June 2015 Android malware review from Doctor Web
July 1, 2015
PRINCIPAL TRENDS IN JUNE
- Activity of banking Trojans
- Emergence of new downloader Trojans
- Emergence of new Android ransomware
- Growing number of SMS Trojans
Number of entries for malicious and unwanted software targeting Android OS in Dr.Web virus database
| May 2015 | June 2015 | Dynamics |
|---|---|---|
| 9,155 | 10,144 | +10.8% |
Mobile threat of the month
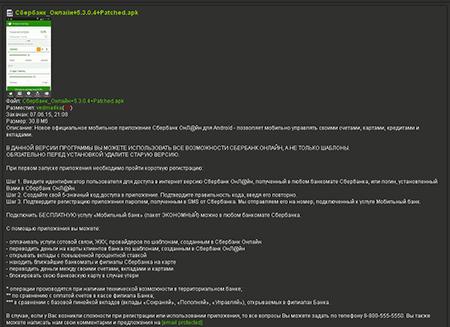
In June 2015, Doctor Web security researchers detected and examined a banking Trojan named Android.BankBot.65.origin that was incorporated into a Sberbank Online mobile application. The modified program was disguised as a new version of its legitimate “colleague” and was distributed through a popular website dedicated to mobile devices.
The compromised copy of an application operates exactly like its original version; so users do not expect the downloaded program to be a malicious one, which puts their confidential data in danger. However, once the application is run, it starts gathering various confidential information that the malware sends to a remote server. The malicious program can also intercept incoming SMS messages upon cybercriminals' command; thus, this fraudulent method can be used to steal money from users' bank accounts. Find out more about Android.BankBot.65.origin in the news article published by Doctor Web.
Banking Trojans for Android
Various banking Trojans that continue to appear with persistent regularity are one of the key threats to Android devices' users. Apart from Android.BankBot.65.origin, other suchlike malicious programs were also quite active during the previous month. In particular, cybercriminals in different countries continued to distribute banking Trojans in unsolicited SMS messages containing a download link for a malware. For example, in Russia, cybercriminals distributed various modifications of Android.SmsBot.291.origin using MMS messages.
 |
 |
 |
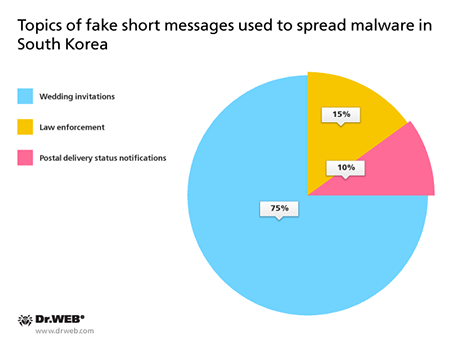
Once again, cybercriminals could not turn their backs on users in South Korea; that is, during the previous month, Doctor Web security specialists detected 20 spam campaigns organized by cybercriminals from this country.
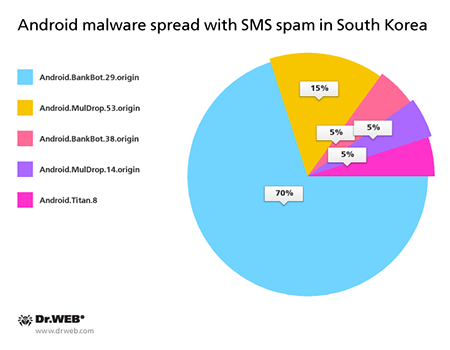
In June, the following malicious programs for Android were distributed via SMS spam messages:
The number of entries for banking Trojans of the Android.BankBot family in Dr.Web virus database:
| May 2015 | June 2015 | Dynamics |
|---|---|---|
| 119 | 122 | +2.52% |
The number of entries for multicomponent Trojans of the Android.SmsSend family in Dr.Web virus database:
| May 2015 | June 2015 | Dynamics |
|---|---|---|
| 378 | 419 | +10.85% |
Android.SmsBot.291.origin
A banking Trojan designed to steal money and remotely controlled by cybercriminals.
Android.BankBot.29.origin
A banking Trojan that steals authentication information used by the clients of some South Korean financial organizations. Once a popular online banking application is launched, the Trojan replaces its interface with a fake one that prompts the user to enter all confidential data necessary to control their bank account. The divulged data is forwarded to cybercriminals. Under the pretext of subscribing the user to a banking service, it attempts to install the malicious program Android.Banker.32.origin.
Android.MulDrop.53.origin
A Trojan designed to distribute and install other malware on Android mobile devices.
Android.MulDrop.14.origin
This Trojan is designed to distribute and install other malware, including various banking Trojans, on Android mobile devices. It is mainly distributed in South Korea.
Android.BankBot.38.origin
This Trojan is designed to steal money from bank accounts of mobile devices' owners.
Android.Titan.8
A dangerous Trojan designed to steal confidential information and execute various intruder-issued commands (for example, make or record calls without the user's knowledge, display different notifications in the status bar, and other commands).
Downloader Trojans
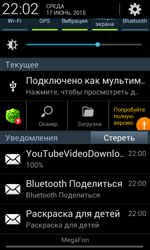
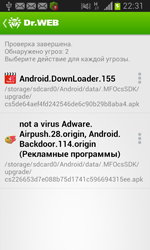
In June, Doctor Web security researchers detected yet another Trojan designed to download other malicious software to mobile devices. The malware named Android.DownLoader.157.origin is disguised as a mobile application, which shows the following information about a conversation partner during a call: country, region, and mobile network operator. However, once the user installs this application, fake SMS notifications that look like real ones will start to appear in the status bar. If such a notification is tapped, some unwanted or malicious program will be downloaded to the victim's device. For more information regarding this Trojan, refer to the news article published by Doctor Web.
|
 |
The number of entries for Trojans of the Android.DownLoader family in Dr.Web virus database:
| May 2015 | June 2015 | Dynamics |
|---|---|---|
| 279 | 310 | +11.11% |
Android ransomware
Trojans belonging to the Android.Locker family continue to present a threat to Android devices' users. These programs lock handhelds and demand a ransom to unlock them. During the previous month, Dr.Web virus database was updated with a number of new entries for these Trojans.
| May 2015 | June 2015 | Dynamics |
|---|---|---|
| 266 | 301 | +13.16% |
SMS Trojans
During the first summer month, new SMS Trojans belonging to various families were detected. These malicious applications send messages to premium numbers and subscribe users to chargeable services without their victims' knowledge or consent.
The number of entries for SMS Trojans of the Android.SmsSend family in Dr.Web virus database:
| May 2015 | June 2015 | Dynamics |
|---|---|---|
| 4,204 | 4,745 | +12.9% |