August 1, 2012
Viruses
According to statistics collected with Dr.Web CureIt!, Trojan.Mayachok.1 was the most commonly occurring threat in July. Compared with June, instances of its detection increased by 18.5%. The main purpose of this malicious program is to block access to certain sites in order to force the user to subscribe to a paid service. Apparently, this criminal profit scheme is rather lucrative, because the popularity of this Trojan among distributors of malicious software remains as great as ever.
Trojan.SMSSend programs rank second in terms of number of detections — their percentage in the summary statistics also increased markedly. But, by contrast, the number of Trojan.Carberp detections fell by 36%. Trojan.Hosts programs and malicious downloaders are often found on computers. The below table shows the list of threats most frequently detected by Dr.Web CureIt! on home PCs in July 2012.
| # | Threat name | Threat type | Detections | %% |
|---|---|---|---|---|
| 1 | Trojan.Mayachok.1 | Virus | 69869 | 7,52% |
| 2 | Trojan.SMSSend.2905 | Virus | 7808 | 0,84% |
| 3 | Trojan.Fraudster.292 | Virus | 6017 | 0,65% |
| 4 | Trojan.Hosts.5940 | Virus | 4883 | 0,53% |
| 5 | Trojan.Carberp.30 | Virus | 4721 | 0,51% |
| 6 | BackDoor.Butirat.91 | Virus | 4048 | 0,44% |
| 7 | Trojan.SMSSend.2363 | Virus | 3235 | 0,35% |
| 8 | Win32.HLLW.Gavir.ini | Virus | 3148 | 0,34% |
| 9 | BackDoor.Ddoser.131 | Virus | 3076 | 0,33% |
| 10 | BackDoor.Butirat.60 | Virus | 2812 | 0,30% |
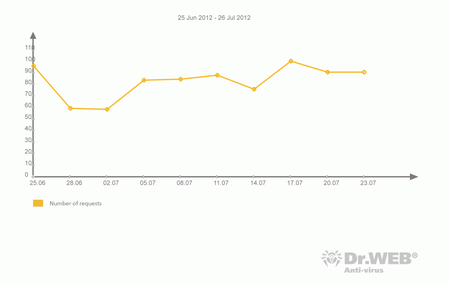
While the number of support requests concerning blocked system access declined at the end of June and in early July, the second half of July saw some increase in incidents of Winlock infections. The chart below shows how the number of such requests for technical support received by Doctor Web changed during the past month.
Malicious spam
Following the shutdown of one of the largest botnets ever created to send out unsolicited e-mails (BackDoor.Blackenergy), the volume of spam traffic diminished significantly. BackDoor.Andromeda.22 leads among malware detected by Dr.Web software in e-mail attachments. Trojan.Necurs.21 ranks second and Trojan.Oficla.zip ranks third. Downloader Trojans and Trojan.Winlock malware are detected quite often (around 0.7% of all malicious mail traffic). It should be noted that the list of programs detected in the last month remained largely unchanged: the number of identified instances of Trojan BackDoor.Andromeda.22 increased slightly, while the e-mail worm family Win32.HLLM.MyDoom, on the contrary, was scarcer than before. In addition, in July Trojan.AVKill programs that were actively spreading a month ago have virtually disappeared from mail server malware statistics.
Botnets
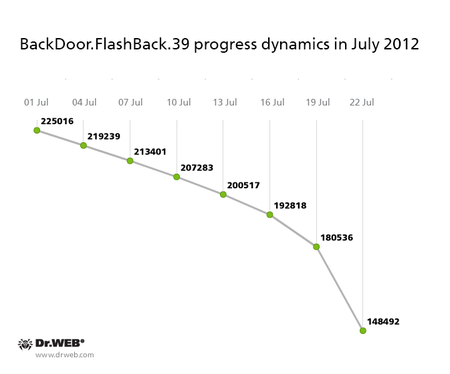
The number of bots in the largest botnet BackDoor.Flashback.39, which included more than 800,000 computers running Mac OS X in April 2012, continues to steadily decline. Around 200,000 bots operated in the network at the beginning of July, but by month’s end, the total number of infected Macs fell to 148,492. Nevertheless, despite the release of operating system updates, anti-virus software for Mac OS X, and an array of tools to remove BackDoor.Flashback.39 offered by various companies, newly infected Macs are still joining the botnet, though their number at present does not exceed 3-4 computers per day. The graph below shows how the number of BackDoor.Flashback.39 bots changed through July 2012:
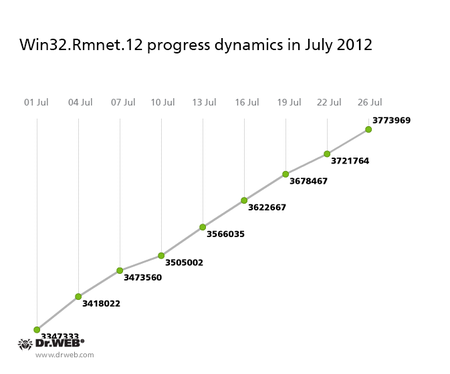
However, the Win32.Rmnet.12 botnet continued to grow, and in June 2012, the number of infected computers surpassed the three million mark, as we reported in a previously published review. Over the past month the number of Win32.Rmnet.12 bots increased by another 481,779 infected machines, and the total number of compromised hosts reached 3,773,969. We'd like to remind you that Win32.Rmnet.12 is a file infector capable of self-replication. It was designed to make web injections—that is, it can embed code into loaded web pages. In addition, Win32.Rmnet.12 redirects users to phishing sites, steals cookie files, and retrieves passwords stored by popular FTP clients such as Ghisler, WS FTP, CuteFTP, FlashFXP, FileZilla, and Bullet Proof FTP. Also, Win32.Rmnet.12 can perform backdoor functions and execute various commands, including the removal of the OS. The graph showing changes in the number of Win32.Rmnet.12 bots in July 2012 can be found below:
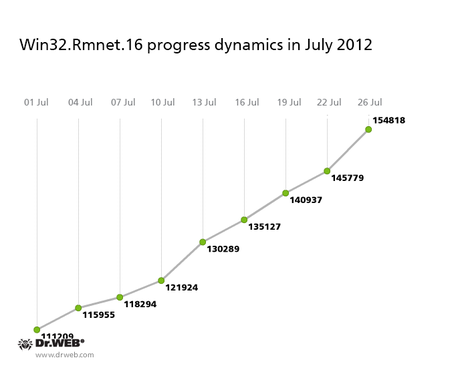
A similar situation exists concerning the Win32.Rmnet.16 botnet. It is also growing, though not so rapidly: in the past month the number of computers infected by the virus has increased by about 50,000, reaching 154,818. A graph showing changes in the number of bots is presented below.
In general, the growth rate is uneven; from 650 to 2,500 machines connect to the network daily.
Earlier this month, Doctor Web warned users about the growing BackDoor.Dande botnet which targets the activities pharmaceutical companies. This Trojan steals information from client applications used to order pharmaceutical products. Since the Trojan will operate only on computers running electronic medication order software, we can assume that the botnet BackDoor.Dande mostly incorporates computers owned by pharmacies and pharmaceutical companies. At the beginning of July 2012, there were 2,857 infected machines and 2,788 (98.5%) of them are located in Russia; the rest are in other countries.
By the end of July, the number of bots has not changed: currently its growth rate is next to zero.
The threat of the month: BackDoor.DaVinci.1
On July 23 Doctor Web's anti-virus laboratory received a malware sample which turned out to be a multi-purpose backdoor comprising a large number of functional modules such as rootkit drivers used to hide the application in the system.
BackDoor.DaVinci.1 is spread as the AdobeFlashPlayer.jar file, signed using an invalid digital certificate.
The file determines the OS type and saves and launches an infected application in the compromised system—currently, Doctor Web's virus analysts have Trojan samples intended for Windows and Mac OS X. It is known that a version targeting mobile platforms also exists.
The malware features a modular architecture: the main backdoor component is supplemented with an encrypted configuration file and rootkit drivers. These drivers enable the malicious application to conceal itself. All Trojan versions use the same configuration file containing the modules' settings.
BackDoor.DaVinci.1 allows criminals to gain full control over an infected computer. In addition, the Trojan saves and transmits information about the infected machine to criminals, acts as a key logger, and can take screenshots and intercept e-mail, ICQ, Skype messages and data captured by a microphone or video camera connected to a computer. In addition, the backdoor has a large set of tools with which to bypass anti-virus software and firewalls, so it may run unnoticed in a system for a long time. Interestingly, BackDoor.DaVinci.1 for Mac OS X is the first instance of malware for the platform that uses rootkit technologies to hide its files and processes.
Threats to Android
During the month, Doctor Web found a number of new malicious programs for Android. Thus, in early July, Doctor Web's analysts discovered several malicious applications distributed via Google Play. According to available statistics, these programs have been downloaded by users more than 18 thousand times.
Android.MMarketPay.origin became one of the most remarkable malicious species for Android that was added to the virus database in July. Its main objective is to purchase apps in the store run by China Mobile without user consent. The Trojan performs all steps automatically: it intercepts verification codes and confirms purchases. Criminals embedded Android.MMarketPay.origin into programs distributed via Chinese forums and sites distributing applications.
The potentially dangerous application Find and Call (Program.Fidall.origin.1), distributed via Google Play, was also added to the virus database. There is also version of this malicious program for iOS (IPhoneOS.Fidall.1) that users could download from Apple Store.
Find and Call is marketed as an effective tool for communication. When launched, it prompts a user to undergo an authorization procedure and enter their e-mail address. If the owner of the mobile device agrees to do it, Find and Call collects contact information found in the device and uploads it to a remote server. The server uses obtained contact information to send SMS messages encouraging recipients to install the application, whereas the user who installed the program is designated as the sender.
Android.MailSteal.1, designed to steal e-mail addresses found in the contact book of a mobile device, was discovered at the end of the month.
In addition, several signatures for new modifications of Android.Gongfu and Android.SmsSend were added to the virus databases.
Other threats in July
In early July, Doctor Web published a news post about malware for Mac OS X. The BackDoor.Macontrol.2 Trojan operates as a backdoor and can execute commands coming from a remote, criminal-controlled server.
BackDoor.Bebloh.17 joined the ranks of banking Trojans. This application is distributed as an attachment to spam messages including those supposedly sent by DHL. It poses a threat to users of e-banking services (RBS), because it allows attackers to steal confidential information by intercepting data submitted through forms in the browser window and by embedding its code into bank web pages. More information about this threat can be obtained from the material published by Doctor Web.
At the end of the month, a mass spam mailing was registered in the social network Twitter. Messages were written in Russian and included a link which, depending on what browser was involved, could direct a user to a fraudulent site or a resource from which malware for mobile devices can be downloaded.
In addition, the second half of July saw the emergence of the Trojan downloader known as Trojan.Yaryar.1. It has a wide set of tools for identifying debugging and analysis software and, moreover, can access NTFS via its own routine rather than Windows API which is rather uncommon for this type of malware.
Malicious files detected in mail traffic in July
| 01.07.2012 00:00 - 31.07.2012 18:00 | ||
| 1 | BackDoor.Andromeda.22 | 1.52% |
| 2 | Trojan.Oficla.zip | 1.35% |
| 3 | Trojan.Necurs.21 | 1.32% |
| 4 | Win32.HLLW.Siggen.2984 | 1.29% |
| 5 | Win32.HLLW.Siggen.3956 | 1.16% |
| 6 | Trojan.DownLoader6.29048 | 1.02% |
| 7 | Trojan.DownLoader6.28761 | 1.02% |
| 8 | Trojan.DownLoader6.25839 | 0.99% |
| 9 | Exploit.CVE2010-3333.4 | 0.96% |
| 10 | Trojan.Swizzor.17774 | 0.92% |
| 11 | Trojan.DownLoader6.28840 | 0.86% |
| 12 | Trojan.Packed.2503 | 0.79% |
| 13 | Win32.HLLW.Siggen.3616 | 0.73% |
| 14 | Trojan.KillProc.17345 | 0.56% |
| 15 | Win32.HLLM.MyDoom.33808 | 0.56% |
| 16 | Win32.HLLM.MyDoom.54464 | 0.56% |
| 17 | Trojan.Winlock.6426 | 0.46% |
| 18 | SCRIPT.Virus | 0.40% |
| 19 | Win32.HLLM.Netsky.35328 | 0.36% |
| 20 | Trojan.Fakealert.32747 | 0.36% |
Malicious files detected on user computers in July
| 01.07.2012 00:00 - 31.07.2012 18:00 | ||
| 1 | SCRIPT.Virus | 0.47% |
| 2 | Trojan.Fraudster.292 | 0.40% |
| 3 | Adware.Downware.179 | 0.39% |
| 4 | Trojan.Mayachok.1 | 0.38% |
| 5 | Trojan.Fraudster.256 | 0.38% |
| 6 | Trojan.SMSSend.2925 | 0.37% |
| 7 | Tool.Unwanted.JS.SMSFraud.10 | 0.34% |
| 8 | Trojan.Fraudster.296 | 0.33% |
| 9 | Trojan.Fraudster.261 | 0.32% |
| 10 | Win32.HLLW.Shadow | 0.30% |
| 11 | Tool.Unwanted.JS.SMSFraud.15 | 0.30% |
| 12 | Win32.HLLW.Autoruner.59834 | 0.28% |
| 13 | Adware.Downware.353 | 0.27% |
| 14 | Trojan.SMSSend.2905 | 0.26% |
| 15 | Tool.InstallToolbar.88 | 0.26% |
| 16 | Adware.Downware.316 | 0.26% |
| 17 | Adware.Downware.342 | 0.26% |
| 18 | Adware.Bandoo.1 | 0.26% |
| 19 | Trojan.SMSSend.2726 | 0.25% |
| 20 | Trojan.Fraudster.252 | 0.24% |


![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments