Doctor Web discovers new version of Android.Loki Trojans that infects system libraries
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
December 9, 2016
The Trojan, dubbed Android.Loki.16.origin, is a multi-component malware program that covertly downloads and installs software on Android devices. The infection process involves several steps.
First, other malicious programs download and run Android.Loki.16.origin on a mobile device. Then the Trojan connects to a command and control server and downloads the additional component Android.Loki.28; it also downloads several exploits so that it can get root privileges. All the files are stored in the Trojan’s folder. Android.Loki.16.origin executes the exploits one by one, and once its privileges have been elevated, it runs the module Android.Loki.28.
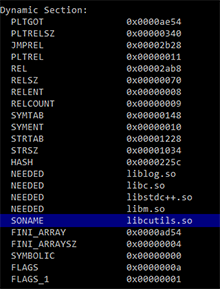
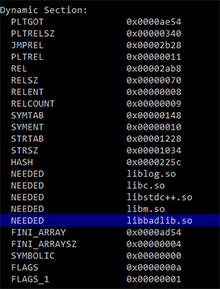
Once launched, Android.Loki.28 mounts the section /system so that a writing process can make changes to system files. It then extracts the additional malicious components Android.Loki.26 and Android.Loki.27 from its body and saves them to the system catalogs /system/bin/ and /system/lib/, respectively. The Trojan then injects a dependency from Android.Loki.27 into one of the system libraries. Once the library is modified, Android.Loki.27 ties itself to it and is run every time the operating system uses the library. Figures below show an example of changes performed by the Trojan:
Once Android.Loki.27 starts operating, it runs Android.Loki.26 solely from system processes that use root privileges. Thus, Android.Loki.26 acquires elevated permissions and can covertly download not only malware programs, but also advertising modules and benign applications, generating illegal income from advertising and increasing download statistics.
Since Android.Loki.27 modifies system components, its deletion can render a device non-operational. When switched on again, the Android operating system won’t boot up normally because it won’t be able to find the dependency from the Trojan in the modified library. For the device to work normally again, its firmware has to be updated, a process that will delete all personal files. Before performing the update, the device owner should create back-up copies of all their important data and, if possible, contact a technical support specialist.
Dr.Web for Android successfully detects all the known Trojans belonging to the Android.Loki family, so they do not pose any threat to our users.