April 3, 2017
The beginning of spring was marked by intense activity on the part of cybercriminals involved in Internet scams and the distribution of malicious software. Moreover, in March a Trojan for Linux, designed to mount DDoS attacks, was detected. On Google Play, Doctor Web security researchers detected a program with an embedded module that displayed annoying ads on screens of Android devices. At least 50 million users have already installed this application. In addition, during the first month of spring, numerous potentially dangerous Internet resources were added to the database of non-recommended websites.
Principal Trends in March
- The appearance of a new Trojan for Linux
- The detection of numerous fraudulent websites
- The distribution of aggressive advertising modules and Trojans targeting the Android OS
Threat of the month
Linux malware usually downloads other Trojans onto an infected device, sets up a proxy server, or mounts DDoS attacks. A Trojan detected by Doctor Web security researchers in March that was subsequently named Linux.DDoS.117 executes that last task.
This malicious program has versions for the following architectures: Intel x86, M68K, MIPS, MIPSEL, SPARC, SH4, Power PC, and ARM. Once launched, Linux.DDoS.117 waits for an Internet connection, and when one appears, it sends the attackers information about the infected device. The Trojan can receive commands and execute them using the command interpreter SH. With the help of a special command, cybercriminals send the name of the attacked host and the duration data of the DDoS attack to the Trojan. More detailed information about Linux.DDoS.117 can be found in the technical description of this malicious program.
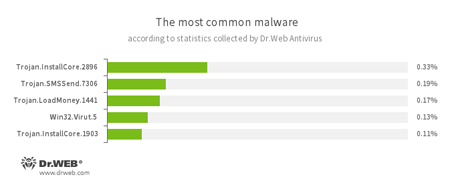
According to Dr.Web Anti-virus statistics
- Trojan.InstallCore
A family of installers of unwanted and malicious applications. - Trojan.SMSSend.7306
A representative of a family of malicious programs that usually take the form of an archive with an embedded installer. The malware prompts the user to either send a message to a short premium service number in order to proceed with the installation and thereafter gain access to the contents of the archive, or indicate a phone number and enter a code received in an incoming message, thus confirming agreement to the terms of a paid subscription. The main “specialization” of Trojan.SMSSend is ransom. - Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer. - Win32.Virut.5
A complex polymorphic virus that infects executable files and contains functions that allow infected computers to be controlled remotely.
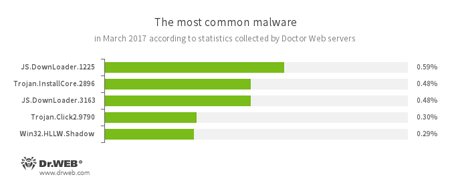
According to Doctor Web statistics servers
- JS.DownLoader
A family of malicious JavaScripts. Download and install malicious software. - Trojan.InstallCore
A family of installers of unwanted and malicious applications. - Trojan.Click2.9790
A Trojan from a family of malicious programs designed to generate traffic for various websites. Such Trojans redirect user requests to the corresponding webpages by controlling the browser. - Win32.HLLW.Shadow
A worm that replicates itself through removable media and network drives. In addition, it can be spread via a network using a standard SMB protocol. It can download executable files from the command and control server and run them.
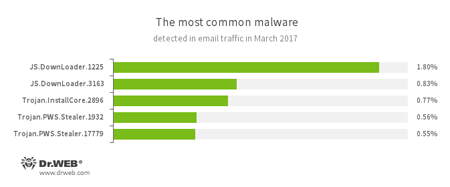
Statistics concerning malicious programs discovered in email traffic
- JS.DownLoader
A family of malicious JavaScripts. Download and install malicious software. - Trojan.InstallCore
A family of installers of unwanted and malicious applications. - Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
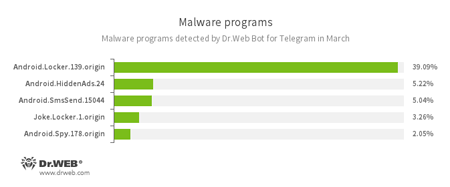
According to Dr.Web Bot for Telegram data
- Android.Locker.139.origin
A ransomware Trojan for Android. It can lock a device after alleging via an on-screen warning that the device owner has done something illegal. To unlock the device, the owner has to pay a ransom. - Android.HiddenAds.24
A Trojan designed to display unwanted ads on mobile devices. - Android.SmsSend.15044
A Trojan belonging to the family of malicious programs that are designed to send SMS messages to premium numbers and subscribe users to chargeable services and services providing paid content. - Joke.Locker.1.origin
A joke program for Android that blocks a mobile device’s screen and displays the Windows BSOD (“Blue Screen of Death”). - Android.Spy.178.origin
A Trojan for Windows that steals confidential information, including user passwords.
Encryption ransomware
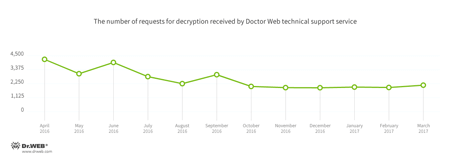
In March, Doctor Web’s technical support was most often contacted by victims of the following modifications of encryption ransomware:
- Trojan.Encoder.858 — 26.71% requests;
- Trojan.Encoder.3953 — 5.89% requests;
- Trojan.Encoder.10144 — 2.83% requests;
- Trojan.Encoder.761 — 2.60% requests;
- Trojan.Encoder.567 — 2.09% requests.
At the beginning of March, a user of the bleepingcomputer.com forum published a link to the list of private keys used by the Dharma ransomware Trojan. According to Doctor Web classification, this is Trojan.Encoder.3953. This is already the second case of the private keys for this encoder being leaked. Once encrypted by this Trojan, files are appended with a suffix containing an email address of the cybercriminals and the following extensions: .xtbl, .CrySiS, .crypted, .crypt or .lock. Thanks to the fact that the keys were leaked, Doctor Web security researchers—as early as March 2—were able to develop a decryption method for files encrypted by Trojan.Encoder.3953.
Also in March, Doctor Web’s specialists created a decryption algorithm for data encrypted by Trojan.Encoder.10465. The malicious program is written in Delphi and appends the extension .crptxxx to infected files. For more information about this encoder and recommendations as to what its victims can do, please refer to this article.
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows.
| Data Loss Prevention | |
|---|---|
 |  |
During March 2017, Doctor Web added 223,173 URLs into the Dr.Web database of non-recommended sites.
| February 2017 | March 2017 | Dynamics |
|---|---|---|
| + 134,063 | + 223,173 | + 66.46% |
In March, Doctor Web security researchers detected more than 500 fraudulent websites aimed at owners and administrators of Internet resources. Many of them received an email claiming to be from Yandex with an offer to improve their website rankings in Internet search results. It contained a link to a page containing a payment form for the offered service.
This offer was common fraud: after paying, victims did not get what was promised. Cybercriminals created more than 500 such pages and distributed them over several leased online media sites.
Malicious and unwanted programs for mobile devices
In March, Doctor Web specialists found a new advertising module on Google Play that was dubbed Adware.Cootek.1.origin. It was embedded in a program called TouchPal, which operates as an on-screen keyboard. After this application was installed, Adware.Cootek.1.origin displayed several types of annoying advertisements; for example, it created unremovable widgets and embedded banners in the lock screen. In addition, it displayed ads on mobile devices right after they were unlocked.
The most noticeable March event related to mobile malware:
- An application with an aggressive, embedded advertising module was detected on Google Play.
Find out more about malicious and unwanted programs for mobile devices in our special overview.