April 2012 Virus Survey: the first ever large-scale botnet for the Mac OS X, the millionth botnet for Windows and the invasion of Trojan coders in Europe
Virus reviews | All the news | Virus alerts
May 2, 2012
Macs under attack globally
The first botnet in the history that was created by hackers using BackDoor.Flashback.39 malware, literally struck more than 800,000 computers running Mac OS X, and figuratively — numerous informational web portals and a large number of mass media. The news quickly spread all over the world, becoming a sensation.
Back in late March the Doctor Web virus laboratory received the first reports that the attackers were actively using known Java vulnerabilities to spread malware for Mac OS X. Since this information came with some regularity and from various sources, it was suggested that the BackDoor.Flashback.39 Trojan that uses Java vulnerabilities can form a botnet on Apple-compatible computers. This malware, like so many other similar ones, has a built-in algorithm for selection of domain names, which are then used by the Trojan as control servers: such an approach, firstly, can significantly increase the network "survivability", and secondly, redistribute the load efficiently between command centers in a timely manner, if the traffic generated by bots exceeds some critical values. On the other hand, this provides an opportunity for information security professionals to "reveal" the method the Trojan is using to choose control centers, and to create a "fake" command server to gather necessary statistics, or even seize control over the network. This approach is called the "sinkhole" and is widely used in anti-virus practices. To test the hypothesis that a botnet running on the Mac OS X platform exists, on April 3, 2012, Doctor Web experts registered a number of BackDoor.Flashback.39 control servers domains. Nobody had expected at that time to detect the biggest ever botnet for Mac OS X, given the high reliability and architectural features of this operating system that ensure relative safety for users. However, the reality surpassed all expectations: during the very first hours, Doctor Web-controlled servers recorded activities of more than 130,000 bots; by the morning, their number reached 550,000, and control centres just ceased to process the load. On April 4, 2012, Doctor Web published a press release to announce the discovery of the BackDoor.Flashback.39 botnet. This was a real bombshell announcement, being quoted by many authoritative world news agencies and other media within just 24 hours.
Two simple conditions must be met for a system to get infected with BackDoor.Flashback.39: Java Virtual Machine must be installed in the system, and a user must load a compromised webpage in the browser. These are specifically designed malicious webpages, and compromised resources which virus writers have access to. Malicious code on such a web page loads a Java applet. The applet exploits a Java vulnerability and saves an executable and a .plist file responsible for its launching on the hard drive of the Apple computer. After that, the applet transfers the saved configuration file to the launchd service that allows it to run the Trojan without user intervention. In fact, users notice nothing at all — they are viewing webpages in their browsers while their Macs are already infected with malware.
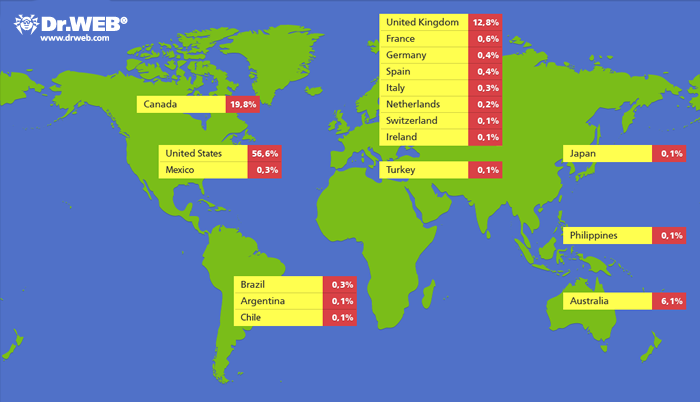
Initially, Doctor Web had information only about some part of botnet that used the modified BackDoor.Flashback Trojan, but already on April 16 additional domains whose names are generated based on the date were registered. Since those domains are used by all the BackDoor.Flashback.39 subversions, the registration of additional domains for control servers allowed to more accurately estimate the malicious network size. Most infected computers reside in the United States (56.6% of infected hosts), Canada comes second (19.8% of infected computers), the third place is taken by the United Kingdom (12.8% infection cases), and Australia with 6.1% is the fourth.
On April 4, 2012, Apple released an update to Java to fix a vulnerability used by the BackDoor.Flashback Trojan. However, if a computer has already been infected before, the update does not protect a user from malware. Shortly afterwards, the number of infected Macs exceeded 800,000. In spite of this, just a few days later, numerous computer security experts reported a significant reduction in the number of BackDoor.Flashback.39 hosts. The joy turned to be premature though: Doctor Web conducted an investigation and found out that there had been an unfortunate error in the experts' calculations.
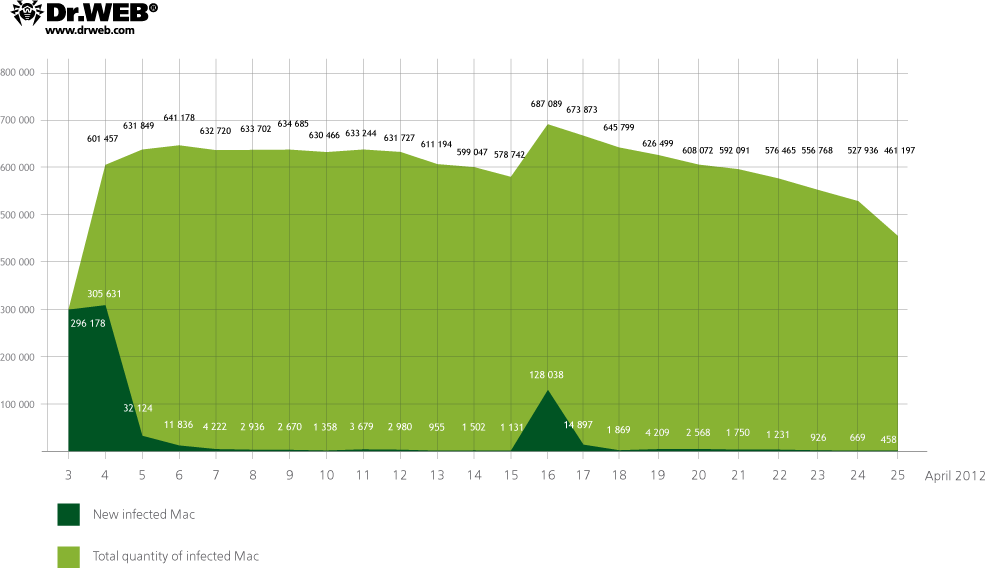
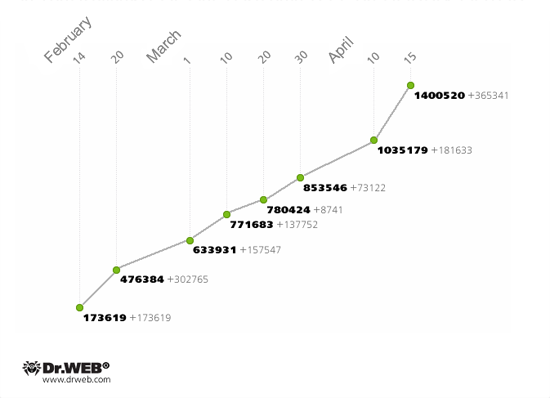
BackDoor.Flashback.39 uses a sophisticated routine to generate control server names: a larger part of the domain names is generated using parameters embedded in the malware resources, others are created using the current date. The Trojan performs sends consecutive queries at the generated addresses according to its pre-defined priorities. The main domains for BackDoor.Flashback.39 command servers were registered by Doctor Web at the beginning of April, and bots first send requests using these names. However, after communicating with servers controlled by Doctor Web, Trojans send requests to the server at 74.207.249.7, controlled by an unidentified third party. This server communicates with bots but doesn't close a TCP connection. As the result, bots switch to the standby mode and wait for the server's reply and, as a consequence, they do not communicate with other command centers, many of which have been specially registered by information security experts. That is why different anti-virus companies delivered contradictory statistics — on the one hand, Symantec and Kaspersky Lab claimed a significant reduction in the number of bots, while on the other hand, data provided by Doctor Web consistently pointed to a significantly larger number of infected computers, with a very weak trend to reduce. The real BackDoor.Flashback.39 growth progress is presented on the chart below:
As of April 28, 2012, the BackDoor.Flashback.39 network had a total of 824,739 bots registered, 334,592 of which were active.
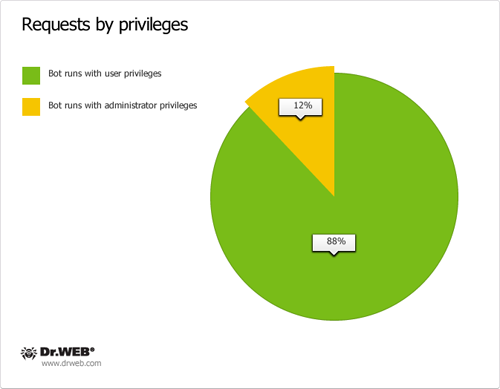
A file that is downloaded by the BackDoor.Flashback.39 Trojan on infected computers is of particular interest. This malicious application can be run with administrator privileges or an ordinary user (at the time the payload is applied, the Trojan displays a dialog box for the administrator password to be entered on a Mac screen) and utilizes two types of control servers. Servers belonging to the first group intercept web search traffic and redirect a user to malicious sites controlled by criminals. The second group issues commands to bots to perform backdoor tasks in the compromised system. Doctor Web analysts managed to take over control server domain names known to BackDoor.Flashback payload malware and analyse requests sent by bots to servers.
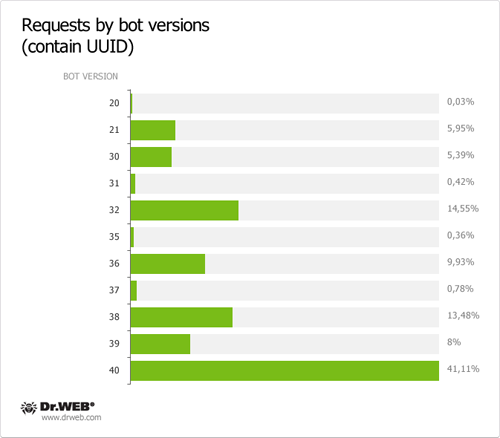
The first group of control domains is generated using the list found in its configuration data; in addition, another domain name list is generated where resulting names are determined by the current date. The second level domain name is the same, while a top-level domain name can be org,. com,. co.uk,. cn,. in. The Trojan horse sends consecutive requests to control servers according to its generated list. An /owncheck/ or /scheck/ GET request sent to a server contains the infected Mac's UUID in the useragent field. If the reply contains a SHA1 hash value of the domain name, this domain will be considered as trusted and from the moment on will be used as a command server name. First domains in this category have been successfully taken over by Doctor Web since April 12, 2012.
Once the malicious program has determined a domain of the first category, it begins to search for a second type domain. The bot uses the list found in its configuration data to send the /auupdate/ GET-request to a number of control servers. The useragent field in these requests contains detailed information on the infected system. If the control server does not return a correct reply, the Trojan uses the current date to generate a string that serves as a hash tag in a search using the address http://mobile.twitter.com/searches?q = # <string>. If the Trojan manages to find a Twitter message containing bumpbegin and endbump tags enclosing a control server address, it will be used as a domain name. Doctor Web began to take over domains of this category on April 13, but on the following day, Saturday, April 14, the Twitter account registered by Doctor Web analysts for this purpose was blocked.
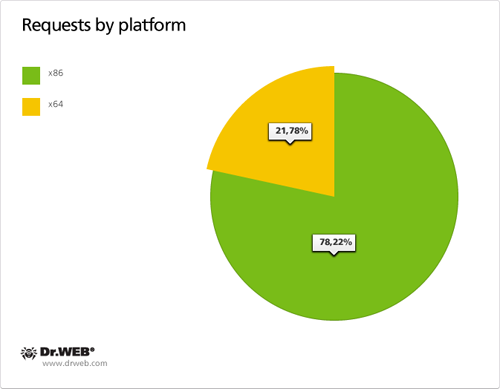
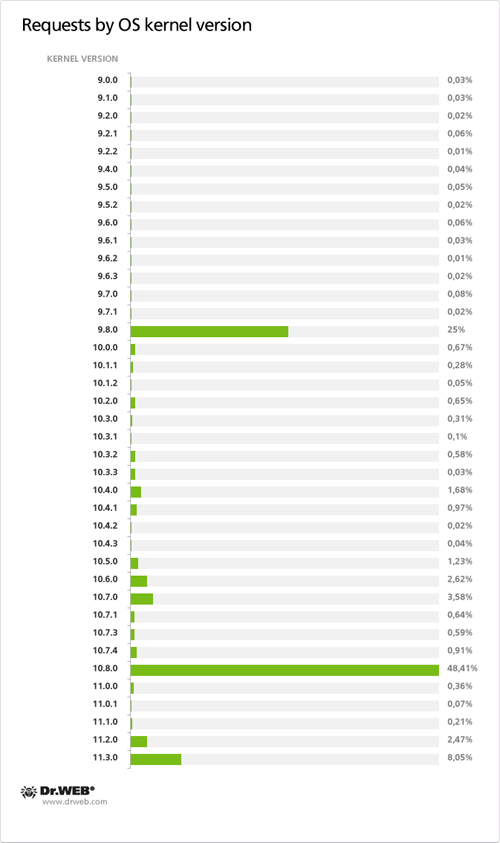
As of April 13, 2012, 30,549 requests containing a UUID were sent to control servers of the first domain name category in 24 hours and 28,284 requests containing a UUID were transmitted to control servers of the second domain name category in the same period of time. Total 95,563 requests containing a UUID were sent to servers meant to control BackDoor.Flashback payload from April 12 till 26, 2012. Below are graphs showing statistics gathered by Doctor Web experts. The data are based on the analysis of daily hits of the BackDoor.Flashback botnet payload to the control server on April 13, 2012.
Shortly after the BackDoor.Flashback was detected, Doctor Web created a special information websitededicated to this threat. On this online resource, owners of Apple-compatible computers can scan their Macs for infection. On the same resource, you can find additional materials and a video presentation on the BackDoor.Flashback Trojan, as well as links to a free scanner for Mac OS X that allows you to scan the operating system and delete the Trojan, if detected. Doctor Web is keeping a close eye on any further developments.
Meet Rmnet — another botnet
According to statistics available to Doctor Web, one of the leading places among threats that infect Microsoft Windows workstations, is now occupied by the Win32.Rmnet.12 file virus. The virus spreads in various ways, in particular, by exploiting browser vulnerabilities that enable intruders to save and launch executables upon loading webpages. The virus searches for all html files stored on disks and embeds VBScript code into them. Besides, Win32.Rmnet.12 infects all executable files with the .exe extension found on the disks, and is able to replicate itself to removable flash drives. It saves an autorun file and a shortcut to a malicious application into the root folder. This application, in its turn, launches the virus.
Win32.Rmnet.12 is a complex multicomponent virus consisting of several modules and capable of self-replication. One of the virus components is a backdoor. Once launched, it tries to determine the Internet connection speed by sending requests to google.com, bing.com and yahoo.com every 70 seconds and analysing responses. Then Win32.Rmnet.12 launches an FTP server on the infected machine, connects to a command center and transmits information about an infected computer. The backdoor can execute commands received from the remote server, in particular, to download and run arbitrary files, update itself, to take screenshots and send them to criminals, and even render the operating system non-operational.
Another virus component steals passwords fstored by the most popular FTP-clients, such as Ghisler, WS FTP, CuteFTP, FlashFXP, FileZilla, Bullet Proof FTP and others. This information can later be exploited to carry out network attacks or to place various malicious objects on remote servers. Also, Win32.Rmnet.12 takes care to search through user's cookies, so attackers can gain access to the user's accounts at different websites that require authentication. In addition, the module can block access individual sites, and redirect the user to a site controlled by virus writers. One of the Win32.Rmnet.12 modifications is also able to make web injections to steal bank account information.
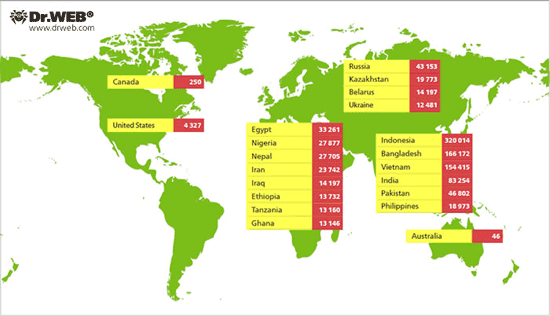
The botnet comprised of hosts infected with Win32.Rmnet.12 was discovered by Doctor Web as long ago as back in September 2011; soon afterwards, control server names stored in the Win32.Rmnet.12 resources were decrypted. After a while, experts analysed the protocol used for communication between bots and control servers which enabled them to determine the number of bots in the network and to control them. On February 14, 2012, Doctor Web's virus analysts succesfully implemented a technoque known as the sinkhole, it was subsequently used to study the BackDoor.Flashback.39 botnet. Namely, they registered domain names for several servers controlling one of the Win32.Rmnet.12 networks and gained full control over that botnet. In late February, another Win32.Rmnet.12 subnet was hijacked this way. Quantatitive dynamics of the botnet controlled by Doctor Web specialists are shown in the chart below.
The greatest number of infected PCs is located in Indonesia comprising 320,014 infected machines, or 27.12%. Bangladesh rates second with 166,172 infected hosts which constitute 14.08% of the botnet size. The third rank is taken by Vietnam (154,415 bots, or 13.08%), followed by India (83,254 bots, or 7.05%), Pakistan (46,802 bots, or 3.9%), Russia (43 153 infected machines, or 3.6%), Egypt (33,261 hosts, or 2.8%), Nigeria (27,877 bots, or 2.3%), Nepal (27,705 bots, or 2.3%) and Iran (23,742 bots, or 2.0%). A sufficiently large number of compromised hosts is found in Kazakhstan (19,773 cases of infection, or 1.67%) and the Republic of Belarus (14,196 bots, or 1.2%). 12,481 compromised hosts, or 1.05% of the total number of Win32.Rmnet.12 bots are located in the Ukraine. A relatively small number of infected computers reside in the U.S. – 4,327 machines, which corresponds to 0.36%. The smallest numbers of compromised hosts are found in Canada (250 computers, or 0.02% of the network's bulk) and Australia (only 46 computers). One infected computer has been found in each of Albania, Denmark, and Tajikistan. Win32.Rmnet.12 botnet geography is shown below.
Encryptors to conquer Europe
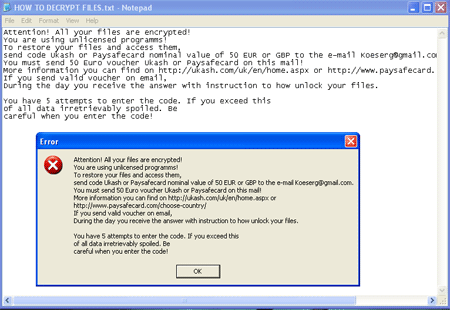
In April, Europeans had also to face troubles: approximately in the middle of the month, Doctor Web anti-virus lab began to receive reports from foreign users who have suffered from encoder Trojans, and first of all, the Trojan.Encoder.94 malware. Like other encoders of this family, Trojan.Encoder.94 searches for user's files, in particular, Microsoft Office documents, music, photos, images and archives on disks available in the infected system, and encrypts them. Once user files are encrypted , the Trojan displays a demand to pay 50 euros or pounds to criminals via Ukash or Paysafecard.
The Trojan features the English interface, but infections have been registered in Germany, Italy, Spain, England, Poland, Austria, Norway, Bulgaria and other countries. Soon afterwards, alarm reports from residents of Brazil, Argentina and other countries in Latin America started to arrive. The Trojan spread through Europe, including such countries as Croatia, Switzerland, Netherlands, Slovenia and Belgium, France, Hungary and Romania. Doctor Web's engineers managed to decrypt data for virtually all users' requests which indicates the high efficiency of technologies employed for this purpose.
In late April, a spike distribution of e-mail messages bearing the title "Ute Lautensack Vertrag Nr 46972057" and the attached zip archive with the name of Abrechnung or Rechnung was recorded. Archives contain the Trojan.Matsnu.1 Trojan. Trying to run it leads to the encryption of all the files on the victim's computer disks. Doctor Web experts have analysed Trojan.Matsnu.1 in the shortest time and developed a special utility that allows user data to be decoded. Download this utility for free from ftp://ftp.drweb.com/pub/drweb/tools/matsnu1decrypt.exe. Remember that if you fell victim to an encoder Trojan, follow these simple guidelines:
- Never attempt to solve the problem by reinstallling the operating system.
- Do not delete any files from the heard drives.
- Do not try to restore the encrypted data on your own.
- Contact Doctor Web's anti-virus laboratory and submit a ticket in the Request for curing section. This service is provided free of charge.
- Attach a file encrypted by the Trojan to the ticket.
- Wait for a response from a virus analyst. Due to the large number of requests it may take some time.
To minimize the damage from an infection by Trojan.Encoder.94 and Trojan.Matsnu.1 Doctor Web recommends users to timely back up all the files they need for their work.
Other "April highlights" and virus threats
Compared to what has been described above, all the other information security threats identified and neutralized by Doctor Web experts in April 2012 do not look that sensational and are significantly less dangerous to users. For example, Trojan.Spambot.11349 description has been added to the the virus databases. This malware is designed to steal email client accounts (in particular, from Microsoft Outlook and The Bat!) and transfer data used by the Autocomplete forms feature in web browsers, to attackers. The Trojan spreads over well-known Backdoor.Andromeda botnets.
The Trojan.Spambot.11349 consists of two components: Delphi-based loader and DLL, which contains a payload. Loader application functions are in general common for this kind of malware: it bypasses a firewall and installs malicious library into the system. Once the library is loaded into an infected computer memory, it takes control of the PC.
Having control of the PC, the library checks for its own copy on the disk, and writes a value of nine random digits that serves as a unique identifier for the bot, to the system registry. Then the Trojan.Spambot.11349 saves a library to work with SSL, and a zlib library, with which the Trojan compresses its request lines, on the disk. At the same time, the HOST field of requests sent by the bot contains a foreign IP address, which is a characteristic feature of the Trojan.Spambot.11349. Using a separate dynamic link library to work with zlib and SSL is not also common for malware architectures.
One of the distinguishing features of the Trojan.Spambot.11349 is that this malware sends a sequence of requests to random IP addresses selected by a special algorithm from a list of subnets stored in the Trojan resources. After that, the Trojan.Spambot.11349 establishes a connection to one of three control servers whose addresses are stored encrypted in the library body, and waits for the configuration file to be received from the server. In case of success, the Trojan creates a request line containing stolen credentials for Microsoft Outlook and The Bat! e-mail clients, packs them with the zlib library and transfers them to a remote server belonging to the attackers. After infecting the system, the Trojan.Spambot.11349 checks the possibility to send spam from an infected computer, sending an e-mail message that contains a random set of characters. If the check is successful, the Trojan retrieves data from a remote server for subsequent spamming. As of April 24, the Trojan.Spambot.11349 Trojans sent out emails that contained advertisements for Viagra.
New threats to the Android mobile operating system also appeared in the past month. Hence, in early April, a family of Android.Gongfu malware was replenished with a new malware instance. An updated modification of the Android.Gongfu was found simultaneously in multiple applications, which were distributed via unofficial software resources. In particular, this Trojan was discovered in a modified Angry Birds Space distribution.
Unlike early Android.Gongfu implementations, new versions do not use the Android vulnerability which would allow them to get root privileges in the system without user intervention. Instead, the infected application comes with a step-by-step manual describing how to run the OS with administrator privileges. The manual claims that it is necessary for normal operation of the program and its updating. When launched with administrator privileges Android.Gongfu is able to inject its code into Android system processes including those critical to stable operation of the OS. The Trojan is able not only to convey information about the infected device to criminals and run commands from a remote server, but also covertly download and install other applications.
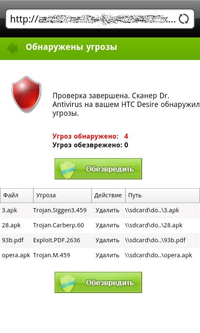
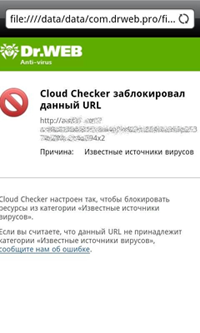
In addition, virus writers specialized on mobile platforms began to use the new psychological ploy to spread malicious software — namely, users' concerns about security issues. With the help of various systems that display advertising, attackers show a message for the user to urgently scan a mobile device for viruses. By clicking on this advertising message, the user gets to a site that allegedly scans a mobile device. This site imitates one of the Dr.Web Security Space 7.0 icons and the program appearance. However, by simulating the user interface, the attackers made a mistake in the details: a fake "anti-virus" finds a non-existent threats on a mobile device, such as Trojan.Carberp.60 that belongs to the category of banking Trojans for the Windows, whereas its mobile version does not currently exist. If the user agrees to "neutralize" the threat the Android.SmsSend family Trojan is downloaded to its device.
 |
 |
 |
 |
All these threats can be successfully detected and neutralized by the Dr.Web anti-virus software, but users are still advised to be careful and not to run programs obtained from unreliable sources.
Malicious files detected in mail traffic in April
| 01.04.2012 00:00 - 30.04.2012 23:00 | ||
| 1 | Trojan.Fraudster.261 | 1.30% |
| 2 | SCRIPT.Virus | 1.11% |
| 3 | Trojan.Fraudster.256 | 0.92% |
| 4 | Trojan.Carberp.30 | 0.76% |
| 5 | Trojan.Fraudster.252 | 0.70% |
| 6 | Trojan.Mayachok.1 | 0.67% |
| 7 | Win32.HLLW.Shadow | 0.67% |
| 8 | Win32.HLLW.Shadow.based | 0.65% |
| 9 | JS.IFrame.233 | 0.61% |
| 10 | Tool.InstallToolbar.74 | 0.61% |
| 11 | Trojan.SMSSend.2726 | 0.59% |
| 12 | JS.Siggen.192 | 0.59% |
| 13 | Trojan.Fraudster.292 | 0.54% |
| 14 | Adware.Predictad.1 | 0.53% |
| 15 | Win32.HLLW.Autoruner.59834 | 0.53% |
| 16 | Trojan.SMSSend.2669 | 0.49% |
| 17 | BackDoor.Ddoser.131 | 0.49% |
| 18 | Trojan.Carberp.29 | 0.48% |
| 19 | Adware.Downware.179 | 0.47% |
| 20 | Win32.HLLW.Autoruner.5555 | 0.47% |
Malicious detected on users' computers in April
| 01.04.2012 00:00 - 30.04.2012 23:00 | ||
| 1 | SCRIPT.Virus | 0.97% |
| 2 | Trojan.Fraudster.261 | 0.97% |
| 3 | Trojan.Fraudster.256 | 0.75% |
| 4 | Trojan.SMSSend.2726 | 0.67% |
| 5 | JS.Siggen.192 | 0.65% |
| 6 | Trojan.Fraudster.292 | 0.63% |
| 7 | Trojan.Mayachok.1 | 0.61% |
| 8 | Trojan.Carberp.30 | 0.59% |
| 9 | Win32.HLLW.Shadow.based | 0.55% |
| 10 | Trojan.SMSSend.2704 | 0.55% |
| 11 | Trojan.Fraudster.252 | 0.53% |
| 12 | Win32.HLLW.Shadow | 0.53% |
| 13 | Tool.InstallToolbar.74 | 0.51% |
| 14 | Adware.Predictad.1 | 0.49% |
| 15 | Win32.HLLW.Autoruner.59834 | 0.49% |
| 16 | Tool.Unwanted.JS.SMSFraud.10 | 0.47% |
| 17 | Trojan.SMSSend.2669 | 0.47% |
| 18 | JS.IFrame.233 | 0.47% |
| 19 | Adware.Downware.179 | 0.45% |
| 20 | BackDoor.Ddoser.131 | 0.45% |