Doctor Web presents overview of IoT-oriented Linux Trojans
Real-time threat news | Hot news | All the news | Virus alerts
October 17, 2016
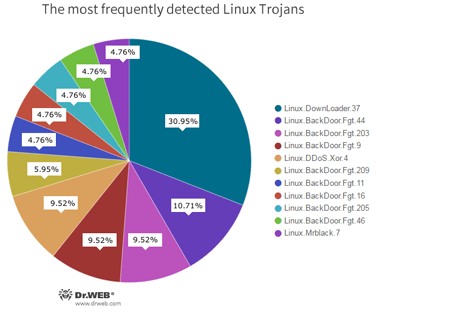
Currently, the virus makers spreading Trojans for the IoT are mostly concerned with creating botnets to carry out DDoS attacks. Nevertheless, some Trojans are implemented to make a proxy server from an infected device. Since mid-September 2016, Doctor Web’s specialists have registered 11,636 attacks by Linux Trojans—9,582 of them were performed over the SSH protocol; and 2,054—over the Telnet protocol. Cybercriminals installed 15 different malware programs, the majority of which belong to the Linux.DownLoader, Linux.DDoS, and Linux.BackDoor.Fgt families. The round diagram below shows the proportional relationship between the most frequently detected Linux Trojans.
Judging from these statistics, Linux.Downloader.37 is the most popular malware program designed to perform DDoS attacks. Among other Linux Trojans, there are representatives of the Linux.Mrblack, Linux.BackDoor.Gates, Linux.Mirai, Linux.Nyadrop, Perl.Flood, and Perl.DDoS families, which are also intended to carry out DDoS attacks. A large number of different modifications of Linux.BackDoor.Fgt were registered on infected devices as well. In addition, versions of these Trojans exist for the MIPS, SPARC, m68k, SuperH, PowerPC, and other architectures. Linux.BackDoor.Fgt can also perform DDoS attacks.
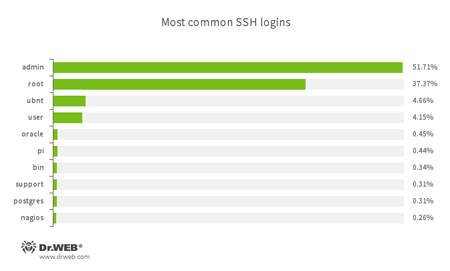
Cybercriminals download all these Trojans to devices after they have cracked the login credentials and established a connection over the Telnet or SSH protocol. Attackers use the login “root” if they want to establish a connection via the Telnet protocol; and the login “admin” if they are using the SSH protocol:
The table below shows some standard combinations of the logins and passwords used by attackers to hack Linux devices.
| SSH | ||
|---|---|---|
| Login | Password | Device/application (presumably) |
| Informix | Informix | Family of the Informix relational database management system (RDBMS) developed by IBM |
| Pi | Raspberry | Raspberry Pi |
| Root | Nagiosxi | Nagios Server and Network Monitoring Software |
| nagios | Nagios | Nagios software |
| cactiuser | Cacti | Cacti software |
| root | Synopass | Synology software |
| admin | Articon | ProxySG - Secure Web Gateway by Blue Coat Systems |
| Telnet | ||
| Root | xc3511 | Surveillance cameras |
| Root | Vizxv | Dahua surveillance cameras |
| Root | Anko | Anko surveillance cameras |
| Root | 5up | TP-Link routers |
| Root | XA1bac0MX | CNB surveillance cameras |
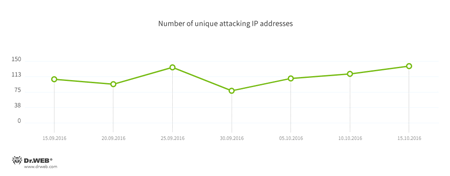
The average number of IP addresses from which cybercriminals attack Linux devices monitored by Doctor Web is 100:
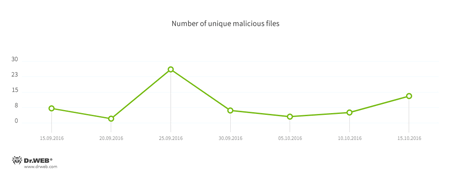
The number of unique malicious files downloaded by cybercriminals to hacked devices varies from just a few to several dozen:
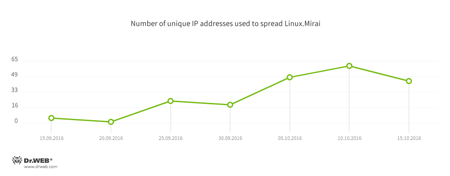
Worth noting are the statistics pertaining to Linux.Mirai downloads to vulnerable devices: once the source code of this Trojan became public, Linux.Mirai’s popularity with virus makers increased dramatically. This fact is illustrated by the growing number of IP addresses from which the malware program is downloaded onto devices:
In October, a Trojan belonging to the Linux.Luabot family was used to spread Linux.Mirai. In the end of September, Doctor Web’s specialists registered attacks involving Linux.Nyadrop.1, which was first spotted by the authors of the MalwareMustDie blog. Judging by the combinations of logins and passwords used during the attacks, we can conclude that the criminals behind the Trojan were partly targeting TP-Link routers. The executable file of Linux.Nyadrop.1 is only 621 bytes in size and is used to install other malware programs on an infected device.
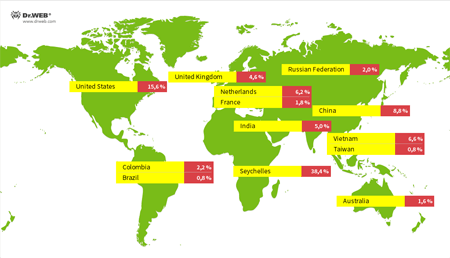
Below you can see the geographical spread of the IP addresses from which malware programs were installed onto Linux devices:
Doctor Web’s specialists are keeping a close watch on the Linux malware landscape and will inform users about new threats in a timely manner.