July 2, 2012
Viruses
According to statistics collected by Dr.Web CureIt!, in June, Trojan.Mayachok.1 was the malware most frequently detected on users' computers, the same as a month ago. The number of its detections has increased markedly: from 3.73% (45,327 cases) in May to 5.82% (56,767 cases) in June. Detections of Trojan downloader modifications have multiplied as well. Trojan.SMSSend variations were found on infected computers as frequently as before, while, in contrast, detections of various Trojan.Carberp versions fell by a few percentage points. The graph below shows in percentage terms the distribution of the most common threats detected by Dr.Web CureIt!.
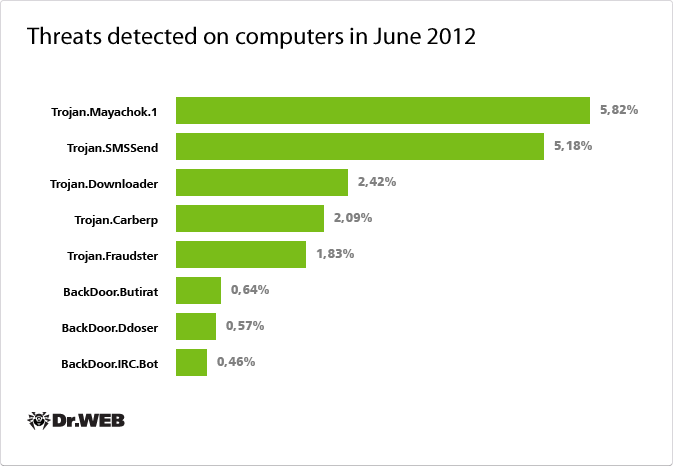
As for threats spread via e-mail, BackDoor.Andromeda.22, which downloads a host of other dangerous applications onto an infected computer, is the undisputed leader. Programs of this backdoor family can exchange encrypted data with a remote server, and upon command, can download various files onto an infected machine.
Second and third places are occupied by Trojan downloaders, while the fourth position is taken by Trojan.Inject1.4969 whose mass distribution was already reported on in a recent news post. Also frequently delivered via e-mail are Win32.HLLM.MyDoom worms and different versions of Windows blockers.
Botnets
Back in April, Doctor Web discovered the largest botnet in history, comprised of a huge number of Apple-compatible computers infected with BackDoor.Flashback.39. Surprisingly, the botnet is still operating properly, although the number of its bots is declining gradually. According to verified data, 364,741 infected Macs were connected to the network at the beginning of June, and the number dropped to 191,756 by month's end. The average daily increase in bot numbers is also very small: an average of 25 newly infected computers are connecting to the BackDoor.Flashback39 network every 24 hours. See how the total number of BackDoor.Flashback.39 bots changed through June 2012 on the graph below.
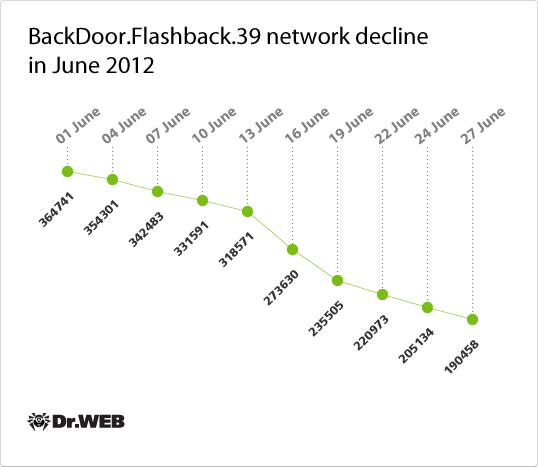
The graph indicates a strong tendency towards the number of active, Apple-compatible computers infected with BackDoor.Flashback.39 being reduced. You can get more information about this threat and check your computer for a possible infection online at drweb.com/flashback, which has been specially designed by Doctor Web to help users neutralize the threat.
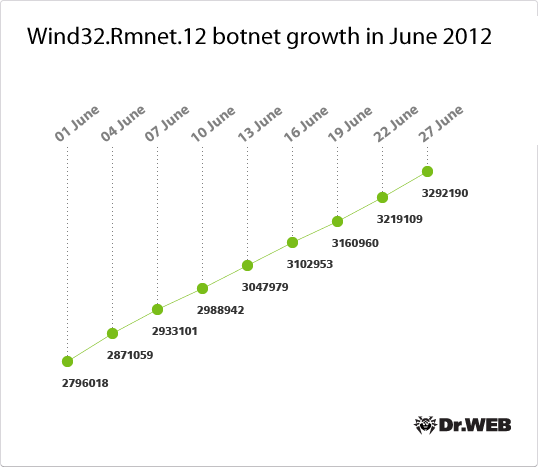
But in the case of the Win32.Rmnet.12 file infector, the situation is rather different: as we've already reported, its botnet has broken the three million mark The virus’s geographical reach has not changed much: the countries most exposed to infection still include Indonesia, Bangladesh, Vietnam, India, and Egypt; a large number of infected PCs can be found in Russia. To learn more about the Win32.Rmnet.12 file infector, refer to our recent publication. On average, 9-150 thousand new bots are registered in Win32.Rmnet.12 networks on a daily basis, which significantly increases the total number of infected machines. Win32.Rmnet.12 botnet growth through June 2012 is illustrated in the graph below.
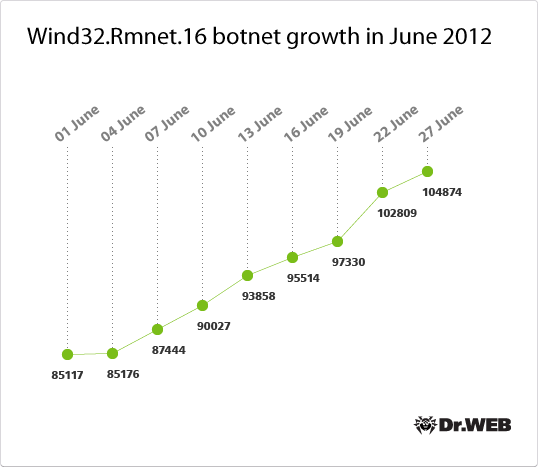
At the same time, the Win32.Rmnet.16 botnet also continues to grow, though not as rapidly. If at the end of May, this malware modification that is widespread mainly in the UK and Australia, infected 84,491 computers, within exactly one month, the number increased to 104,874. You can use the graph below to trace how Win32.Rmnet.16 infections increased in number.
Scammers are on the alert
In June, Doctor Web warned users about another fraud technique that was gaining popularity among criminals, and that publication triggered a wide response. The technique in question targeted online job seekers.
People, who register on a job offer portal as individuals seeking employment, typically fill out a special form in which they provide their full name, contacts, information about their educational background and work experience, as well as other data that may be of interest to a potential employer. Representatives of companies registered on the site as employers can view such CVs. In pursuing their goals, attackers create an account for a non-existing company on such a resource or pose as a well-known firm. Then the scammers search for CVs published on the website and send job offers to applicants. To get a job, a user is invited to an online interview, during which they must answer several simple questions via a specified website. Designed by criminals specifically for this purpose, such sites look like they belong to respected companies, so the unsuspecting victim falls into a trap.
An online interview usually consists of a short test involving several dozen simple questions, and the applicant is not asked for their name, contact information, or information about work experience or qualifications. But after they have passed the test, the victim is invited to send an SMS message containing their personal result code to a short number and enter into the appropriate field the verification code received in a reply message. By doing this, the user winds up agreeing to the terms of a pseudo subscription to an information-access service, and the service fee will be debited from their account on a monthly basis.
It should be noted that some large companies do conduct such online interviews in order to accelerate the recruitment process. The best way to avoid such traps is to search the Internet for information about the company offering the job—many publications are available about any large and respected business. You can also search for the company's contact information and call them to find out more about the proposed interview. A telephone conversation with a company representative will certainly dispel a job seeker’s arising doubts.
The threat of the month: Trojan.Hottrend
The smallest known banking Trojan, dubbed Tinba (short for “tiny banker”) by security experts, won the title for Threat of the Month. Written in Assembly, it occupies as little as 20 KB. In the Dr.Web virus database, this threat is listed under the name Trojan.Hottrend, and the first records concerning this Trojan family were added to the Dr.Web virus databases as early as late April 2012.
The main purpose of this malware is to monitor Internet traffic to intercept sensitive (including banking) information and send it to criminals. In June, Doctor Web's analysts also discovered several other species of small-sized banking Trojans, for example, Trojan.PWS.Banker.64540 which occupies about 80 KB on a disk. A detailed description of this can be found onthreatDoctor Web's site, and a separate review has been published concerning Trojan.Hottrend malignant payload.
Threats to Android
The rate at which new threats to Android are identified appears to be steady. During the month, more than 35 new Android.SmsSend modifications were added to the virus database as well as several other malicious programs that may harm mobile devices. In addition, in the second half of June, we reported on the distribution of Trojan Android.SpyEye.2.origin, which is capable of stealing short messages on an infected mobile phone.
At the end of the month, Android.SmsBot.1.origin, distributed with spam, was added into the Dr.Web virus database. This malicious program uses a fairly complex algorithm to generate a Twitter account name and acquires control server names via this account. Having established a connection to a command center, Android.SmsBot.1 can send information about an infected device to criminals, receive commands, and report back upon their execution. Covert SMS sending is one of its key functions. It may be a danger to users of mobile devices, though some anonymous users (perhaps, individuals related to the program’s creation) argue that this application is intended to automate telephone voting.
Top 20 malware detected in June in mail traffic
| 01.06.2012 00:00 - 29.06.2012 16:00 | ||
| 1 | BackDoor.Andromeda.22 | 2.14% |
| 2 | Win32.HLLW.Siggen.2984 | 2.06% |
| 3 | Trojan.DownLoader6.19810 | 1.53% |
| 4 | Trojan.Inject1.4969 | 1.23% |
| 5 | Trojan.DownLoader6.20943 | 1.18% |
| 6 | Trojan.DownLoader6.18049 | 1.09% |
| 7 | Win32.HLLM.MyDoom.33808 | 1.01% |
| 8 | Win32.HLLM.MyDoom.54464 | 0.88% |
| 9 | Trojan.Winlock.5600 | 0.83% |
| 10 | Trojan.AVKill.19024 | 0.74% |
| 11 | Trojan.AVKill.18763 | 0.66% |
| 12 | Win32.HLLM.Beagle | 0.61% |
| 13 | Trojan.AVKill.18755 | 0.53% |
| 14 | Win32.HLLM.Netsky.35328 | 0.48% |
| 15 | Trojan.DownLoader6.18373 | 0.48% |
| 16 | SCRIPT.Virus | 0.44% |
| 17 | Trojan.AVKill.18749 | 0.44% |
| 18 | Trojan.MulDrop3.55845 | 0.39% |
| 19 | Win32.HLLM.Netsky.based | 0.39% |
| 20 | Trojan.PWS.Panda.786 | 0.35% |
Top 20 malware detected in June on user PCs
| 01.06.2012 00:00 - 29.06.2012 16:00 | ||
| 1 | Trojan.Fraudster.256 | 0.50% |
| 2 | SCRIPT.Virus | 0.44% |
| 3 | Trojan.Fraudster.292 | 0.42% |
| 4 | Adware.Downware.179 | 0.38% |
| 5 | Tool.Unwanted.JS.SMSFraud.15 | 0.36% |
| 6 | Trojan.Fraudster.296 | 0.35% |
| 7 | Trojan.SMSSend.2925 | 0.35% |
| 8 | JS.IFrame.233 | 0.34% |
| 9 | Win32.HLLW.Shadow | 0.34% |
| 10 | Trojan.Fraudster.261 | 0.33% |
| 11 | Trojan.Mayachok.1 | 0.33% |
| 12 | Trojan.SMSSend.2905 | 0.33% |
| 13 | Trojan.SMSSend.2884 | 0.33% |
| 14 | Tool.Unwanted.JS.SMSFraud.10 | 0.32% |
| 15 | Win32.HLLW.Autoruner.59834 | 0.32% |
| 16 | Trojan.SMSSend.2726 | 0.28% |
| 17 | Trojan.Fraudster.308 | 0.26% |
| 18 | Win32.HLLW.Shadow.based | 0.26% |
| 19 | Adware.Downware.316 | 0.25% |
| 20 | Tool.InstallToolbar.55 | 0.24% |

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments