was receiving requests from Latin America (Brazil and Argentina), as well as European countries such as France, Belgium, Switzerland, Netherlands, Croatia, Slovenia, Hungary and Romania. By the end of the year, the situation with Trojan encoders had changed dramatically. In 2011 the main target of these programs was Russian users, but by December 2012—according to Doctor Web analysts, the ratio of Russian users to foreign users was 50/50. The main surge of encoders targeting the Western market occurred in April and May 2012. However, by autumn of that year, their numbers had decreased slightly. According to available statistics, we can assume that the number of encoders in the coming year will grow rapidly. In general, 2013 will be called the “year of encoders”; they may very well spread in epidemic proportions.
Winlockers
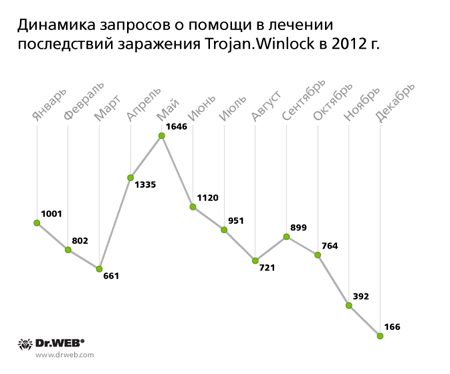
Trojans-winlockers, which paralyse operating systems and force users to make a payment to have their systems unlocked, have been known for quite a while. New winlocker modifications were detected in 2012, but their propagation was not dramatic. This year Doctor Web technical support received more than 10,000 requests from Trojan-winlocker victims. All of them were provided with technical aid. The evolution of such requests is shown in the graph below.
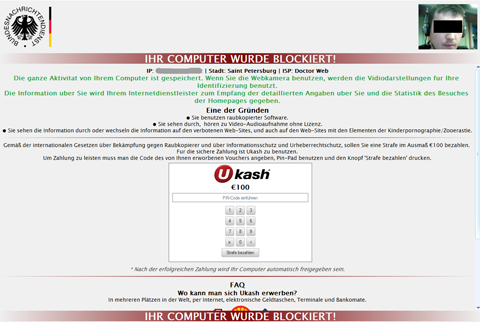
Autumn 2012 was marked by the spread of Trojan blockers, dubbed multi-lockers because of the header on the control server’s home page. These Trojans do not incorporate the images, texts or other resources that are usually shown on the screen by similar malicious applications once access to Windows has been blocked. All the necessary elements are downloaded from a remote server. This allows intruders to quickly configure displayed text, images and also change the unlock code. When launched on an infected PC, multi-lockers block the download of several applications and system utilities. Some multi-locker modifications can capture images from a web camera connected to an infected computer and display them in the window of the blocked system to scare the user. The message, allegedly from state law enforcement agencies, informs a victim that all their actions on the computer are being logged and their picture, obtained with a web camera, is being stored for later identification and the acquisition of more detailed personal information.
Doctor Web registered cases of infection in Canada, Spain, Germany, France, Italy, Portugal, Austria, Switzerland, the UK, Australia, the U.S. and other countries Intruders usually use ransom payment systems like Ukash, Moneypack and Paysafecard to get payments from victims. An analysis of Doctor Web Trojan winlockers shows that virus writers are moving away from traditional winlockers with the standard architecture toward more sophisticated designs and increased functionality. We can assume that these Trojans will appear sometime in the next year, and that the area of their propagation will expand.
The most important events in the field of information security
The year 2012 was marked by important and interesting events in the field of information security. The number of cases of websites being compromised to spread malware grew significantly in the past year. The first wave of hacker attacks was registered at the beginning of the year, when tens to hundreds of thousands of sites were compromised. In the compromised resources, hackers placed exploits used for the propagation of the Trojan for Mac OS X — Backdoor.Flashback.39. Another wave of Internet resources being hacked was registered in mid-August; several thousand sites were compromised in the Russian segment of the Internet to spread Trojans for mobile platforms. This trend remained till the end of the year; in December some popular portals, including the Dalai Lama’s official website, were compromised. The main goal was to infect visitors’ computers with malware for Windows and Mac OS X. In the past year, cybercriminals took broad advantage of various Java vulnerabilities. Thus, in spring 2012, they spread Trojans of the Trojan.Carberp family and a backdoor for Mac OS X Backdoor.Flashback.39, using the CVE-2012-0507 vulnerability. In July, the media reported that the CVE-2012-1723 vulnerability was used in the popular BlackHole exploits. On August 26, another critical Java vulnerability was described. Criminals used it to attack computers under Mac OS X, Linux and Windows. Doctor Web analysts confirm that the situation was very dramatic at that moment; on the day news about the discovered exploit was published, intruders already knew about the Java 7 vulnerability, but Java was to be updated only in mid-October. So, for roughly two months malware was able to exploit this unpatched vulnerability and redirect users to malicious resources through hacked websites that at first glance seemed harmless. Oracle’s actions in this situation were not timely, which is why malware penetrated unprotected computers. However, when Java was updated in September 2012, information security specialists discovered other critical vulnerabilities with this platform. In addition, in early November, a zero-day vulnerability was found in Adobe Reader (versions 10 and 11). With the help of this vulnerability, intruders succeeded in running malware on compromised computers. Cybercriminals distributed the file containing this vulnerability over the Internet and via e-mail. Another interesting discovery made by specialists from one of the anti-virus labs was Win32.HLLW.Flame, sophisticated multi-component malware that Doctor Web specialists dubbed Trojan Elephant because of its record size (more than 6 MB). This program has a wealth of capabilities, but it isn't widespread in the wild. According to Doctor Web analysts, this Trojan is not as dangerous as the many publications on the Internet and in the media made it out to be. Another important event in the field of information technology was the elimination of the botnet BackDoor.BlackEnergy. Это была крупнейшая бот-сеть, ориентированная на массовую рассылку спама, а также проведение DDoS-атак, и прекращение ее деятельности достаточно быстро привело к снижению объемов спам-трафика начиная с июля 2012 года. Вместе с тем, несмотря на уничтожение главных управляющих центров BackDoor.BlackEnergy, специалисты «Доктор Веб» зафиксировали несколько более мелких командных серверов этой сети, которые продолжали свою деятельность и после опубликованных в прессе заявлений об уничтожении данной бот-сети. Тем не менее, уже спустя несколько месяцев прекратили свое существование и эти серверы, поэтому в настоящий момент мы действительно можем говорить о полной и безоговорочной ликвидации ботнета BackDoor.BlackEnergy in July. This was the largest botnet ever created to send out unsolicited e-mails and mount DDoS attacks; after its shutdown, the volume of spam traffic diminished significantly. Besides the fact that the main control servers of BackDoor.BlackEnergy were destroyed, Doctor Web specialists detected some small operating control servers of this botnet after its elimination was announced in the media. However, after several months, these servers were also destroyed. Today we can say that the BackDoor.BlackEnergy botnet has been eliminated completely.
Online Fraud
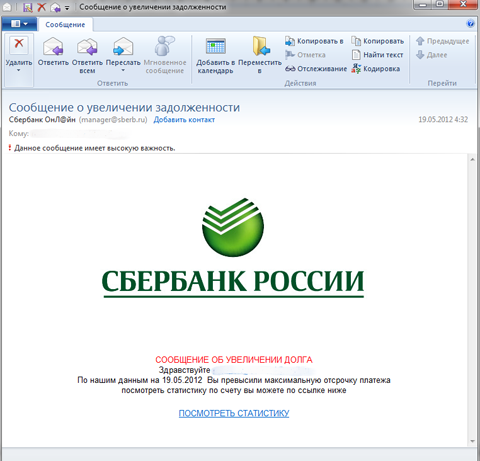
Online fraudsters are ever watchful, and they use all possible means to make money on gullible users. Thus, at the beginning of May, they attacked Facebook users. After visiting their Facebook pages, users discovered a link in their newsfeeds to Profile Visitor, which allegedly can record and show visitors their profiles on a special web page. As a rule, the link was published on behalf of a user’s friends and led to a Facebook embedded application page. To activate the application, permission had to be given to the program to publish content on behalf of the user account. As soon as an unsuspecting victim clicked Allow, a link to the application — posted on their behalf — appeared on the wall of their profile and in the newsfeeds of all their friends as well. However, even if the user did not allow Profile Visitor to publish anything on their behalf, everyone in their list of friends would automatically be marked in a "photo" that was actually a Profile Visitor banner link. Following this link, the user was redirected to bogus sites. At the end of the same month, many Russian users received e-mails sent on behalf of Sberbank. The subject was "Debt increase message". The message said that the recipient "had exceeded the maximum deferment of payment", and provided a link so that the recipient could supposedly view statistics. By following this link, the user downloaded the file .SCR in a RAR or in a ZIP archive or in an unpacked format. When an attempt was made by the user to open this file, documents and images stored on the computer hard drive were encrypted; and in exchange for decrypting these items, criminals demanded a set payment.
In June, e-mails were sent on behalf of the UPS and EMS postal services. The e-mails reported that the service couldn't deliver the message to the user, and the cybercriminals referred the user to an attached file containing a Trojan to see more details. At the same time, cybercriminals invented a new way of cheating users searching for jobs. In pursuing their goals, attackers created an account for a non-existent company with a big and catchy name on employment websites. Then the scammers sent job offers to applicants. To become employed, users were invited to online interviews, during which they had to answer several simple questions via a specified website. The online interview usually consisted of a short test involving several dozen simple questions, but after the victims passed the test, they were invited to send an SMS message containing their personal result code to a short number and enter into the appropriate field the verification code received in a reply message. By doing this, users wound up agreeing to the terms of a pseudo subscription to an information-access service, and a service fee was debited from their account on a monthly basis.
The most interesting threats
One of the most important events of the fourth quarter of the year was a sharp decline in the number computers infected with the Trojan program, Trojan.Mayachok.1, which had headed the list of the most dangerous threats since the beginning of the year. Above all, this was due to the fact that virus writers began modifying this Trojan: at the beginning of the year, there were a few modifications of this Trojan, but by the end of December, Dr.Web virus databases included more than 1,000 corresponding entries. Virus writers changed the malicious program code and its features. At the beginning of the year, at least one Trojan.Mayachok modification appeared each month, but in October and November, new modifications of this Trojan were detected almost daily, but there were few significant differences between them. Trojan.Mayachok can embed content into loaded web pages. For example, it can block access to the Internet and demand a fee to unlock it. We can assume that new Trojan modifications of this family will appear on a regular basis. In late June, Doctor Web specialists analysed Trojan.Hottrend smallest known banking Trojan., whic Its size is only 20 KB. The main purpose of this malware is to monitor Internet traffic to intercept sensitive (including banking) information and send it to criminals. One of the most interesting Trojans identified by Doctor Web virus analysts in 2012 was BackDoor.DaVinci.1. The most distinguishing feature of this malicious application is that it runs both in Windows and Mac OS X. It is known that a modification targeting mobile platforms also exists. This malicious program is a multi-component backdoor that includes a large number of functional modules, such as drivers that use rootkit technologies, to hide the application in an operating system. BackDoor.DaVinci.1 allows criminals to gain full control over an infected computer. In addition, the Trojan saves and transmits information about the infected machine to criminals, acts as a key logger, and can take screenshots and intercept e-mail, ICQ, Skype messages and data captured by a microphone or video camera connected to a computer. In addition, the backdoor has a large set of tools with which to bypass anti-virus software and firewalls, so it may run unnoticed in a system for a long time. Interestingly, BackDoor.DaVinci.1 for Mac OS X is the first instance of malware for the platform that uses rootkit technologies to hide its files and processes. But the most original Trojan of the year was Trojan.KillFiles.9055. It was spread via e-mail messages that called on users to attend an opposition-organized rally on March 5, 2012. The body of this Trojan was in the macro built in an attached Word document. Once opened with a word processor, this program saved itself on the hard drive and launched the process. Once launched on a victim's computer, Trojan.KillFiles.9055 freezes Windows OS. Simultaneously, the Trojan replaced the contents of all of the files found on the C drive (.msc, .exe, .doc, .xls, .rar, .zip, and .7z) with meaningless data and marked them for deletion upon reboot, which renders Windows non-operational. Then the Trojan notified a remote server that the system had been broken down successfully.
Android is under attack: easy money, access to confidential information, and complexity of threats
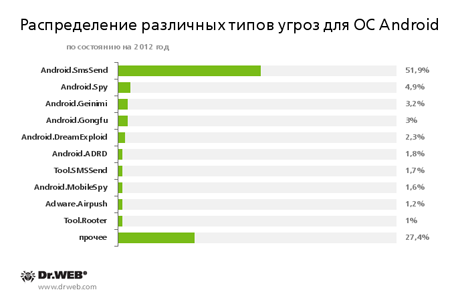
As was expected, the number of threats for Android OS went on growing in 2012; mobile devices under this OS became increasingly popular on the global market. Thus, according to a recent study by IDC, in the third quarter of 2012, three-quarters of the smart phones supplied were under this platform. Different types of malware for Android are shown in the diagram below.
Trojans of the Android.SmsSend family, which appeared as early as 2010, remain the most widespread and commonly occurring threat. These Trojans send costly SMS messages and subscribe owners of the devices to various services. The majority of Android.SmsSend Trojans are primitive programs, but they are easy to develop and offer high pay back. That's why cybercriminals release many modifications of these Trojans. In 2012 the quantity of spyware for the Android OS grew significantly. From mid-year onwards, a number of Trojans emerged and spread on devices belonging to Japanese Android users. All these Trojans—including Android.EmailSpy.origin, Android.MailSteal.1.origin и Android.Maxbet.1.origin — were distributed via spam containing a link to download a "useful" application. Spyware is designed to steal personal information such as e-mail addresses. New banking Trojans were also detected, for example Android.SpyEye.2.origin, Android.Panda.2.origin and Android.FakeSber.1.origin. The last one interests us greatly, because while malware of this type was always targeting foreign users, this one was designed to attack Russian bank customers. This indicates that the reach of such malicious programs is widening. Although banking Trojans for Android are not widespread, they may represent a serious danger for users, because these attacks are usually pointed and well-prepared. The emergence of the first such malware targeting Russian users may lead to an increase in incidents involving it. In the past year, the range of commercial spyware has expanded; not only were new modifications of well-known cyber espionage and monitoring applications added to the Dr.Web virus databases over the course of the year, but also some new families of these applications. In 2013, we can expect potentially dangerous programs and spy Trojans to increase. Advanced Persistent Threat (APT) campaigns are likely to use Trojans for Android. In general, we can say that a growing number of Android threats related in one way or another to the theft of confidential information are being used in narrowly focused attacks. This trend won't disappear in the near future. One of the most dangerous Trojans for mobile devices running Android OS in 2012 was Android.SmsSend.186.origin. It is distinguished from most other representatives of this family by the sophisticated methods it employs to hide its malicious activity. First, a dropper not requiring any special permission was used during its propagation. Second, after installation, Android.SmsSend.186.origin forced users to assign it administrator privileges. On some Android OS versions, once the Trojan obtained these privileges, it was difficult to remove it from the device. New malware that resists attempts to remove it and uses different methods to hide its activity is likely to appear in 2013. Malware that exploits Android vulnerabilities to improve system privileges was not widespread in the past year. The reason for this could be that users are gradually switching to newer Android versions that do not have these vulnerabilities and enjoy improved platform security as a whole However, it is possible that in 2013 a new malicious application exploiting previously unknown vulnerabilities will emerge. The latest, recently released Android version (4.2) has several improvements designed to combat malware. Some new features were added. For example: application checks are based on security ratings, and there is a new restriction on applications that can send SMS to premium numbers (now users can allow or forbid the sending of such messages). However, the effectiveness of these innovations can only be fully assessed once a significant number of mobile devices are using the updated version. Taking into consideration the huge number of devices compatible with the Android OS, we can assume that cybercriminals will find ways to bypass new security features.
Predictions and prospects
Based on an analysis of threats received by the Doctor Web virus laboratory in 2012, we can predict the major trends that are likely to develop in 2013. The number of threats for Mac OS X will increase. These include Trojans that can exploit vulnerabilities (the Java vulnerability, for example) and botnets targeted exclusively at Apple-compatible computers. The range of malware for the Android mobile platform will also increase significantly. The estimated growth rate may be as high as 50-100% of the current number of known threats. Botnets targeting Microsoft Windows OS will continue to grow. Thus, already in the first quarter of 2013, the number of computers infected with Win32.Rmnet.12 and bundled into a botnet will exceed 10 million (unless measures are taken to eliminate this botnet). Viruses or Trojans that exploit vulnerabilities or specific technologies used in Microsoft Windows 8 may appear. For example, we can expect malware to intercept the GPS coordinates of Tablet PCs using this platform. Banking Trojans designed to steal confidential information and gain unauthorized access to online banking services will become more sophisticated and widespread. The number of pre-planned, targeted attacks against different businesses may increase. Malware will increasingly use webcams, microphones, and GPS receivers to spy on users. Trojans spyware will be more diversified. New threats using cloud services and other distributed services are likely to appear. The number of malicious programs using P2P and TOP networks will increase.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments