June 28, 2017
Trojan.Encoder.12544 poses a serious threat to Windows-running computers. Various sources call it a modification of the Trojan known as Petya (Trojan.Ransom.369); however, Trojan.Encoder.12544 only slightly resembles that Trojan. This malicious program has infected the information systems of government institutions, banks, and commercial organizations. It has also infected user computers in several countries.
At the moment, it is known that the Trojan has infected computers by exploiting the same vulnerabilities exploited by cybercriminals during the WannaCry attack. The spread of Trojan.Encoder.12544 started on the morning of June 27. Once launched on an attacked computer, the Trojan employs several methods to search for available computers in the local network. Then, the Trojan starts scanning ports 445 and 139. Once machines with open ports are found, Trojan.Encoder.12544 attempts to infect them via a widely known SMB protocol vulnerability (MS17-10).
In its body, the Trojan contains four compressed resources. Two of these resources are 32-bit and 64-bit versions of the Mimikatz tool, which is designed to intercept passwords of open Windows sessions. Depending on an operating system’s capacity, the Trojan unpacks the necessary version of the Mimikatz tool, saves it to a temporary folder, and runs the Mimikatz tool. Using Mimikatz and some other methods, Trojan.Encoder.12544 obtains the list of local and domain users authorized on the infected computer. The Trojan then looks for network folders available for writing, attempts to open them using the received data, and saves its copy in these folders. To infect the computers to which it has received access, Trojan.Encoder.12544 uses the PsExec tool, which is designed for remote computer management, or a standard console tool to call the Wmic.exe objects.
The encoder checks its second launch using a file it saved to the C:\Windows\ folder. The file name matches the Trojan’s name, without the extension. Since the worm sample spreading at the moment is named perfc.dat, the file preventing its launch is C:\Windows\perfc. However, if cybercriminals change the original Trojan’s name, creating the file C:\Windows\perfc (as many anti-virus developers advise) will not save a computer from infection. In addition, the Trojan checks the existence of the file only if it has enough privileges to do so.
Once launched, the Trojan sets its privileges, loads its copy to the memory, and grants the copy control. Then, the encoder overwrites its own file with the trash data and removes the file. First, Trojan.Encoder.12544 damages the VBR (Volume Boot Record) of the C drive, and the first drive sector is filled with the trash data. Then, the encoder copies the original Windows boot record encrypted with the XOR algorithm to another part of the drive and overwrites the original record with its own boot record. Then it creates a task to reboot the computer and starts encrypting all the files with the following extensions: .3ds, .7z, .accdb, .ai, .asp, .aspx, .avhd, .back, .bak, .c, .cfg, .conf, .cpp, .cs, .ctl, .dbf, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .kdbx, .mail, .mdb, .msg, .nrg, .ora, .ost, .ova, .ovf, .pdf, .php, .pmf, .ppt, .pptx, .pst, .pvi, .py, .pyc, .rar, .rtf, .sln, .sql, .tar, .vbox, .vbs, .vcb, .vdi, .vfd, .vmc, .vmdk, .vmsd, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xvd, and .zip.
The Trojan encrypts files only on the fixed drives. The data on each drive is encrypted in a separate thread. The files are encrypted using the AES-128-CBC algorithm; a separate key is created for each drive (a characteristic feature of the Trojan that has not been noted by other specialists). This key is encrypted with the RSA-2048 algorithm (other researchers say that an 800-bit key is used) and is saved to the file named README.TXT to the root folder of the system drive. An additional extension is not added to the encrypted files.
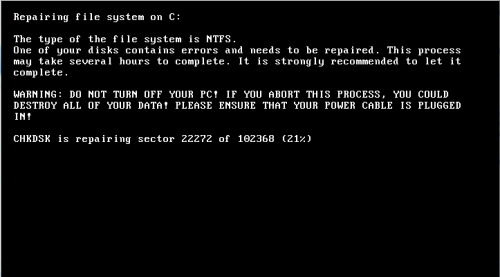
After the computer is rebooted according to the created task, control is granted to the Trojan boot record. On the screen of the infected computer, it displays a text similar to the CHDISK standard tool’s text.
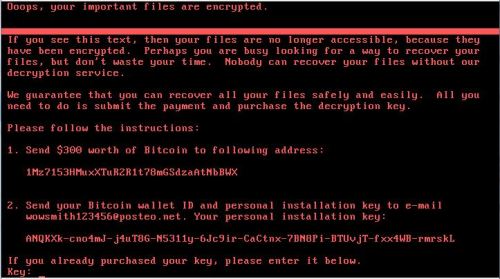
Meanwhile, Trojan.Encoder.12544 encrypts the MFT (Master File Table). Once Trojan.Encoder.12544 completes the encryption, it displays a ransom demand on the screen.
Power down your computer immediately if you see the CHDISK text at system startup. In this case, the boot records will be damaged, but they can be repaired using the Windows recovery tool or Recovery Console if you boot the computer using the distribution disk. Normally, recovery of the boot record is possible in Windows 7 and later operating systems if the hidden portion containing the critical data backup copy is present on the drive. You can also use Dr.Web LiveDisk; create a boot disk or a boot USB, start the operating system from this boot removable media, run the Dr.Web scanner, check the infected drive, and choose the Neutralize action for the detected threats.
According to some sources, the only email address used by the cybercriminals behind Trojan.Encoder.12544 is blocked. That’s why the cybercriminals cannot communicate with their victims (to offer to decrypt files, for example).
To avoid infection by Trojan.Encoder.12544, Doctor Web recommends that you create backup copies of all of your critical data on independent, removable media and use the Data Loss Prevention feature of Dr.Web Security Space. In addition, it is recommended that you install all the security updates for your operating system. Meanwhile, Doctor Web specialists will continue examining Trojan.Encoder.12544.

![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments