Windows blockers and banners in web browsers
If you look at the graph showing how browser blockers (Trojan.BrowseBan) and blockers of Windows (Trojan.Winlock) spread in March, you will see that they got to where they were in mid October and November 2009. However, the weekly graph shows the number of detections remaining around 10 000 on a daily bases which roughly amounts to 100 000 infected systems per week.
In March Doctor Web received over 100 unique screenshots of blockers via its user technical support system. Since cases when a user can take a screenshot in the infected systems are very rare, the total number of processed support requests related to the subject is much higher.
 |
 |
Blockers remain one of the most common issues in user support requests for several reasons. First of all, it is quite difficult to get rid of such species of malware since they hamper any user activity in the system and secondly these are malicious programs whose activities are meant to be noticed. While most malicious programs operate covertly, Doctor Web strongly recommends all users of Dr.Web products contact the technical support service immediately if they think that they have even an indirect evidence of an active infection in the system.
Botnet communicates over Microsoft Word
Trojan.Oficla is a malware underworld specimen that allows owners of botnets created by means of this program to hide in a system as a Microsoft Word process if the latter is installed on the computer.
Authors of Trojan.Oficla sell new modifications of the program to other criminals so that they create new botnets that operate all over the world.
As zombies in any other botnet, machines compromised by Trojan.Oficla are fully controlled by the botnet’s owner and can download other malicious programs from a server belonging to criminals, install and launch downloaded malware.
Doctor Web’s statistics server registered around 100 000 detections of this malicious program in one week of March 2010. Trojan.Oficla spreads with e-mail messages and exploits vulnerabilities of web browsers. It can also take advantage of other spreading channels. The choice here is determined by imagination of the botnet’s owner.
Invisible banker
Trojan.PWS.Ibank is another piece of malware that doesn’t attract users’ attention while at work. Its numerous modifications retrieve account details of customers of large banks in Russia. Trojans exploit vulnerabilities of banking software used by clients to carry out transactions over the Internet.
Retrieved account information is sent to criminals. Trojan.PWS.Ibank also operates as a key logger.
Trojan.PWS.Ibank spreads in surges. A rapid growth of the number of its detections that dropped again within 24 hours was registered several times in March.
Fake anti-viruse
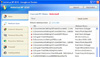
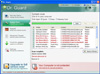
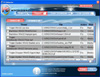
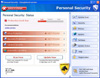
By the end of March an inflow of support requests regarding fake Russian online anti-viruses has practically stopped. However, traditional representatives of this malware family (Trojan.Fakealert) infect user systems with the number of detections of such programs remaining steady 30 millions per month.
Methods used to spread fake anti-viruses have been honed through years and remain the same. Yet appearance of such malware does change. Fake anti-viruses tend to look more and more like popular IT security solutions spread using social engineering techniques.
Trojan.Fakealert screenshots
File encoder
The March was also marked by discovery of several new modifications of Trojan encoders that demanded over USD 50 from a user willing to get his data back.
Trojan.Encoder.67 encrypted all files except for files located in certain system directories that sometimes might render a system non-operational and even itself from actually displaying a ransom demand message.
Trojan.Encoder.68 compromised only files of certain types. It placed target files in password-protected ZIP archives. The password consisted of 47 symbols and was unique for each infected system. Doctor Web offered users free access to a web-form where they could generate passwords to extract their files.
Tools required to counter an.Encoder.68 programs can be found on the special web-page of Doctor Web’s site devoted to free anti-virus tools.
In March the share of malicious code in mail traffic increased by 22% compared with February while the share of malicious code among files scanned on users machines reduced by 24%. These fluctuations are insignificant since the overall share of malware from the total number of scanned objects remained the same as in February.
Malicious programs detected in mail traffic in March
| 01.03.2010 00:00 - 01.04.2010 00:00 | ||
| 1 | Trojan.DownLoad.41551 | 15495381 (14.11%) |
| 2 | Trojan.DownLoad.37236 | 13614045 (12.39%) |
| 3 | Trojan.DownLoad.47256 | 10053104 (9.15%) |
| 4 | Trojan.Botnetlog.zip | 7267927 (6.62%) |
| 5 | Trojan.MulDrop.40896 | 7103001 (6.47%) |
| 6 | Trojan.Fakealert.5115 | 7029855 (6.40%) |
| 7 | Trojan.Packed.683 | 5753224 (5.24%) |
| 8 | Trojan.Fakealert.5238 | 5266296 (4.79%) |
| 9 | Trojan.DownLoad.50246 | 4054874 (3.69%) |
| 10 | Trojan.Fakealert.5825 | 3445424 (3.14%) |
| 11 | Trojan.Fakealert.5437 | 2519370 (2.29%) |
| 12 | Trojan.Fakealert.5356 | 2283687 (2.08%) |
| 13 | Trojan.Fakealert.5784 | 1974861 (1.80%) |
| 14 | Trojan.PWS.Panda.122 | 1852731 (1.69%) |
| 15 | Trojan.Fakealert.5229 | 1836702 (1.67%) |
| 16 | Trojan.Fakealert.5457 | 1609146 (1.46%) |
| 17 | Trojan.Siggen.18256 | 1527888 (1.39%) |
| 18 | Trojan.Packed.19694 | 1517178 (1.38%) |
| 19 | Trojan.MulDrop.46275 | 1463124 (1.33%) |
| 20 | Trojan.Fakealert.11956 | 1369146 (1.25%) |
| Total scanned: | 30,331,944,880 |
| Infected: | 109,851,515 (0.36%) |
Malicious programs detected on user machines in March
| 01.03.2010 00:00 - 01.04.2010 00:00 | ||
| 1 | Win32.HLLW.Gavir.ini | 773623 (6.35%) |
| 2 | BAT.Generic.184 | 576696 (4.73%) |
| 3 | Trojan.Fraudster.36 | 501271 (4.12%) |
| 4 | Trojan.WinSpy.641 | 472955 (3.88%) |
| 5 | Trojan.AntiAV.6 | 428431 (3.52%) |
| 6 | Trojan.WinSpy.616 | 410484 (3.37%) |
| 7 | Trojan.WinSpy.640 | 409803 (3.36%) |
| 8 | Win32.HLLW.Shadow.based | 406787 (3.34%) |
| 9 | Trojan.DownLoad.32973 | 371322 (3.05%) |
| 10 | Win32.HLLM.Xgray.3 | 361513 (2.97%) |
| 11 | VBS.Sifil | 351449 (2.89%) |
| 12 | BAT.310 | 310476 (2.55%) |
| 13 | IRC.Apulia.1215 | 289792 (2.38%) |
| 14 | Trojan.WinSpy.570 | 266963 (2.19%) |
| 15 | Trojan.AuxSpy.111 | 249772 (2.05%) |
| 16 | Win32.HLLP.Jeefo.36352 | 198323 (1.63%) |
| 17 | Trojan.PWS.Ibank.28 | 191114 (1.57%) |
| 18 | ACAD.Pasdoc | 184475 (1.51%) |
| 19 | Trojan.PWS.Ibank.25 | 174119 (1.43%) |
| 20 | Win32.HLLW.Shadow | 148909 (1.22%) |
| Total scanned: | 88,035,683,471 |
| Infected: | 12,181,429 (0.01%) |




![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments