July 3, 2017
The most notable event of the first summer month is an outbreak of Trojan.Encoder.12544, the new encryption worm that is also known as Petya, Petya.A, ExPetya, and WannaCry-2 in some media sources. This malicious program has infected computers of numerous companies and individuals in different countries. In June, Doctor Web security researchers examined two new malicious programs for Linux. One of them installs a cryptocurrency-mining application on the devices it infects, and the other runs a proxy server. In mid-June, one more mining Trojan has been detected, but in this case it has posed a threat to Windows users. Also, in June, several new malicious programs for Android have been detected.
Principal Trends in June
- Outbreak of the encryption worm Trojan.Encoder.12544
- Distribution of the mining Trojan for Windows
- Detection of new malicious programs for Linux
Threat of the month
On the morning of June 27, first reports on a spread of a dangerous encryption worm have appeared. Mass media dubbed it Petya, Petya.A, ExPetya and WannaCry-2. Doctor Web security researchers named it Trojan.Encoder.12544. In reality, this malicious program doesn’t have much in common with the Trojan Petya (Trojan.Ransom.369): they are similar only in the procedure of file table encryption. The Trojan infects computers by exploiting the same vulnerabilities exploited by cybercriminals during the WannaCry attack. Trojan.Encoder.12544 receives a list of local and domain users authorized on the infected computer. Then it searches for network folders available for writing, tries to open them using the obtained account data and save its copy there. Some researchers claimed that creation of the perfc file in the Windows folder is enough to prevent the encoder from launching, but it is not. Indeed, the worm checks its second launch according to availability of a file with a name matching the Trojan’s name without the extension in the system folder. However, if cybercriminals change the original Trojan’s name, creating the file C:\Windows\perfc (as many anti-virus developers advise) will not save a computer from infection. In addition, the Trojan checks the existence of the file only if it has enough privileges to do so.
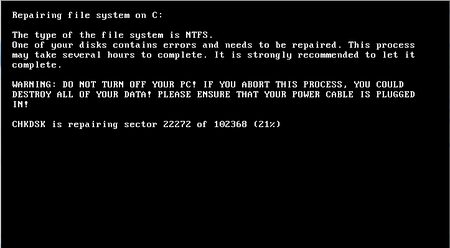
Trojan.Encoder.12544 damages VBR (Volume Boot Record), encrypts the original Windows boot record using the XOR algorithm, then copies it to another disc partition and replaces with its own. Then it creates a task for restart and encrypts files on the fixed computer disks. After the computer is rebooted, on the screen of the infected computer, the worm displays a text similar to the CHDISK standard tool’s text.
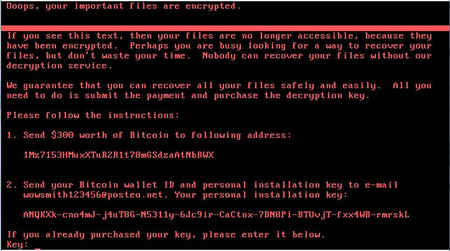
Meanwhile, Trojan.Encoder.12544 encrypts the MFT (Master File Table). Once Trojan.Encoder.12544 completes the encryption, it displays a ransom demand on the screen.
Doctor Web security researchers believe that in the first place Trojan.Encoder.12544 was developed not to demand ransom but to destroy infected computers: firstly, cybercriminals used only one email for contacts and it was blocked soon after the outbreak. Secondly, the key displayed on the screen of the infected computer is a random set of symbols that has nothing in common with the real encryption key. Thirdly, the key sent to cybercriminals doesn’t have anything in common with the key used for encryption of the file allocation table, so cybercriminals have no chance to provide a victim with the key for disk decryption. Details on the operating routines of Trojan.Encoder.12544 can be found in the news article or technical description.
The Trojan first began spreading from an update system of the program MEDoc—a popular tax accounting software in Ukraine. Doctor Web specialists have already encountered malicious programs that spread the same way. Back in 2012, our security researchers detected a targeted attack on drugstores and pharmaceutical companies that involved the use of BackDoor.Dande. It stole medication procurement information from special programs used in the pharmaceutical industry. The Trojan was downloaded from http://ws.eprica.ru. This website belonged to “Spargo Tekhnologii” and was designed to update ePrica, a program for monitoring of medication prices. You can learn more about this incident in our news article, and details of the investigation are in the technical description.
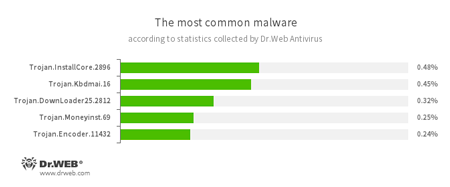
According to Dr.Web Anti-virus statistics
- Trojan.InstallCore
A family of installers of unwanted and malicious applications - Trojan.Kbdmai.16
An adware Trojan. One of the functions of this malicious program is to open different websites in the browser window. - Trojan.DownLoader
A family of malicious programs designed to download other malware to a compromised computer. - Trojan.Moneyinst.69
A malicious program that installs various software, including other Trojans, on a victim's computer. - Trojan.Encoder.11432
A network worm that launches a dangerous ransomware Trojan on a victim’s computer. It is also known as WannaCry.
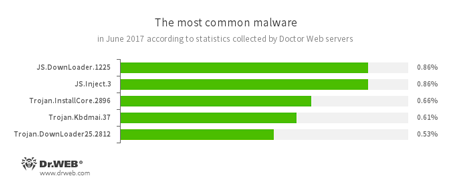
According to Doctor Web’s statistics servers
- JS.DownLoader
A family of malicious JavaScripts. Download and install malicious software. - JS.Inject.3
A family of malicious JavaScripts. They inject a malicious script into the HTML code of web pages. - Trojan.InstallCore
A family of installers of unwanted and malicious applications - Trojan.Kbdmai.37
An adware Trojan. One of the functions of this malicious program is to open different websites in the browser window. - Trojan.DownLoader
A family of malicious programs designed to download other malware to a compromised computer.
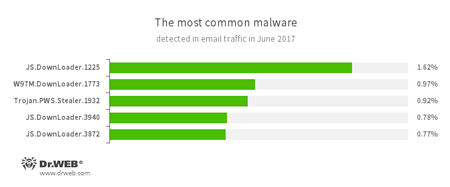
Statistics concerning malicious programs discovered in email traffic
- JS.DownLoader
A family of malicious JavaScripts. Download and install malicious software. - W97M.DownLoader
A family of downloader Trojans that exploit vulnerabilities in office applications. Designed for downloading other malware to a compromised computer. - Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
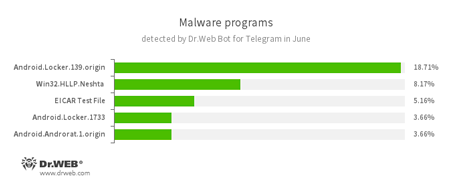
According to Dr.Web Bot for Telegram data
- Android.Locker.139.origin, Android.Locker.1733
Ransomware Trojans for Android. They can lock a device after alleging via an on-screen warning that the device owner has done something illegal. To unlock the device, the owner has to pay a ransom. - Win32.HLLP.Neshta
A file virus known to security researchers since 2005. It infects EXE PE files no less than 41472 bytes in size. During the infection process, it writes itself at the start of the infected file, and the original start is moved to the end of the file. It contains the following string: «Neshta 1.0 Made in Belarus». - EICAR Test File
A special text file designed to test an anti-virus’s efficiency. Upon detecting this file, anti-virus scanners should react in exactly the same way as if the file were a virus. - Android.Androrat.1.origin
A spyware program for Android devices.
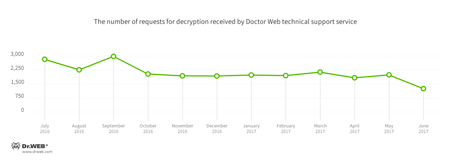
In June, Doctor Web’s technical support service was most often contacted by victims of the following modifications of encryption ransomware:
- Trojan.Encoder.858 — 28.51% of requests;
- Trojan.Encoder.10103 — 8.10% requests;
- Trojan.Encoder.567 — 5.54% of requests;
- Trojan.Encoder.11432 — 4.10% requests;
- Trojan.Encoder.10144 — 2.36% requests;
Dr.Web Security Space for Windows protects against encryption ransomware
During June 2017, 229,381 URLs of non-recommended sites were added to the Dr.Web database.
| May 2017 | June 2017 | Dynamics |
|---|---|---|
| + 1,129,277 | + 229,381 | - 79.68% |
Linux malware
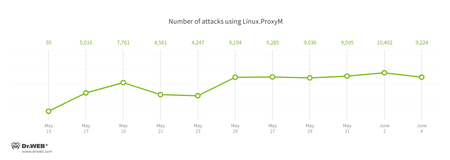
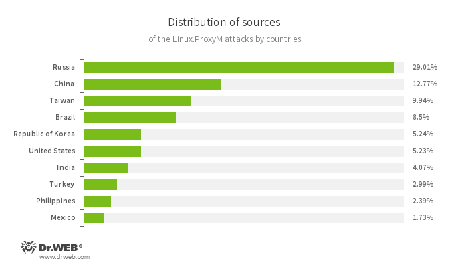
In June, Doctor Web security researchers examined two Trojans for Linux. One of them was Linux.MulDrop.14. It attacks only Raspberry Pi minicomputers. The Trojan is a script containing a compressed and encrypted application designed to mine cryptocurrency. The second Trojan, added to the virus databases as Linux.ProxyM, attacked users beginning in February 2017 but peaked in late May. Doctor Web specialists have pinpointed the activity of the Linux.ProxyM attacks in the below chart:
A significant portion of the attacked IP addresses is located in Russia. In second place is China, and in third place—Taiwan. The below illustration shows the geographical locations from which Linux.ProxyM attacks have been launched:
More information about this malicious program can be found in an article published by Doctor Web.
Other information security events
Malicious programs that use the computing resources of infected devices to mine cryptocurrency emerged soon after the appearance of cryptocurrency: the first Trojan from this family dubbed Trojan.BtcMine was added to the Dr.Web virus databases in 2011. Trojan.BtcMine.1259, which was detected in June, is yet another representative of this malicious family. Trojan.BtcMine.1259 is designed to mine the Monero (XMR) cryptocurrency. Trojan.DownLoader24.64313 downloads it to a computer. This loader Trojan is distributed via the backdoor DoublePulsar.
In addition to engaging in its main function, Trojan.BtcMine.1259 decrypts and loads into the memory a library that is a modified version of a remote administration system with open source code. This system is known as Gh0st RAT (Dr.Web Anti-virus detects it as BackDoor.Farfli.96). Using this library, cybercriminals can control an infected computer and execute various commands. The module that mines Monero (XMR) can load up to 80% of an infected machine’s computing sources with calculations. The Trojan contains both 32- and 64-bit versions of the miner. Which implementation of the Trojan is used on an infected computer depends on the bitness of its operating system. More information about this malicious program can be found in a news article published by Doctor Web.
Malicious and unwanted programs for mobile devices
In June, Doctor Web security researchers detected Android.Spy.377.origin which was attacking Iranian mobile device users. This malicious program sent cybercriminals confidential information and could execute their commands. Also, in June, Doctor Web specialists found new riskware programs on Google Play that are designed to help users connect to the “VK” and “Odnoklassniki” websites which are blocked in Ukraine. These applications, added to the Dr.Web virus database as Program.PWS.1, used an anonymizing server to bypass access restrictions and did nothing to protect transmitted user data.
Also in the past month, such Trojans as Android.SmsSend.1907.origin and Android.SmsSend.1908.origin were distributed via Google Play. They sent SMS to premium numbers and subscribed users to expensive services. In addition, signatures for Trojans of the Android.Dvmap family were added to the virus database. These malicious applications tried to gain root access, infected system libraries, installed additional components, and, when commanded by cybercriminals, were able to download and run software without user knowledge.
One more Android Trojan, detected in June, was named Android.Encoder.3.origin. It was designed to target Chinese users. Once it infected mobile devices, it encrypted files on the SD card and demanded a ransom for their decryption.
Among the most notable June events related to mobile malware, we can mention:
- The detection of an Android Trojan that spied on Iranian users;
- The detection of new threats on Google Play;
- The distribution of an encoder Trojan that encrypted SD card files and demanded a ransom for their restoration.
Find out more about malicious and unwanted programs for mobile devices in our special overview.